Understanding what is a tabletop exercise for incident response is crucial in today’s digital landscape, where cyber threats are constantly evolving. These exercises, far from being dry simulations, are dynamic learning experiences designed to enhance an organization’s ability to respond effectively to security incidents. They provide a safe environment for teams to practice, refine, and validate their incident response plans, ultimately strengthening their overall security posture.
This guide explores the core principles of tabletop exercises, from their fundamental objectives and design to the practical steps involved in planning, conducting, and analyzing these valuable training sessions. We will cover everything from defining roles and responsibilities to crafting realistic scenarios and measuring exercise effectiveness. This information will help you to understand the benefits of regular tabletop exercises for any organization.
Defining a Tabletop Exercise (TTX) for Incident Response
Tabletop exercises (TTXs) are essential tools for organizations to enhance their incident response capabilities. They offer a safe and controlled environment to simulate a cybersecurity incident, allowing participants to practice their roles, test existing plans, and identify areas for improvement. This proactive approach helps organizations be better prepared to handle real-world cyberattacks and minimize their impact.
Core Purpose of a Tabletop Exercise in Incident Response
The primary purpose of a tabletop exercise in the context of incident response is to evaluate and improve an organization’s readiness to handle cybersecurity incidents. This involves assessing the effectiveness of incident response plans, policies, and procedures, as well as the skills and coordination of the incident response team. The exercise allows for identification of gaps, weaknesses, and areas where further training or resources are needed.
Concise Definition of a TTX
A tabletop exercise (TTX) is a discussion-based exercise where participants, typically members of an incident response team and relevant stakeholders, meet to discuss a simulated cybersecurity incident. The exercise involves a facilitator presenting a scenario, and participants discussing their roles, responsibilities, and actions according to established incident response plans and procedures. It is a low-stress, non-threatening environment designed for learning and improvement.
Primary Objectives of Conducting a Tabletop Exercise
Conducting a tabletop exercise serves several key objectives, all contributing to a more robust and effective incident response capability. These objectives can be summarized as follows:
- Testing Incident Response Plans and Procedures: TTXs allow organizations to validate their documented incident response plans and procedures. This involves walking through the steps Artikeld in the plan, identifying any ambiguities, inconsistencies, or omissions.
- Improving Communication and Coordination: Exercises facilitate the practice of communication and coordination among different teams and stakeholders involved in incident response, such as IT, security, legal, and public relations. This practice helps improve information sharing and decision-making during an actual incident.
- Identifying Gaps and Weaknesses: TTXs help organizations uncover gaps in their incident response capabilities. This may include missing procedures, inadequate training, insufficient resources, or poorly defined roles and responsibilities.
- Enhancing Team Skills and Knowledge: The exercises provide an opportunity for team members to practice their skills and gain a better understanding of their roles and responsibilities during an incident. This helps build confidence and improve overall team performance.
- Raising Awareness: TTXs increase awareness of cybersecurity threats and the importance of incident response among all participants. This can lead to a stronger security culture within the organization.
- Evaluating Technology and Tools: Tabletop exercises can be used to evaluate the effectiveness of security tools and technologies. Participants can discuss how they would use these tools to detect, analyze, and respond to the simulated incident.
For example, a financial institution might conduct a TTX to simulate a ransomware attack. The exercise would involve the incident response team, IT staff, legal counsel, and public relations representatives. They would discuss how they would detect the attack, contain the damage, eradicate the threat, recover systems, and communicate with customers and the media. The exercise would help the institution identify weaknesses in its ransomware response plan, such as insufficient backup procedures or unclear communication protocols.
This proactive approach can save millions in damages and reputational harm.
Participants and Roles in a TTX
Understanding the roles and responsibilities of participants is crucial for a successful tabletop exercise (TTX). Clearly defined roles ensure that the exercise runs smoothly, allowing participants to focus on the simulated incident and the organization’s response capabilities. The inclusion of diverse stakeholders provides a comprehensive perspective and facilitates a more realistic and valuable learning experience.
Typical Roles and Responsibilities
The effectiveness of a TTX hinges on the clearly defined roles and responsibilities of its participants. Each role plays a specific part in simulating an incident response, contributing to the overall learning objectives.
- Exercise Facilitator: The facilitator guides the exercise, presents the scenario, poses questions, and manages the discussion. Their primary responsibility is to keep the exercise on track, ensure that all participants have an opportunity to contribute, and steer the conversation toward the learning objectives. The facilitator also provides context and clarifies any ambiguities.
- Subject Matter Experts (SMEs): SMEs possess specialized knowledge in specific areas, such as legal, technical, or public relations. They provide expert advice and insights during the exercise, helping to inform the decision-making process. Their role is to answer questions, provide context, and offer guidance based on their expertise.
- Participants (Players): Participants are the individuals who actively engage in the exercise, representing their respective roles within the organization. They are responsible for responding to the scenario, making decisions, and discussing their actions. Participants should be familiar with their roles and responsibilities within the incident response plan.
- Observers: Observers are individuals who are present during the exercise but do not actively participate. They may be senior management, auditors, or individuals from other departments. Their role is to observe the exercise and provide feedback on the organization’s response capabilities. They may also take notes and provide a post-exercise assessment.
- Scenario Presenter/Controller: The scenario presenter is responsible for delivering the exercise scenario, providing updates, and injecting new information as the exercise progresses. They may also be responsible for simulating the actions of attackers or other external entities.
- Documentation Specialist/Recorder: This individual is responsible for documenting the exercise, including key decisions, actions taken, and lessons learned. They may also be responsible for capturing any deviations from the incident response plan.
Importance of Including Various Stakeholders
A comprehensive TTX should include a diverse group of stakeholders to ensure a well-rounded and effective exercise. The inclusion of various perspectives enhances the exercise’s value and facilitates a more realistic simulation of an incident response.
- Executive Leadership: Involvement from executive leadership provides strategic direction and demonstrates commitment to incident response preparedness. Their presence ensures that the exercise aligns with the organization’s overall goals and objectives.
- IT and Security Teams: IT and security teams are at the forefront of incident response. Their participation ensures that the technical aspects of the incident are thoroughly addressed, and that the organization’s security controls are effective.
- Legal Counsel: Legal counsel provides guidance on legal and regulatory requirements, ensuring that the organization’s response complies with all applicable laws and regulations. They can also advise on issues such as data privacy and breach notification requirements.
- Public Relations/Communications: Public relations and communications teams are crucial for managing the organization’s public image during an incident. Their participation ensures that the organization is prepared to communicate effectively with stakeholders, including customers, employees, and the media.
- Human Resources: Human resources representatives can address the impact of an incident on employees, including issues such as employee privacy, benefits, and potential disciplinary actions.
- Business Unit Representatives: Including representatives from various business units ensures that the exercise considers the impact of the incident on different parts of the organization. This allows for a more holistic and comprehensive response.
Comparison of Facilitator and Participant Roles
The facilitator and participant roles in a TTX have distinct responsibilities, each contributing to the exercise’s overall success. While both roles are essential, their functions and focus areas differ significantly.
| Role | Responsibilities |
|---|---|
| Facilitator |
|
| Participant |
|
The facilitator’s role is to guide and manage the exercise, while the participant’s role is to actively engage and respond to the scenario.
Designing a Tabletop Exercise Scenario
Crafting a compelling and effective tabletop exercise scenario is crucial for achieving the exercise’s objectives. A well-designed scenario provides a realistic context for participants to apply their incident response plans, identify gaps, and improve their coordination. This section will guide you through the process of creating a realistic and impactful scenario.
Creating a Realistic Incident Response Scenario
The process of designing a realistic scenario involves several key steps. These steps help ensure the scenario is both engaging and provides valuable learning opportunities for the participants. The goal is to simulate a plausible incident that challenges the team’s incident response capabilities.
- Define Objectives and Scope: Begin by clearly defining the exercise objectives. What specific skills or aspects of incident response do you want to assess? This will dictate the type of incident and the level of detail required. Consider the organization’s specific risks, industry regulations, and past incidents. The scope defines the boundaries of the exercise.
- Identify Threat Actors and Motivations: Determine the potential threat actors and their motivations. This helps to create a realistic attack vector and realistic behaviors. Consider factors such as the attacker’s sophistication, resources, and goals. Understanding the threat landscape is critical.
- Select the Incident Type: Choose an incident type that aligns with the objectives and scope. Consider common threats such as malware infections, phishing attacks, ransomware, data breaches, denial-of-service attacks, and insider threats. The selection should be relevant to the organization’s risk profile.
- Develop the Attack Narrative: Construct a narrative that describes the attack from start to finish. This narrative should include the initial attack vector, the attacker’s actions, the impact on the organization, and the evidence available to the incident responders.
- Create Inject Messages: Develop a series of injects – short, focused pieces of information delivered to participants at specific points in the exercise. Injects drive the scenario forward and provide new information or challenges.
- Determine the Exercise Timeline: Establish a timeline for the exercise, including the start and end times, and the timing of injects. The timeline should be realistic, considering the typical response times for the incident type.
- Prepare Supporting Documentation: Gather or create any supporting documentation needed for the exercise, such as network diagrams, system logs, and incident response plans.
- Validate the Scenario: Test the scenario with a small group of subject matter experts to ensure it is realistic, challenging, and achieves the objectives. Refine the scenario based on their feedback.
Key Elements to Consider When Designing a Scenario
Several key elements contribute to a well-designed incident response scenario. Paying attention to these elements ensures the exercise is both effective and engaging for the participants.
- Realism: The scenario should reflect real-world threats and vulnerabilities. Base the scenario on actual incidents, threat intelligence reports, or industry best practices. The more realistic the scenario, the more valuable the learning experience.
- Relevance: The scenario should be relevant to the organization’s specific environment, including its industry, size, and IT infrastructure.
- Complexity: The scenario should be complex enough to challenge participants but not so complex that it overwhelms them. The level of complexity should align with the experience level of the participants.
- Engagement: The scenario should be engaging and keep participants interested. Use a compelling narrative, and provide opportunities for participants to make decisions and solve problems.
- Measurable Outcomes: The scenario should be designed to generate measurable outcomes. The exercise objectives should be clearly defined, and the scenario should provide opportunities to assess whether those objectives are met.
- Flexibility: The scenario should be flexible enough to adapt to participant actions and unexpected events. The exercise facilitator should be prepared to adjust the scenario based on the participants’ responses.
- Evidence: Provide realistic evidence that participants can use to investigate the incident. This evidence could include log files, network traffic captures, and security alerts. The availability and quality of evidence greatly influence the exercise.
Basic Incident Scenario: Phishing Attack
This scenario involves a phishing attack targeting employees of a fictitious company, “InnovateTech.” The goal is to test the incident response team’s ability to detect, contain, and remediate a phishing attack.
Scenario Overview:
InnovateTech has been targeted by a phishing campaign. Employees have received emails appearing to be from the IT department, asking them to update their passwords. Several employees have clicked on the malicious link and entered their credentials. The attackers now have access to employee accounts.
Objectives:
- Assess the incident response team’s ability to detect and analyze phishing emails.
- Evaluate the team’s ability to contain the spread of the attack.
- Assess the team’s ability to identify compromised accounts.
- Test the team’s ability to remediate the incident and recover from the attack.
Timeline and Injects (Example):
- T+0: Exercise begins. The facilitator provides an initial inject: “Several employees have reported receiving suspicious emails.”
- T+15 minutes: An inject is delivered: “A user has reported clicking on a link in a phishing email and entering their credentials.”
- T+30 minutes: An inject is delivered: “The incident response team discovers suspicious activity in the network logs, indicating potential lateral movement.”
- T+45 minutes: An inject is delivered: “The team identifies several compromised accounts. The attacker is attempting to exfiltrate data.”
- T+60 minutes: Exercise concludes.
Evidence Provided:
- Sample phishing email headers and content.
- Network logs showing suspicious activity.
- User account activity logs.
- A list of compromised accounts.
Discussion Points:
- How does the team detect phishing emails?
- What steps are taken to contain the attack?
- How are compromised accounts identified?
- What is the process for resetting passwords and restoring access?
- What are the steps to prevent future attacks?
Expected Outcomes:
- Improved detection and analysis of phishing emails.
- Faster containment of the attack.
- Efficient identification and remediation of compromised accounts.
- Enhanced communication and coordination within the incident response team.
Exercise Preparation and Planning
Preparing and planning are critical phases in ensuring a successful tabletop exercise (TTX) for incident response. This involves meticulous organization, resource allocation, and the establishment of clear goals. A well-prepared exercise provides a realistic and productive learning environment, allowing participants to test and refine their incident response plans and procedures. Effective planning minimizes disruptions, maximizes learning outcomes, and contributes to the overall preparedness of the organization.
Steps Involved in Preparing for a Tabletop Exercise
The preparation phase is a multi-step process that ensures the exercise runs smoothly and achieves its intended objectives. Each step is crucial for setting the stage for a productive and insightful session.
- Define Exercise Scope and Objectives: Clearly articulate the purpose of the TTX. This includes identifying the specific incident scenarios to be explored, the key learning objectives, and the desired outcomes. For instance, the exercise might focus on testing the organization’s response to a ransomware attack, evaluating the effectiveness of communication protocols, and identifying areas for improvement in the incident response plan.
- Identify Participants and Roles: Determine the individuals or teams who will participate in the exercise, and assign them specific roles and responsibilities. This may include incident responders, IT staff, legal counsel, public relations personnel, and executive leadership. Providing participants with role-specific information helps them understand their responsibilities during the exercise.
- Develop the Scenario: Create a realistic and challenging incident scenario that aligns with the exercise objectives. The scenario should include a timeline of events, relevant details, and potential challenges. It should also consider various factors, such as the type of attack, the affected systems, and the potential impact on the organization.
- Prepare Exercise Materials: Compile all necessary materials for the exercise, including the scenario document, participant guides, communication templates, and any relevant technical documentation. These materials provide participants with the information they need to engage in the exercise effectively.
- Arrange Logistics: Organize the physical or virtual environment for the exercise, including the meeting space, technology, and any necessary resources. This also involves scheduling the exercise, notifying participants, and ensuring that all participants have the necessary access and information.
- Conduct a Pre-Exercise Briefing: Before the exercise begins, provide participants with a briefing on the exercise objectives, scenario, and rules of engagement. This ensures that everyone understands the purpose of the exercise and their roles and responsibilities.
Checklist for Pre-Exercise Activities
A pre-exercise checklist is a valuable tool for ensuring that all necessary tasks are completed before the TTX begins. It helps to maintain organization, reduce the risk of overlooking critical details, and ensure that the exercise is well-prepared.
- Confirm Exercise Objectives: Review and finalize the exercise objectives to ensure they are clearly defined and measurable.
- Finalize Scenario Details: Review the scenario to ensure it is realistic, challenging, and relevant to the organization’s risk profile.
- Distribute Participant Materials: Distribute all necessary materials, such as the scenario document, participant guides, and any relevant technical documentation, to all participants in advance.
- Confirm Participant Availability: Confirm that all participants are available and able to attend the exercise.
- Test Technology and Communication Channels: Ensure that all technology, such as video conferencing software and communication tools, is functioning correctly.
- Prepare the Exercise Environment: Set up the physical or virtual environment for the exercise, including the meeting space, technology, and any necessary resources.
- Conduct a Dry Run (Optional): Consider conducting a dry run of the exercise with a small group to identify any potential issues or areas for improvement.
Importance of Setting Clear Exercise Objectives
Establishing clear exercise objectives is fundamental to the success of a tabletop exercise. Well-defined objectives provide a roadmap for the exercise, guiding the scenario development, participant engagement, and evaluation process.
Setting clear objectives helps to ensure that the exercise is focused, relevant, and productive, ultimately leading to improved incident response capabilities.
- Focus the Exercise: Clearly defined objectives help to focus the exercise on specific areas of concern, ensuring that the scenario and discussions are relevant to the organization’s needs.
- Guide Scenario Development: Objectives guide the development of the scenario, ensuring that it includes the necessary elements to test the organization’s response capabilities. For example, if an objective is to test the organization’s communication protocols during a data breach, the scenario will include elements that trigger those protocols.
- Facilitate Participant Engagement: Objectives provide participants with a clear understanding of the exercise’s purpose, enabling them to engage more effectively and contribute to meaningful discussions.
- Enable Effective Evaluation: Objectives provide a framework for evaluating the exercise’s success, allowing the facilitator to assess whether the intended learning outcomes were achieved. For instance, an objective might be to evaluate the speed of containment. Post-exercise, the team would measure how long containment took and compare it to the objective.
- Improve Incident Response Plans: Objectives drive the identification of areas for improvement in the incident response plan, leading to a more robust and effective response strategy.
Conducting the Tabletop Exercise
Now that the exercise is planned and prepared, the execution phase of the tabletop exercise (TTX) for incident response is critical. This section provides a detailed guide on conducting the TTX, emphasizing facilitation techniques, and strategies for maintaining engagement and focus. Effective execution ensures the exercise achieves its objectives and delivers valuable insights.
Step-by-Step Guide to Running a Tabletop Exercise
A well-structured approach is crucial for a successful TTX. Following a defined process ensures all aspects are covered and the exercise remains focused.
- Opening Remarks and Introductions: The facilitator begins by welcoming participants, reiterating the exercise’s objectives, scope, and ground rules. Briefly introduce the scenario and set the stage. This includes outlining the expected timeline and the roles of the facilitator and any observers.
- Scenario Presentation: The facilitator presents the initial scenario, often in the form of a brief overview of the incident. This could be a description of a security breach, a phishing attack, or a system outage. The initial information should be clear and concise.
- Module-Based Discussions: The exercise is typically broken down into modules, each focusing on a specific aspect of the incident response plan. Each module presents new information or developments related to the incident.
- Facilitated Discussion: For each module, the facilitator poses questions or prompts designed to elicit discussion among the participants. The questions should relate to the scenario and the organization’s incident response plan.
- Participant Responses and Analysis: Participants respond to the prompts, discussing their actions, decisions, and the rationale behind them. The facilitator guides the discussion, ensuring all relevant aspects of the plan are considered.
- Scenario Progression: After each discussion module, the facilitator provides additional information or “injects” to the scenario, based on the participants’ actions and the evolving situation. This might include new threats, additional compromised systems, or external communications.
- Plan Evaluation: As the exercise progresses, the facilitator guides the participants to evaluate the effectiveness of the incident response plan. This involves identifying strengths, weaknesses, gaps, and areas for improvement.
- Documentation: Throughout the exercise, a scribe documents the key discussions, decisions, and recommendations. This documentation forms the basis for the after-action report.
- Wrap-up and Summary: At the end of the exercise, the facilitator summarizes the key findings, lessons learned, and any action items.
- Closing Remarks: The facilitator thanks the participants for their engagement and provides any final thoughts.
Best Practices for Facilitating Discussions
Effective facilitation is key to maximizing the value of a TTX. The facilitator’s role is to guide the discussion, encourage participation, and ensure the exercise stays on track.
- Active Listening: The facilitator should actively listen to participants’ responses, summarizing and clarifying points to ensure understanding.
- Open-Ended Questions: Use open-ended questions that encourage participants to think critically and share their perspectives. Avoid questions that can be answered with a simple “yes” or “no.” For example, instead of asking, “Did you follow the plan?” ask, “What steps did you take in response to the incident, and why?”
- Encouraging Participation: Encourage participation from all attendees, ensuring that quieter participants have a chance to speak and that no single person dominates the discussion.
- Managing Time: Keep the discussion focused and on track. The facilitator should manage time effectively, ensuring that each module receives adequate attention without exceeding the allotted time.
- Staying Neutral: Remain neutral and avoid expressing personal opinions or biases. The facilitator’s role is to guide the discussion, not to judge the participants’ actions.
- Providing Context: Offer context and relevant information to help participants understand the situation and make informed decisions. This may include referencing the incident response plan, security policies, or other relevant documentation.
- Summarizing Key Points: Regularly summarize the key points of the discussion to reinforce the lessons learned and ensure that everyone is on the same page.
Techniques for Keeping the Exercise on Track and Engaging Participants
Maintaining engagement and focus throughout a TTX requires several techniques. These strategies help ensure that the exercise remains productive and informative.
- Scenario Management: Maintain a realistic and engaging scenario, ensuring it reflects potential real-world incidents. The scenario should be relevant to the organization’s environment and the participants’ roles.
- Time Management: Stick to the planned schedule and manage time effectively. This involves allocating appropriate time for each module and ensuring that discussions remain focused.
- Use of Visual Aids: Utilize visual aids, such as slides, diagrams, or charts, to illustrate key points and enhance understanding.
- Injections and Updates: Provide regular updates and “injections” to the scenario to keep participants engaged and challenge their decision-making skills. These updates should be realistic and based on the participants’ actions.
- Role-Playing: Consider incorporating role-playing to simulate real-world interactions. For example, participants might role-play communicating with the media or coordinating with law enforcement.
- Encouraging Critical Thinking: Prompt participants to think critically about their decisions and the potential consequences of their actions. Ask “what if” questions to explore different scenarios.
- Positive Reinforcement: Provide positive reinforcement and acknowledge the participants’ contributions. This helps to create a positive and collaborative environment.
- Debriefing: Conclude each module with a brief debriefing to summarize the key takeaways and lessons learned. This reinforces the learning and ensures that everyone understands the key points.
Post-Exercise Activities
The post-exercise phase is critical to the overall success of a tabletop exercise (TTX). This phase focuses on extracting valuable insights from the exercise, analyzing performance, and identifying areas for improvement in the incident response plan and team capabilities. It involves a structured debriefing session and a comprehensive analysis of the exercise outcomes. This process helps to translate the TTX experience into actionable improvements.
Significance of a Post-Exercise Debriefing Session
A debriefing session is a structured discussion held immediately after the TTX concludes. It serves as a platform for participants to share their experiences, observations, and lessons learned during the exercise. This session provides an opportunity to gather feedback on the exercise itself, the incident response plan, and the team’s performance. The debriefing session is vital for identifying strengths and weaknesses and for fostering a culture of continuous improvement.The debriefing session is important for several reasons:
- Capturing Immediate Feedback: It allows for the collection of fresh perspectives and insights while the exercise is still fresh in participants’ minds.
- Identifying Gaps: It helps to uncover any gaps or inconsistencies in the incident response plan, procedures, or communication protocols.
- Promoting Learning: It facilitates a shared understanding of the exercise objectives, scenarios, and outcomes, which promotes learning and knowledge sharing among participants.
- Building Team Cohesion: It fosters a sense of teamwork and collaboration by encouraging participants to reflect on their roles and contributions within the context of the exercise.
- Driving Improvement: It provides the basis for developing recommendations and action items to enhance the incident response capabilities of the organization.
Key Components of a Debriefing Report
The debriefing report documents the key findings and recommendations from the post-exercise debriefing session. It serves as a valuable reference for future exercises and for implementing improvements to the incident response plan.The key components of a debriefing report include:
- Exercise Overview: A brief summary of the exercise, including its objectives, scenario, and participants.
- Key Observations: A summary of the main observations and insights from the exercise, including both positive and negative aspects.
- Strengths: Identification of the areas where the team performed well, such as effective communication, adherence to procedures, or quick decision-making.
- Weaknesses: Identification of the areas where the team struggled, such as slow response times, communication breakdowns, or procedural errors.
- Lessons Learned: A list of key lessons learned from the exercise, highlighting what went well and what could be improved.
- Recommendations: Specific, actionable recommendations for improving the incident response plan, procedures, training, or team capabilities.
- Action Items: A list of specific tasks to be completed, including the responsible parties and deadlines for implementation.
- Appendices: Supporting documents, such as the exercise scenario, participant list, and any relevant communications or logs.
Process of Analyzing Exercise Outcomes
Analyzing exercise outcomes involves a systematic review of the data and feedback collected during the TTX, including the debriefing session, participant feedback, and exercise logs. The analysis aims to identify areas for improvement and to inform the development of an action plan to enhance the incident response capabilities of the organization.The process of analyzing exercise outcomes typically involves the following steps:
- Data Collection: Gathering all relevant data from the exercise, including the debriefing report, participant feedback surveys, exercise logs, and any other documentation.
- Data Review: Reviewing the collected data to identify key themes, patterns, and trends related to the exercise objectives and scenario.
- Performance Evaluation: Evaluating the team’s performance against the exercise objectives and performance metrics.
- Gap Analysis: Identifying any gaps or discrepancies between the expected performance and the actual performance, including any deviations from established procedures.
- Root Cause Analysis: Determining the underlying causes of any identified weaknesses or failures, such as inadequate training, unclear procedures, or communication breakdowns.
- Recommendation Development: Developing specific, actionable recommendations to address the identified weaknesses and to improve the incident response plan and team capabilities.
- Action Plan Development: Creating an action plan that Artikels the specific tasks, responsible parties, and deadlines for implementing the recommendations.
- Reporting: Preparing a comprehensive report summarizing the exercise outcomes, including the findings, recommendations, and action plan.
For example, consider a TTX where the scenario involved a ransomware attack. During the analysis, the team might discover that the backup and recovery procedures were not followed correctly, resulting in extended downtime. The root cause analysis might reveal that the team lacked adequate training on the backup and recovery procedures. The recommendation could be to provide specialized training to the relevant team members, and the action plan would include a schedule for delivering the training and verifying its effectiveness.
This proactive approach is crucial for improving the organization’s resilience against cyber threats.
Common Incident Response Scenarios for TTXs
Tabletop exercises (TTXs) are invaluable for honing incident response capabilities. They allow teams to practice their response procedures, identify weaknesses, and improve communication in a low-pressure environment. Selecting appropriate scenarios is crucial for a successful TTX. This section provides examples of incident response scenarios suitable for tabletop exercises, compares different types of cyberattacks, and explains how to incorporate real-world threat intelligence.
Scenario Examples for Tabletop Exercises
The choice of scenario should align with the organization’s risk profile and business objectives. Consider the organization’s industry, size, and existing security controls when selecting a scenario. Several common scenarios are well-suited for tabletop exercises, providing opportunities to assess various aspects of incident response.
- Ransomware Attack: This is a prevalent threat. A ransomware scenario can involve the encryption of critical systems, demands for payment, and the potential for data exfiltration. Participants must consider containment, eradication, recovery, and communication strategies.
- Data Breach: Scenarios involving data breaches can cover various attack vectors, such as phishing, compromised credentials, or vulnerabilities in web applications. The exercise can focus on identifying the scope of the breach, notifying affected parties, and mitigating damage to the organization’s reputation.
- Denial-of-Service (DoS) or Distributed Denial-of-Service (DDoS) Attack: These attacks aim to disrupt service availability. A TTX can simulate a DDoS attack targeting critical infrastructure, such as a website or network services. Participants will need to analyze traffic patterns, implement mitigation strategies, and manage communications with stakeholders.
- Insider Threat: This scenario involves malicious or negligent actions by employees or contractors. The exercise can explore the detection of insider activities, the investigation process, and the legal and HR considerations associated with the incident.
- Supply Chain Attack: This type of attack targets an organization through its vendors or suppliers. A TTX can simulate a scenario where a vendor’s system is compromised, leading to a compromise of the organization’s systems. Participants will need to assess the impact, communicate with the vendor, and implement remediation measures.
- Phishing Campaign: A simulated phishing campaign allows teams to practice identifying and responding to phishing attempts. The exercise can assess the effectiveness of employee training, phishing detection tools, and incident reporting procedures.
Comparison of Cyberattack Types in TTXs
Different types of cyberattacks require distinct response strategies. Understanding the characteristics of each attack type is crucial for designing effective TTX scenarios. The following table compares various cyberattack types, highlighting their key features and the associated response considerations.
| Attack Type | Description | Impact | TTX Considerations |
|---|---|---|---|
| Ransomware | Malware that encrypts data and demands a ransom for its release. | Data loss, business disruption, financial loss, reputational damage. | Data backup and recovery, ransom negotiation (if applicable), law enforcement involvement, communication strategy. |
| Data Breach | Unauthorized access to sensitive data. | Data loss, regulatory fines, legal liabilities, reputational damage. | Containment, eradication, notification requirements, legal counsel, public relations. |
| DoS/DDoS | Overwhelming a system with traffic to make it unavailable. | Service disruption, financial loss, reputational damage. | Traffic analysis, mitigation tools, incident response plan, communication protocols. |
| Phishing | Deceptive emails or messages designed to trick users into revealing sensitive information. | Data theft, malware infection, financial loss, reputational damage. | User awareness training, email security filters, incident reporting procedures, phishing simulation exercises. |
| Insider Threat | Malicious or negligent actions by employees or contractors. | Data theft, data leakage, sabotage, financial loss, reputational damage. | Access controls, monitoring systems, incident investigation, legal and HR considerations. |
| Supply Chain Attack | Compromising an organization through its vendors or suppliers. | Data loss, system compromise, business disruption, reputational damage. | Vendor risk management, incident response plan, communication with vendors, incident containment and remediation. |
Incorporating Real-World Threat Intelligence
Integrating real-world threat intelligence into a TTX scenario significantly enhances its realism and effectiveness. Threat intelligence provides insights into current attack trends, tactics, techniques, and procedures (TTPs) used by threat actors.
- Sources of Threat Intelligence:
- Security Vendors: Many security vendors provide threat intelligence feeds, reports, and alerts.
- Industry-Specific Information Sharing and Analysis Centers (ISACs): ISACs facilitate the sharing of threat information among organizations within the same industry.
- Government Agencies: Governmental organizations, such as CISA (Cybersecurity and Infrastructure Security Agency), often publish threat advisories and reports.
- Open-Source Intelligence (OSINT): Publicly available information, such as news articles, social media, and vulnerability databases, can provide valuable threat intelligence.
- Incorporating Threat Intelligence into a Scenario:
- Identify Relevant Threats: Research current threat actors, their TTPs, and the vulnerabilities they are exploiting.
- Develop a Realistic Attack Scenario: Base the scenario on real-world attacks, incorporating the tactics and techniques observed in recent incidents.
- Include Indicators of Compromise (IOCs): Provide participants with IOCs, such as malicious IP addresses, file hashes, and domain names, to help them identify and analyze the attack.
- Use Threat Intelligence Reports: Share relevant threat intelligence reports with participants to provide context and enhance their understanding of the attack.
Example: Suppose a threat intelligence report reveals that a new ransomware variant is targeting organizations in the healthcare industry. The TTX scenario could simulate an attack involving this ransomware variant, including the specific TTPs and IOCs identified in the report. This allows participants to practice their response to a realistic and relevant threat.
Benefits of Tabletop Exercises
Regularly conducting tabletop exercises (TTXs) is a crucial component of a robust incident response plan. These exercises offer numerous advantages, contributing significantly to an organization’s ability to effectively manage and mitigate cybersecurity incidents. The benefits extend beyond simply identifying weaknesses; they foster a culture of preparedness and continuous improvement.
Improved Incident Response Capabilities
TTXs are designed to simulate realistic incident scenarios, providing participants with the opportunity to practice their roles and responsibilities in a safe environment. This practice directly translates into improved incident response capabilities. By working through different scenarios, teams gain experience in decision-making, communication, and coordination, all under pressure. This hands-on experience allows for identification of gaps in existing plans, policies, and procedures, as well as the opportunity to refine them.
Key Benefits of Tabletop Exercises
The following points highlight the primary advantages of conducting tabletop exercises for incident response:
- Enhanced Team Coordination: TTXs facilitate improved communication and collaboration among team members. Participants learn how to effectively share information, coordinate actions, and make decisions as a cohesive unit. For instance, during a simulated ransomware attack, team members can practice how to quickly communicate with each other, including which channels to use, and how to share key information such as the extent of the breach, the systems affected, and the actions taken to contain the damage.
This can significantly reduce response times and minimize the impact of the incident.
- Identification of Weaknesses: Exercises help uncover vulnerabilities in incident response plans, policies, and procedures. Participants can identify areas where processes are unclear, roles are undefined, or resources are lacking. For example, a TTX might reveal that the organization’s communication plan does not include a designated spokesperson or that the data backup procedures are inadequate.
- Improved Decision-Making: TTXs provide a platform to practice decision-making under pressure. Participants are challenged to analyze information, assess risks, and make informed choices in a simulated crisis environment. For example, during a simulated data breach, participants might be faced with a decision on whether to pay a ransom, notify law enforcement, or contain the breach and begin data recovery.
- Increased Awareness: TTXs raise awareness of cybersecurity threats and the importance of incident response within the organization. This can lead to a more security-conscious culture and encourage employees to take a proactive approach to security. This can also provide an opportunity to train on new threats and tools.
- Refinement of Incident Response Plans: Based on the lessons learned during TTXs, organizations can refine and improve their incident response plans. This iterative process ensures that plans remain relevant and effective in the face of evolving threats. For instance, after a TTX, the organization might update its communication plan to include more detailed contact information for key stakeholders, or it might revise its data recovery procedures to incorporate more frequent backups.
- Cost-Effectiveness: TTXs are a cost-effective way to test and improve incident response capabilities. Compared to live-fire exercises, TTXs require fewer resources and can be conducted more frequently. This allows organizations to regularly assess their preparedness and identify areas for improvement without incurring significant costs.
- Regulatory Compliance: Many industry regulations and standards require organizations to conduct regular incident response exercises. TTXs can help organizations meet these compliance requirements and demonstrate their commitment to cybersecurity. For example, regulations like HIPAA and PCI DSS often require organizations to have incident response plans and to test those plans regularly.
Methods for Measuring Exercise Effectiveness
Evaluating the effectiveness of a tabletop exercise (TTX) is crucial for identifying strengths and weaknesses in an organization’s incident response capabilities. This assessment provides valuable insights for refining plans, improving training, and ultimately enhancing the ability to effectively manage and recover from security incidents. The measurement process should be comprehensive, encompassing various aspects of the exercise, from participant understanding to the overall efficiency of the response procedures.
Metrics to Evaluate the Success of a Tabletop Exercise
Several key metrics can be employed to gauge the success of a TTX. These metrics provide a structured approach to assessing different facets of the exercise and its impact on the organization’s incident response readiness.
- Plan Coverage: This metric assesses the extent to which the incident response plan addresses the scenarios presented during the exercise. It evaluates whether the plan covers all critical aspects of the incident, including detection, containment, eradication, recovery, and post-incident activities. A well-designed plan should provide clear guidance for each stage of the incident lifecycle.
- Participant Understanding: This metric measures the participants’ comprehension of their roles, responsibilities, and the procedures Artikeld in the incident response plan. It evaluates their ability to apply the plan effectively in the simulated incident environment.
- Communication Effectiveness: This metric assesses the efficiency and clarity of communication among participants during the exercise. It examines whether information is shared promptly, accurately, and to the appropriate stakeholders. Effective communication is critical for coordinating response efforts and making informed decisions.
- Decision-Making Speed and Accuracy: This metric evaluates the speed and accuracy with which participants make decisions during the exercise. It assesses their ability to analyze information, assess risks, and select appropriate courses of action. Timely and accurate decision-making is essential for minimizing the impact of an incident.
- Resource Utilization: This metric examines how effectively participants utilize available resources, such as personnel, tools, and technologies. It evaluates whether resources are allocated appropriately and used efficiently to address the incident.
- Time to Completion of Key Tasks: This metric measures the time required to complete critical tasks, such as incident identification, containment, and recovery. Shorter completion times generally indicate a more efficient and effective response.
- Plan Adherence: This metric assesses the extent to which participants follow the procedures Artikeld in the incident response plan. It evaluates whether the plan is being implemented as intended and whether any deviations are justified.
- Identification of Gaps and Weaknesses: This metric focuses on identifying any shortcomings in the incident response plan, procedures, or team capabilities. It involves analyzing the exercise to pinpoint areas that require improvement.
- Overall Exercise Realism: This metric evaluates how closely the exercise simulates real-world incident scenarios. It assesses the realism of the threats, the complexity of the incident, and the challenges faced by participants.
Assessing Participant Understanding of Incident Response Plans
Evaluating participant understanding of the incident response plan is a critical component of assessing TTX effectiveness. This involves various methods to gauge how well participants comprehend their roles, responsibilities, and the procedures they should follow.
- Pre-Exercise Surveys: Administering pre-exercise surveys to assess participants’ initial knowledge of the incident response plan provides a baseline for comparison. These surveys can cover topics such as their understanding of roles, plan components, and incident handling procedures.
- Observation During the Exercise: Observing participants during the exercise allows for direct assessment of their understanding and application of the plan. Observers can note how well participants follow procedures, communicate with each other, and make decisions.
- Post-Exercise Questionnaires: Post-exercise questionnaires can be used to gather feedback on participant understanding. These questionnaires can include questions about their roles, the plan’s clarity, and their ability to apply the plan during the exercise.
- Scenario-Based Questions: Integrating scenario-based questions into the exercise itself allows for assessing participant understanding in a practical context. These questions can require participants to apply their knowledge of the plan to specific incident scenarios.
- Role-Playing Exercises: Incorporating role-playing exercises within the TTX allows participants to practice their roles and responsibilities, demonstrating their understanding of the plan in a simulated environment. This also helps in identifying areas where participants may need additional training or clarification.
- Review of Deliverables: Reviewing any deliverables produced during the exercise, such as incident reports or communication logs, can reveal how well participants understand and apply the plan.
Methods for Gathering Feedback from Participants
Gathering feedback from participants is essential for gaining valuable insights into the effectiveness of the TTX. This feedback helps to identify areas for improvement, understand participant perspectives, and refine future exercises.
- Post-Exercise Surveys: Post-exercise surveys are a common method for gathering feedback. These surveys can include a mix of multiple-choice questions, rating scales, and open-ended questions to capture both quantitative and qualitative data. They should cover various aspects of the exercise, such as clarity of objectives, scenario realism, and usefulness of the plan.
- Focus Groups: Conducting focus groups allows for in-depth discussions about the exercise. Participants can share their experiences, provide detailed feedback, and discuss areas for improvement. Focus groups can be particularly helpful for exploring complex issues or gathering nuanced perspectives.
- Individual Interviews: Individual interviews provide an opportunity to gather detailed feedback from individual participants. This method allows for a more personal and in-depth exploration of their experiences and perspectives.
- Debriefing Sessions: Debriefing sessions immediately following the exercise provide a platform for participants to share their immediate feedback and insights. These sessions can be facilitated by an exercise facilitator or observer.
- Feedback Forms: Providing feedback forms allows participants to provide written comments and suggestions. These forms can be distributed during the exercise or after it has concluded.
- Anonymous Feedback Mechanisms: Offering anonymous feedback mechanisms, such as online forms or suggestion boxes, can encourage participants to provide honest and candid feedback without fear of reprisal.
Using TTXs for Plan Improvement
Tabletop exercises (TTXs) are invaluable tools not only for practicing incident response but also for refining and improving incident response plans. By simulating realistic scenarios and identifying gaps or weaknesses in existing plans, TTXs provide actionable insights that can be directly applied to enhance preparedness and effectiveness. The process of using TTXs to improve plans is cyclical, involving the identification of shortcomings, the implementation of changes, and subsequent testing to validate the improvements.
Incorporating Lessons Learned into Plan Revisions
A structured process is crucial for translating TTX outcomes into tangible plan improvements. This process ensures that lessons learned are systematically captured, analyzed, and integrated into the incident response plan.The process for incorporating lessons learned into plan revisions involves the following steps:
- Exercise Debrief and After-Action Report (AAR): Following the TTX, a debriefing session is held with all participants to gather feedback and insights. This session should be facilitated by an experienced exercise controller or facilitator. The AAR is a formal document that summarizes the exercise, including objectives, scenario overview, key observations, and areas for improvement.
- Identifying Gaps and Weaknesses: During the debrief and AAR creation, the exercise participants and controller should collaboratively identify specific gaps and weaknesses in the existing incident response plan. These might include missing procedures, unclear roles and responsibilities, insufficient communication protocols, or inadequate resource allocation.
- Prioritizing Recommendations: Not all identified issues are equally critical. The team needs to prioritize the recommendations based on their potential impact on incident response effectiveness and the likelihood of occurrence. A risk assessment approach can be used to prioritize.
- Developing Action Items: For each prioritized recommendation, specific action items are developed. These action items should be SMART (Specific, Measurable, Achievable, Relevant, and Time-bound). For example, if the TTX reveals a communication failure, an action item might be to update the communication plan with a new contact tree and test it within two weeks.
- Implementing Plan Revisions: Based on the action items, the incident response plan is revised. This may involve updating procedures, clarifying roles, adding new communication protocols, or acquiring additional resources. The plan revisions should be clearly documented.
- Testing the Revised Plan: After the plan is revised, it’s crucial to test the changes. This can be done through another TTX, a functional exercise, or a walkthrough. This testing validates the effectiveness of the revisions and identifies any remaining issues.
- Documenting and Iterating: The entire process is documented, including the AAR, action items, plan revisions, and testing results. This documentation serves as a record of the improvement process and facilitates future iterations. The process is cyclical; further exercises and reviews will identify areas for improvement.
Comparing Original and Revised Plans Based on TTX Outcomes
A comparison table provides a clear visual representation of the changes made to the incident response plan based on the TTX outcomes. This table highlights the improvements and demonstrates the value of the exercise in enhancing preparedness.
| Area of Focus | Original Plan Description | TTX Outcome | Revised Plan Description |
|---|---|---|---|
| Communication Protocol | Reliance on email for all communications; no backup communication channels. | Email system failure during the simulated incident; delayed notifications. | Implemented a tiered communication system including SMS, phone calls, and a dedicated messaging platform; established a contact tree. |
| Roles and Responsibilities | Roles were generally defined but lacked specific task assignments and escalation procedures. | Confusion regarding who was responsible for specific actions; delayed decision-making. | Detailed roles and responsibilities with specific task assignments; clear escalation paths; updated contact information. |
| Incident Reporting | Incident reporting process lacked a standardized template; reporting was inconsistent. | Incomplete and inconsistent incident reports hindered the investigation and response. | Implemented a standardized incident reporting template; provided training on its use; established a reporting schedule. |
| Resource Availability | Limited documentation of available resources and contact information. | Difficulty in locating and deploying necessary resources during the simulated incident. | Developed a comprehensive resource inventory with contact information and procedures for requesting resources. |
Closing Notes
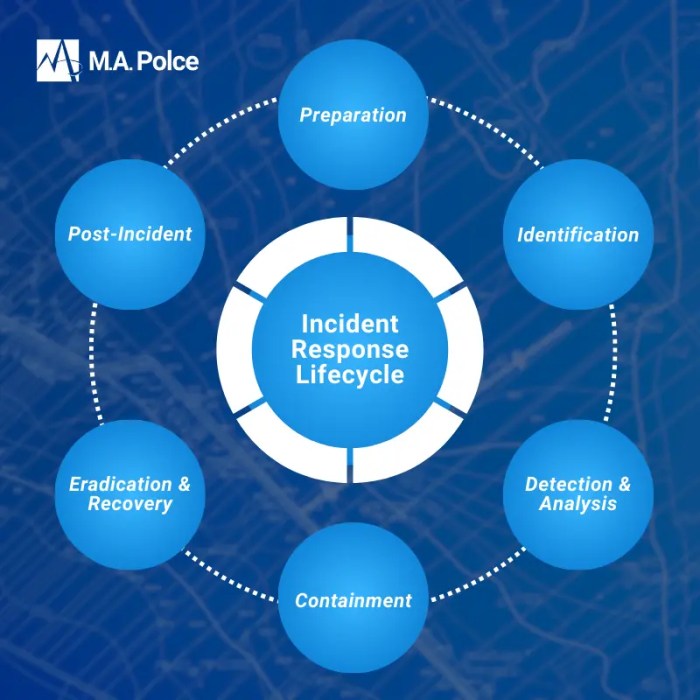
In conclusion, tabletop exercises for incident response are indispensable tools for organizations seeking to fortify their defenses against cyber threats. By actively engaging in these exercises, teams can improve their preparedness, refine their response strategies, and ultimately mitigate the impact of potential incidents. Embracing a proactive approach to incident response through tabletop exercises is not just a best practice; it is a critical investment in an organization’s resilience and long-term security.
Essential FAQs
What is the primary goal of a tabletop exercise?
The primary goal is to validate and improve an organization’s incident response plan and processes through a collaborative, discussion-based scenario.
Who should participate in a tabletop exercise?
Participants should include key stakeholders from various departments, such as IT, security, legal, communications, and executive management, to ensure a comprehensive understanding of the incident response process.
How often should tabletop exercises be conducted?
Regular tabletop exercises, ideally at least annually, or more frequently if there are significant changes to the organization’s infrastructure, threat landscape, or incident response plan, are recommended.
What are the key deliverables from a tabletop exercise?
Key deliverables include a debriefing report summarizing the exercise, identifying areas for improvement, and documenting any changes to the incident response plan.
How do tabletop exercises differ from other types of security training?
Tabletop exercises focus on discussion and decision-making, whereas other types of training may involve hands-on technical simulations or awareness campaigns.