Application modernization is crucial for businesses to adapt to evolving technologies and market demands. This process often involves dealing with legacy systems, presenting unique challenges. The Strangler Fig pattern offers a strategic approach to incrementally modernize applications, preserving existing functionality while introducing new capabilities. This methodology allows for a controlled transition, minimizing disruption and maximizing the return on investment.
This document delves into the intricacies of the Strangler Fig pattern, examining its core principles, implementation steps, and considerations for successful modernization projects. We’ll explore various application modernization strategies, highlighting the benefits and limitations of each approach. The document also addresses crucial aspects such as security, compliance, monitoring, and planning, enabling a comprehensive understanding of the process.
Introduction to Application Modernization
Application modernization is the process of enhancing, upgrading, or transforming existing applications to leverage current technologies and architectures. This often involves migrating legacy systems to more modern platforms, improving performance, enhancing security, and increasing scalability. The objective is to maintain or improve application functionality while reducing technical debt and improving overall operational efficiency.This transformation is crucial for businesses seeking to adapt to evolving market demands, improve competitiveness, and enhance user experience.
Modernization efforts are often driven by the need to reduce costs associated with maintaining legacy systems, increase operational efficiency, and ensure continued application functionality in the face of changing technological landscapes.
Motivations Behind Application Modernization
Businesses embark on application modernization projects for a variety of compelling reasons. These include the desire to reduce operational costs, improve application performance, enhance security, and increase scalability. Legacy systems, often developed with older technologies, can become increasingly difficult and expensive to maintain over time. Modernizing these systems can lead to significant cost savings in the long run, freeing up resources for more strategic initiatives.
Furthermore, modernization projects can address security vulnerabilities inherent in older systems, safeguarding sensitive data and improving overall system resilience.
The Role of Legacy Systems in Modernization
Legacy systems, while often crucial to a company’s past success, often present significant challenges in the modern era. These systems may be built on outdated technologies, lacking the flexibility and scalability required for current business needs. They may also present security vulnerabilities that are difficult and expensive to address. However, legacy systems contain valuable business logic and functionality, and a successful modernization strategy must carefully consider how to retain this knowledge while migrating to newer platforms.
The goal is not to abandon the past, but to build on it in a way that maximizes the return on investment in existing systems.
Common Challenges in Application Modernization
Modernization projects are often complex and face various obstacles. These challenges can include the high cost of migration, the potential for data loss or corruption, and the need to ensure seamless integration with existing systems. The sheer complexity of legacy systems, often with undocumented codebases and unclear functionalities, can also create hurdles. Successful projects require careful planning, a deep understanding of the existing system, and a thorough approach to testing and validation.
Legacy System Feature, Modernization Need, and Potential Solution
| Legacy System Feature | Modernization Need | Potential Solution |
|---|---|---|
| Outdated programming language (e.g., COBOL) | Maintenance costs are high and skilled developers are scarce. | Migrate to modern languages (e.g., Java, Python) with automated code conversion tools. Employ cloud-based solutions for easier scaling and management. |
| Lack of security features | Vulnerabilities expose sensitive data to potential threats. | Implement security best practices, including encryption and access controls. Employ security testing and penetration testing to proactively address potential risks. |
| Limited scalability | Inability to handle increasing data volumes and user traffic. | Migrate to cloud-based platforms or microservices architecture for increased scalability and flexibility. Implement load balancing and caching strategies to optimize performance. |
| Poorly documented code | Understanding the system’s logic and functionality is challenging. | Invest in code documentation and refactor existing code to improve readability. Employ tools for automated code analysis to identify potential issues and improve maintainability. |
Understanding the Strangler Fig Pattern
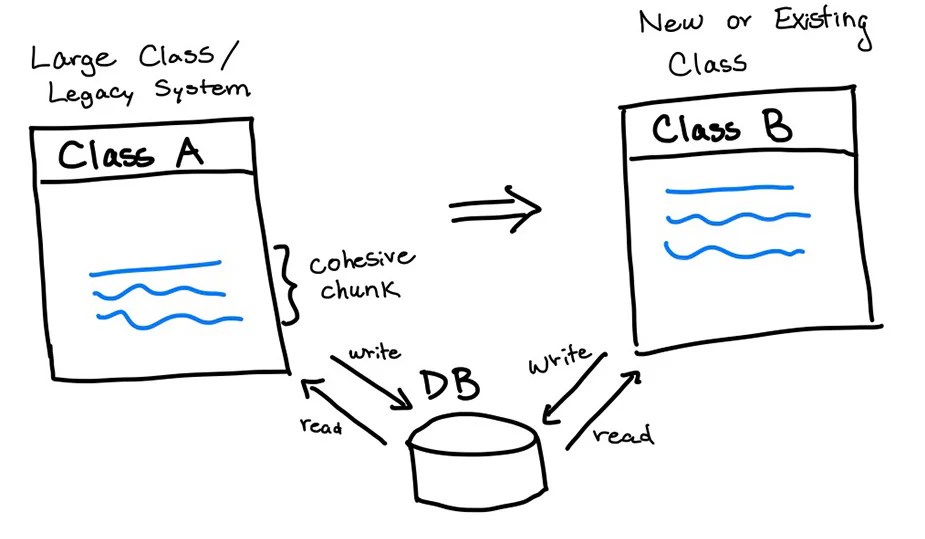
The Strangler Fig pattern is a sophisticated approach to application modernization, specifically designed to manage the complexities of integrating new technologies with existing, legacy systems. It provides a controlled and phased approach to migration, minimizing disruption and maximizing the benefits of modernization. This methodology allows businesses to gradually replace older components with newer ones, preserving the functionality of the existing system while implementing improvements.This pattern, drawing parallels to a strangler fig vine that slowly envelops and replaces a host tree, meticulously replaces legacy components with modern ones.
This approach prioritizes functionality over complete overhaul, enabling organizations to effectively manage the transition.
Core Concept of the Strangler Fig Pattern
The Strangler Fig pattern leverages a gradual replacement strategy. New, modern applications (the “strangler vines”) are developed and deployed alongside the existing legacy system (the “host tree”). These new applications progressively take over functionality, eventually rendering the legacy system redundant and allowing for its decommissioning. Crucially, the new applications often integrate with the existing system through an API layer, allowing for seamless data exchange.
Addressing Legacy System Issues
The Strangler Fig pattern effectively addresses legacy system issues by allowing for a controlled transition. The pattern mitigates risks associated with complete system replacement, which can be disruptive and costly. By introducing new components incrementally, the pattern allows businesses to maintain functionality while gradually upgrading to modern technologies. This gradual approach reduces downtime and minimizes the impact on users.
It’s particularly useful when the legacy system is complex or when the cost of a complete overhaul is prohibitive.
Comparison with Other Modernization Approaches
Compared to other modernization approaches, such as a complete rewrite or a monolithic refactoring, the Strangler Fig pattern offers a more flexible and gradual path. A complete rewrite often entails significant upfront investment and risks of losing functionality. A monolithic refactoring, while preserving the existing architecture, might not be sufficient to achieve significant performance gains. The Strangler Fig approach strikes a balance between these two approaches, allowing businesses to leverage the existing system while introducing new technologies in a controlled and manageable manner.
Key Components and Steps in Implementation
The Strangler Fig pattern involves several key components and steps:
- API Gateway: This component acts as an intermediary between the legacy system and the new applications, allowing the new applications to interact with the legacy system’s functionalities. This crucial layer allows for seamless integration without requiring modifications to the legacy system.
- New Applications: These applications are specifically designed to handle new requirements or replace functionalities within the legacy system. They often use modern technologies and architectures, improving performance and scalability.
- Phased Rollout: The introduction of new applications is typically implemented in phases, allowing for thorough testing and validation of new components before decommissioning older parts of the system. This careful phasing minimizes disruption to the user experience.
- Data Migration: This aspect is critical. Data migration plans are vital to ensure smooth transition and minimize data loss during the replacement process. A well-defined strategy for data migration ensures continuity of operations and prevents significant disruptions.
Benefits and Drawbacks
The Strangler Fig pattern offers several benefits:
- Reduced Risk: The phased approach minimizes the risk of disruption and allows for testing and validation of new components before decommissioning older parts.
- Gradual Adoption: Organizations can gradually adopt new technologies and architectures without requiring a complete overhaul.
- Controlled Transition: The pattern provides a controlled environment for the transition, minimizing the risk of data loss and disruption to existing functionality.
However, the pattern also presents some drawbacks:
- Increased Complexity: The implementation of an API gateway and the coordination of multiple applications can add complexity to the project.
- Longer Implementation Time: The phased approach may result in a longer implementation time compared to a complete rewrite.
- Technical Debt: Maintaining both the legacy system and the new applications simultaneously can introduce technical debt, potentially impacting long-term maintainability.
Comparison: Strangler Fig vs. Microservices
| Feature | Strangler Fig | Microservices |
|---|---|---|
| Architecture | Hybrid, integrates new components with legacy system | Decentralized, independent services |
| Deployment | Phased, incremental | Independent, often deployed concurrently |
| Data Access | Often relies on existing database and API access | May require custom data access layers |
| Testing | Testing is integrated with existing systems | Testing is service-specific |
| Scalability | Scalability of new components; legacy system might not scale as well | Individual services can be scaled independently |
Application Modernization Strategies

Application modernization is a crucial process for organizations aiming to enhance the performance, security, and maintainability of their legacy systems. Choosing the appropriate modernization strategy is critical, as it directly impacts the project’s success and long-term value. Different approaches cater to varying needs and constraints, and careful consideration of these factors is essential for a successful outcome.
Various Modernization Strategies
Different strategies are available for application modernization, each with its own set of advantages and disadvantages. Understanding these strategies is vital for organizations to select the most suitable approach for their specific context. Factors such as the application’s complexity, the desired outcome, and available resources influence the selection process.
Rehosting
Rehosting involves migrating an application to a new platform without changing its core architecture. This approach is often the quickest and least expensive option, particularly when the underlying infrastructure is being upgraded. However, it doesn’t address fundamental issues within the application itself. This strategy is best suited for applications with simple structures and minimal integration requirements.
Re-platforming
Re-platforming involves migrating the application to a different platform, but preserving its original architecture. This strategy often involves replacing the underlying operating system, database, or middleware. While it offers a way to leverage new platform capabilities, it may introduce complexities if the application has intricate dependencies.
Refactoring
Refactoring focuses on improving the internal structure and design of an application without changing its external behavior. This involves code restructuring, optimization, and the introduction of new technologies, aiming to improve maintainability and performance. This strategy is beneficial for applications with significant code complexity or technical debt.
Replatforming
Replatforming is similar to re-platforming, but it goes beyond just replacing the platform. It involves adapting the application to leverage the new platform’s capabilities, often resulting in a more efficient and modern application. This strategy involves architectural adjustments and often leads to significant changes in the application’s structure.
Reengineering
Reengineering involves a complete redesign and rebuilding of the application, often with significant code rewriting. This is the most comprehensive modernization approach, leading to a fundamentally different application with enhanced features and improved performance. It is suitable for applications with outdated architectures, extensive technical debt, or significant security vulnerabilities.
Table Comparing Modernization Approaches
| Approach | Description | Pros | Cons |
|---|---|---|---|
| Rehosting | Migrating to a new platform without architectural changes. | Fast, cost-effective, minimal disruption. | Doesn’t address underlying application issues, limited scalability. |
| Re-platforming | Migrating to a different platform, preserving architecture. | Leverages new platform capabilities, potentially faster than reengineering. | Can introduce complexities due to dependencies, may not fully address technical debt. |
| Refactoring | Improving the internal structure and design. | Improves maintainability and performance, addresses technical debt. | Requires significant effort, may not be suitable for major architectural changes. |
| Replatforming | Adapting to a new platform, leveraging its capabilities. | Modernizes application architecture, improved performance. | More complex than rehosting, potentially higher risk. |
| Reengineering | Complete redesign and rebuilding of the application. | Addresses major issues, improved security, enhanced performance. | Most expensive and time-consuming, highest risk. |
Examples of Modernization Projects
A company migrating its legacy Java application to a cloud-based platform using rehosting. Another company updating its web application using re-platforming to leverage a new framework. A third company modernizing its internal application using refactoring to improve code quality. These are just a few examples of how different modernization strategies are employed.
Best Practices for Choosing a Strategy
Selecting the appropriate strategy involves careful consideration of several factors. Assessing the application’s architecture, complexity, and dependencies is critical. Evaluating the project’s budget, timeline, and available resources is also essential. Understanding the desired outcome and anticipated benefits is crucial for aligning the strategy with the organization’s goals. Thorough planning and risk assessment are essential for successful modernization.
The Strangler Fig Pattern in Action
The Strangler Fig pattern facilitates a smooth transition from legacy systems to modern architectures. This gradual replacement approach minimizes disruption to existing functionalities while simultaneously introducing new capabilities. Careful planning and execution are crucial for success.Implementing the Strangler Fig pattern involves a phased approach, meticulously integrating the new application with the old one. This methodical integration ensures minimal impact on users and existing workflows.
The key is to understand the specific steps and methodologies for incremental replacement.
Implementing the Strangler Fig Pattern
The process of implementing the Strangler Fig pattern involves a series of steps designed to minimize disruption and maximize efficiency. These steps typically follow a methodical sequence.
- Identifying the Target Application: Carefully assess the legacy application’s functionalities and identify the specific modules or functionalities that are candidates for modernization. This analysis helps define the scope of the initial modernization effort.
- Building a New Application: The next step involves designing and developing the new application, incorporating the desired modern features and technologies. This new application should be designed to handle the functionalities targeted for modernization.
- Creating a Proxy: A proxy application acts as an intermediary between the old and new systems. It routes requests to the appropriate system, ensuring seamless operation during the transition. This is a crucial step to ensure that users experience a smooth transition.
- Incremental Replacement: Gradually replace functionalities from the old system with the new one. Start with small, manageable components and progressively expand the scope. This incremental approach reduces the risk of disruption and allows for testing and refinement.
- Monitoring and Optimization: Thoroughly monitor the performance and stability of both the old and new systems. Refine the integration process based on observed data to optimize the transition.
Incremental Replacement of Functionalities
Replacing functionalities incrementally is crucial for minimizing disruption. This strategy involves carefully isolating the specific functionalities to be replaced and gradually shifting the load to the new application. This methodical approach allows for comprehensive testing and validation at each stage.
- Identify Key Functionalities: Start by identifying the functionalities that are most suitable for modernization. These could be components with high maintenance costs, outdated technologies, or functionalities that require significant improvements.
- Design Replacement Strategies: Develop specific strategies for replacing these functionalities. Consider how to map the functionality from the old system to the new system, while maintaining backward compatibility.
- Develop Unit Tests: Create thorough unit tests for each replaced functionality to ensure that the new implementation functions correctly and meets all requirements.
- Phased Rollout: Gradually migrate users from the old system to the new system, ensuring that there are clear guidelines and processes for the rollout. This ensures minimal disruption to ongoing processes.
Integrating the New Application with the Old
A smooth integration between the new and old applications is essential for a successful transition. This involves careful design and implementation of the proxy application.
- Design the Proxy: Design the proxy application to act as a gatekeeper, routing requests to either the old or new application based on the functionality being accessed. This ensures that the appropriate system handles each request.
- Testing the Proxy: Thoroughly test the proxy to ensure that it routes requests correctly and provides a seamless user experience. The testing should cover various scenarios, including normal operations, error conditions, and peak loads.
- Monitoring Integration: Continuously monitor the performance of the integrated system, tracking metrics such as response time, error rates, and user feedback to ensure that the integration is functioning optimally.
Real-World Use Cases
Numerous organizations have successfully leveraged the Strangler Fig pattern. One example is a large e-commerce company that modernized its order processing system. They progressively migrated components to a new, cloud-based system while maintaining the existing system for legacy orders. Another example is a financial institution that modernized its core banking system. This involved gradually replacing functionalities, such as account management, while maintaining access to existing systems.
Phases of Strangler Fig Implementation
| Phase | Activities | Deliverables |
|---|---|---|
| Phase 1: Assessment & Planning | Identify target functionalities, define modernization strategy, create proxy design, and establish monitoring metrics. | Detailed modernization plan, proxy architecture design, and monitoring strategy documentation. |
| Phase 2: Development & Testing | Develop the new application, implement unit tests, integration tests, and performance tests. | Functional new application, comprehensive test results, and a deployment plan. |
| Phase 3: Deployment & Integration | Deploy the new application, integrate with the proxy, and begin incremental replacement. | Deployed new application, integrated proxy, and migrated initial functionalities. |
| Phase 4: Monitoring & Optimization | Monitor system performance, gather user feedback, and refine the integration process. | Performance metrics, user feedback reports, and optimized integration processes. |
Technology Considerations
The Strangler Fig pattern hinges on a careful selection of technologies to ensure a smooth and effective transition. Choosing the right tools allows for seamless integration between the legacy system and the new microservices, minimizing disruption and maximizing efficiency. Understanding the strengths and weaknesses of each technology is crucial to achieving a successful modernization effort.
Technologies Commonly Used
A variety of technologies can be employed in Strangler Fig implementations, each with its own advantages and disadvantages. The choice of technology should be tailored to the specific needs and characteristics of the legacy application and the desired outcome. Key considerations include performance requirements, scalability needs, and data integration strategies.
- Microservices Frameworks: Frameworks like Spring Boot, NestJS, or Laravel facilitate the creation of independent, scalable microservices. These frameworks often support containerization and orchestration, enabling efficient deployment and management.
- Programming Languages: Java, Python, Node.js, and Go are popular choices for developing microservices. The selection depends on existing team expertise, project requirements, and the specific tasks assigned to each service.
- Databases: Relational databases like PostgreSQL or MySQL might be used for some aspects of the legacy system, while NoSQL databases like MongoDB or Cassandra might be better suited for new, microservice-specific data needs. Choosing the right database for each part of the application ensures optimal performance and data management.
- API Gateways: API gateways like Kong or Apigee are often used to manage communication between the legacy system and the new microservices. They act as a central point for routing requests, enforcing security policies, and handling potential performance issues.
- Containerization Platforms: Docker and Kubernetes are essential for packaging and deploying microservices. Containerization allows for consistent environments across development, testing, and production, ensuring reproducibility and stability.
Selection Criteria
Several criteria must be considered when selecting technologies for a Strangler Fig implementation. These include the existing technology stack, team expertise, scalability requirements, security concerns, and maintenance costs.
- Compatibility: The chosen technologies should be compatible with the legacy system’s architecture and existing data structures. Compatibility ensures a smooth transition and avoids unnecessary complexity or disruption.
- Scalability: The technologies must support future scalability requirements, as the new microservices are likely to experience growing demands over time. This involves evaluating the scalability of each technology choice, including potential load balancing mechanisms.
- Maintainability: Consider the ease of maintaining and updating the chosen technologies. A well-maintained system is less prone to errors and can be upgraded more easily in the future.
- Security: Security considerations are paramount. Technologies should adhere to industry best practices and incorporate robust security measures to protect sensitive data and prevent vulnerabilities.
Potential Compatibility Issues
Legacy systems often have unique data formats and communication protocols that can differ significantly from modern standards. These discrepancies can cause compatibility issues during integration with new microservices. Careful planning and thorough testing are vital to address potential challenges.
- Data format discrepancies: Differences in data structures between the legacy system and new services can create issues during data exchange. This often necessitates data transformation and mapping to ensure compatibility.
- API protocol incompatibility: Differences in communication protocols between the legacy system and new services can cause difficulties in integration. This necessitates the use of API gateways or intermediary layers to bridge the gap between systems.
- Security vulnerabilities: Legacy systems may have security vulnerabilities that need to be addressed during the modernization process. Assessing and mitigating these vulnerabilities is critical to ensure the security of the entire system.
Technology Use Cases
The following table illustrates common technologies and their typical use cases in Strangler Fig implementations:
| Technology | Description | Use Case |
|---|---|---|
| Spring Boot | Java-based framework for building microservices | Developing new microservices for application functionality |
| PostgreSQL | Open-source relational database | Storing data for legacy and new application components |
| Docker | Containerization platform | Packaging and deploying microservices consistently |
| Kubernetes | Container orchestration platform | Managing and scaling microservices in production |
| Kong | API gateway | Routing requests, managing security, and handling performance issues |
API Design and Management
Designing and managing APIs is crucial for a successful Strangler Fig implementation. APIs form the communication channels between the legacy system and the new microservices. Well-defined APIs facilitate seamless integration and reduce complexity.
- API design best practices: Applying RESTful principles, defining clear endpoints, and providing well-documented specifications contribute to API usability.
- API versioning: Implementing versioning strategies ensures backward compatibility as new features are introduced. This allows for gradual transitions and minimizes disruptions to existing applications.
- API security: Implementing security measures such as authentication and authorization mechanisms within the API design is essential to protect sensitive data and maintain system integrity.
Security and Compliance
Application modernization, while offering significant benefits, introduces new security considerations. A crucial aspect of any modernization project is the proactive implementation of robust security measures throughout the entire process. Careful planning and execution are paramount to ensure the security and compliance of the modernized application, minimizing risks and adhering to industry standards.
Security Considerations During Modernization
Modernization efforts often involve migrating data and applications to new platforms or technologies. This transition presents unique security challenges, demanding a thorough risk assessment and a proactive security strategy. Vulnerabilities may arise from the integration of new components, the migration process itself, or changes in the application’s architecture. This necessitates a comprehensive security audit and rigorous testing throughout the modernization lifecycle.
Importance of Security Best Practices
Security best practices form the foundation of any successful modernization initiative. Adherence to these practices helps ensure that the modernized application is secure from various threats. This includes employing secure coding practices, implementing access controls, and adhering to industry-standard security frameworks. Examples include OWASP (Open Web Application Security Project) guidelines and NIST (National Institute of Standards and Technology) frameworks.
Security Vulnerabilities and Mitigation Strategies
Modern applications are susceptible to various security vulnerabilities. Understanding potential threats and implementing appropriate mitigation strategies is essential. For instance, insecure APIs, outdated libraries, and insufficient input validation can create entry points for attackers.
Compliance Requirements for Modernized Applications
Modernized applications must comply with relevant industry regulations and standards. Compliance requirements can vary based on the application’s industry and geographic location. Understanding and adhering to these regulations is critical for maintaining operational stability and avoiding penalties. For example, financial institutions must adhere to strict regulations like PCI DSS (Payment Card Industry Data Security Standard).
Security Risks and Mitigation Techniques
The following table Artikels potential security risks during application modernization and their corresponding mitigation strategies.
| Risk | Description | Mitigation |
|---|---|---|
| Insecure API Design | APIs lacking proper authentication, authorization, and input validation. | Employ API security best practices, including rate limiting, input validation, and strong authentication mechanisms. |
| Outdated Libraries | Using libraries with known vulnerabilities. | Regularly update libraries to the latest versions and address any reported security issues promptly. Use dependency management tools. |
| Insufficient Input Validation | Failing to sanitize user inputs, leading to injection attacks (SQL, XSS). | Implement robust input validation mechanisms to prevent malicious code injection and ensure data sanitization. |
| Data Breach | Unauthorized access and exposure of sensitive data. | Implement encryption at rest and in transit. Employ strong access controls, regular security audits, and incident response plans. |
| Unauthorized Access | Gaining access to resources without proper authorization. | Implement role-based access control (RBAC), multi-factor authentication, and regular access reviews. |
Monitoring and Maintenance
Effective monitoring and maintenance are crucial for ensuring the stability and performance of modernized applications, particularly during the transition from legacy to new systems. Proper monitoring allows for early detection of issues, enabling swift resolution and preventing service disruptions. A robust maintenance strategy ensures ongoing support and upgrades for the modernized architecture, safeguarding against unforeseen problems and guaranteeing optimal functionality.Maintaining both the legacy and the new applications requires a holistic approach.
The monitoring strategies should encompass not only the individual components but also the integration points between them, ensuring seamless data flow and optimal performance. This necessitates a proactive approach that anticipates potential problems and implements preventative measures.
Monitoring Strategies for New and Legacy Applications
Monitoring both the new and legacy applications involves different approaches, each tailored to the specific characteristics of the system. For legacy applications, monitoring focuses on key performance indicators (KPIs) that reflect their historical performance patterns. This enables comparison with the new system’s performance metrics, allowing for an assessment of improvements or potential degradations. For new applications, monitoring is centered around their functionality and efficiency, tracking usage patterns, resource consumption, and adherence to performance benchmarks.
Monitoring Integration Points
Monitoring integration points is critical for maintaining data integrity and application functionality. This includes the use of logging, tracing, and performance monitoring tools to track data flow and identify any bottlenecks or errors. Comprehensive monitoring of the interfaces between legacy and new applications ensures smooth communication and data exchange. This continuous monitoring of the integration points is paramount to maintaining seamless application operation and identifying any disruptions early on.
Ongoing Maintenance and Support
Ongoing maintenance and support are essential to ensure that both the legacy and new applications function optimally and remain compliant with evolving business needs. This involves regular updates, bug fixes, and security patches for both sets of applications. This ongoing maintenance must consider the specific maintenance needs of each application and their integration points. A well-defined maintenance schedule, encompassing testing and validation processes, ensures smooth operation and reduces the risk of unexpected failures.
Examples of Monitoring Tools
Various monitoring tools can be employed to track application performance and identify potential issues. Popular choices include New Relic, Datadog, Prometheus, and Grafana. These tools offer different functionalities, ranging from performance monitoring to log analysis. The selection of monitoring tools should align with the specific requirements of the modernization project, considering factors such as scalability, cost, and ease of integration.
Monitoring and Maintenance Flowchart
| Step | Description |
|---|---|
| 1. Define KPIs | Establish key performance indicators (KPIs) for both legacy and new applications, encompassing system performance, resource utilization, and integration points. |
| 2. Implement Monitoring Tools | Select and deploy appropriate monitoring tools, tailored to the specific needs of each application and integration points. |
| 3. Configure Alerts | Configure alerts based on predefined thresholds for KPIs, enabling rapid response to potential issues. |
| 4. Regular Maintenance | Establish a regular maintenance schedule for both legacy and new applications, encompassing updates, bug fixes, and security patches. |
| 5. Continuous Monitoring | Continuously monitor application performance, integration points, and user feedback. |
| 6. Issue Resolution | Proactively address issues identified during monitoring and maintenance. |
Planning and Execution
The successful modernization of applications hinges critically on meticulous planning and execution. A well-defined roadmap, clear communication, and realistic timelines are paramount to achieving desired outcomes while minimizing disruption. This phase ensures the project aligns with business objectives and leverages resources effectively.A strategic approach to application modernization, like the Strangler Fig pattern, necessitates careful planning to avoid unforeseen challenges.
This includes defining clear objectives, identifying key stakeholders, and creating a detailed timeline. Thorough planning fosters a smoother transition and reduces the risk of project delays or cost overruns.
Planning Phase Steps
A comprehensive planning phase is crucial for successful application modernization. It involves several key steps:
- Defining Objectives and Scope: Clearly articulate the business goals for the modernization effort. This includes specific performance improvements, cost reductions, and functionality enhancements. Defining the scope is vital, ensuring that the project stays focused on the essential aspects. This limits scope creep and keeps the project on track.
- Identifying Stakeholders and Assessing Dependencies: Identify all key stakeholders who will be impacted by or involved in the modernization process. Understanding their needs and concerns is crucial for effective communication and buy-in. Assess any dependencies on other systems or teams, and create a plan for mitigating potential conflicts.
- Risk Assessment and Mitigation Planning: Identify potential risks associated with the modernization project, such as technical challenges, security vulnerabilities, and potential disruptions to service. Develop mitigation strategies to address these risks and minimize their impact.
- Resource Allocation and Budgeting: Determine the necessary resources (personnel, budget, tools) required for the modernization project. Develop a detailed budget outlining anticipated costs for various phases, including development, testing, and deployment. This provides clarity and accountability.
- Technology Selection and Vendor Evaluation: Evaluate potential technologies for modernization, considering factors like compatibility, scalability, security, and cost. Assess and evaluate vendors to ensure alignment with project needs and support.
Roadmap Design
A well-structured roadmap is essential for guiding the modernization project. It provides a visual representation of the entire process, from initial assessment to final deployment.
- Phased Approach: Divide the modernization process into distinct phases, such as assessment, planning, development, testing, deployment, and maintenance. This phased approach allows for incremental progress and facilitates management of complexity.
- Key Milestones and Dependencies: Establish clear milestones and dependencies between each phase to ensure smooth progression. Each milestone should have a clear definition of completion, including deliverables and acceptance criteria.
- Contingency Planning: Anticipate potential challenges and develop contingency plans to address them. This includes backup plans for unforeseen technical issues, budget overruns, or delays.
Successful Modernization Projects
Several organizations have successfully implemented application modernization projects using the Strangler Fig pattern. One example involves a financial institution that modernized its core banking system in phases. By carefully selecting the appropriate technologies and using the Strangler Fig pattern, they successfully migrated their application without significant downtime.Another example is a retail company that migrated its legacy e-commerce platform to a cloud-based solution using a Strangler Fig approach.
This allowed them to leverage the scalability and flexibility of the cloud while minimizing disruption to existing operations. These projects highlight the benefits of a phased approach and strategic planning.
Project Timeline
The following table Artikels a potential timeline for an application modernization project using the Strangler Fig pattern. This is a template, and specific timelines will vary based on project complexity and resources.
| Phase | Tasks | Timeline |
|---|---|---|
| Assessment | Requirements gathering, system analysis, risk assessment | 2-4 weeks |
| Planning | Roadmap development, resource allocation, vendor selection | 4-6 weeks |
| Development | New application development, integration | 8-12 weeks |
| Testing | Unit testing, integration testing, user acceptance testing | 4-6 weeks |
| Deployment | Phased deployment, data migration | 2-4 weeks |
| Maintenance | Monitoring, support, updates | Ongoing |
Stakeholder Communication
Effective communication with stakeholders is crucial for gaining buy-in and managing expectations. Regular updates, clear communication channels, and active listening are essential to ensure everyone is aligned.
Strangler Fig and Cloud Migration

The Strangler Fig pattern, while primarily designed for application modernization, proves highly adaptable for cloud migration strategies. Its phased approach allows for a gradual transition to cloud environments, minimizing disruption to existing systems and maximizing the benefits of cloud services. This compatibility hinges on carefully planned refactoring and integration of cloud-native services.The key to successful cloud migration using the Strangler Fig pattern is to leverage its modularity and incremental nature.
This strategy enables a smooth transition to the cloud while maintaining the functionality of existing legacy applications. The pattern’s modularity and incremental nature allows for a phased migration, reducing risks and ensuring operational continuity.
Compatibility of Strangler Fig with Cloud Migration Strategies
The Strangler Fig pattern’s modularity is particularly well-suited for cloud migrations. Each new cloud-based service acts as a “strangler” around a portion of the legacy system, gradually replacing it with a more modern, cloud-optimized component. This gradual replacement facilitates a controlled and manageable migration process. This is especially beneficial when dealing with complex legacy applications that have intertwined dependencies.
Integrating Cloud-Native Applications with Legacy Systems
Cloud-native applications often leverage microservices architectures and containerization technologies. Integrating these with existing legacy systems requires careful consideration of API design and data exchange protocols. Using well-defined APIs facilitates communication between the new cloud-native services and the legacy systems, allowing seamless data flow. This integration can be achieved through API gateways or message queues.
Refactoring Legacy Applications for Cloud Deployments
Refactoring legacy applications for cloud deployments involves identifying modules that can be migrated to cloud-native technologies first. These modules should be selected based on factors such as their complexity, dependency on other systems, and potential for optimization in the cloud environment. The refactoring process should also focus on improving the application’s architecture to better align with cloud principles, such as scalability, resilience, and maintainability.
This is crucial for long-term success in a cloud environment.
Examples of Cloud Migration Using Strangler Fig
A company migrating its customer relationship management (CRM) system to the cloud might use the Strangler Fig pattern. They could start by migrating the customer data entry and management functions to a cloud-based service. Gradually, they would replace other functionalities, such as reporting and analytics, with cloud-native components. This staged approach minimizes the disruption to the existing CRM system while leveraging the benefits of the cloud.
Another example is a company moving their order processing system to the cloud. The company would first migrate the order entry module to a cloud-based microservice, and then progressively replace other modules such as inventory management and shipping with cloud-native components.
Cloud Platform Compatibility with Strangler Fig
| Cloud Platform | Compatibility with Strangler Fig | Strengths | Weaknesses |
|---|---|---|---|
| AWS | High | Extensive range of services, mature ecosystem | Potential for complexity in managing multiple services |
| Azure | High | Strong integration capabilities, good support for hybrid environments | Can have a steeper learning curve for some users |
| Google Cloud | High | Focus on serverless computing and containerization | May have fewer enterprise-level support resources |
This table illustrates the compatibility of various cloud platforms with the Strangler Fig pattern. The table demonstrates the relative ease of implementation and the strengths and weaknesses of each platform. Each platform offers different strengths and weaknesses, which must be considered when choosing a platform for the migration.
End of Discussion
In conclusion, the Strangler Fig pattern presents a compelling strategy for application modernization. By incrementally replacing functionalities and integrating new applications with existing ones, organizations can achieve a seamless transition. This approach effectively addresses the challenges of legacy systems while facilitating a controlled migration to a more modern architecture. Key considerations for successful implementation include thorough planning, robust security measures, and ongoing monitoring and maintenance.
Questions Often Asked
What are the common challenges in application modernization projects?
Common challenges include compatibility issues between legacy and new systems, security concerns during the transition, managing stakeholder expectations, and maintaining operational continuity throughout the process.
How does the Strangler Fig pattern differ from a microservices approach?
The Strangler Fig pattern focuses on gradual replacement, maintaining the functionality of the old system while introducing new features. Microservices, on the other hand, aim for a complete overhaul, decomposing the application into independent, deployable services. The choice depends on the specific needs and constraints of the project.
What are some best practices for choosing the right modernization strategy?
Best practices include thoroughly evaluating the legacy system’s architecture and functionality, assessing the resources available, understanding the business needs and objectives, and carefully planning the implementation steps.
What security considerations should be taken into account during application modernization?
Security considerations include identifying and mitigating potential vulnerabilities in both the legacy and new systems, implementing robust access controls, and ensuring compliance with industry standards and regulations throughout the process.