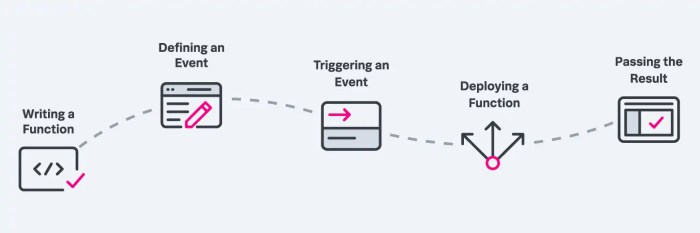
What is a serverless framework for deployment automation? It represents a paradigm shift in software development, moving away from managing servers and infrastructure towards a more efficient, scalable, and cost-effective approach. Serverless computing allows developers to focus on writing code, while the underlying infrastructure is handled by a cloud provider. This approach drastically simplifies deployment processes, enabling rapid iteration and reducing operational overhead.
This document will explore the core concepts of serverless frameworks, examining their key components, deployment methods, and integration with CI/CD pipelines. We will delve into the advantages of Infrastructure as Code (IaC) within a serverless context and analyze several popular frameworks, comparing their features and capabilities. Furthermore, we will cover best practices, troubleshooting techniques, and critical security considerations to ensure successful serverless deployments.
The goal is to provide a comprehensive understanding of how serverless frameworks revolutionize deployment automation, empowering developers to build and deploy applications more effectively.
Introduction to Serverless Frameworks
Serverless computing represents a significant shift in cloud architecture, moving away from managing servers directly and towards a model where the cloud provider handles the underlying infrastructure. This allows developers to focus solely on writing and deploying code, leading to increased efficiency and reduced operational overhead. Serverless frameworks are designed to streamline this process, offering tools and abstractions to simplify the deployment, management, and scaling of serverless applications.
Fundamental Concepts of Serverless Computing and its Advantages
Serverless computing, at its core, is a cloud computing execution model where the cloud provider dynamically manages the allocation of machine resources. Developers upload code, and the provider handles everything else, including provisioning, scaling, and maintenance. This contrasts with traditional server-based models where developers are responsible for managing servers. This shift offers several key advantages.
- Reduced Operational Overhead: Developers no longer need to manage servers, operating systems, or patching. This frees up valuable time and resources to focus on building applications.
- Automatic Scaling: Serverless platforms automatically scale resources up or down based on demand. This ensures applications can handle traffic spikes without manual intervention and helps to optimize costs.
- Pay-per-use Pricing: Users are charged only for the actual compute time and resources consumed. This can significantly reduce costs compared to traditional models where resources are provisioned and paid for continuously, regardless of usage.
- Increased Agility: Serverless architectures allow for faster development cycles and quicker deployments. Developers can iterate more rapidly and respond to changing business requirements more effectively.
- Improved Scalability and Reliability: Serverless platforms are designed to handle high traffic loads and provide built-in redundancy, leading to highly scalable and reliable applications.
Definition of a Serverless Framework in the Context of Deployment Automation
A serverless framework, in the context of deployment automation, is a set of tools and methodologies that simplifies the process of building, deploying, and managing serverless applications. It acts as an abstraction layer, hiding the complexities of the underlying cloud infrastructure and providing a more streamlined and efficient development experience. These frameworks typically include features such as:
- Infrastructure as Code (IaC): Allows developers to define their infrastructure (functions, APIs, databases, etc.) as code, enabling version control, repeatability, and automated deployments.
- Deployment Orchestration: Automates the deployment process, including packaging code, uploading it to the cloud provider, configuring resources, and managing dependencies.
- Local Development and Testing: Provides tools for developing and testing serverless functions locally, allowing for faster iteration and debugging.
- Monitoring and Logging: Integrates with cloud provider services for monitoring application performance, logging events, and troubleshooting issues.
- Simplified Configuration: Offers a simplified way to configure serverless applications, including environment variables, security settings, and other configurations.
Brief History of Serverless Frameworks and Their Evolution
The emergence of serverless frameworks is directly linked to the evolution of serverless computing itself. Early serverless offerings, such as AWS Lambda (launched in 2014), provided the basic building blocks for serverless applications. However, managing these functions and their associated infrastructure directly was complex and time-consuming. This led to the development of frameworks that addressed these challenges.
- Early Frameworks (2015-2017): The initial serverless frameworks focused on simplifying deployment and configuration. Examples include the Serverless Framework (formerly known as “JAWS”), which gained popularity by providing a command-line interface (CLI) for deploying functions to AWS Lambda. These frameworks often utilized YAML or JSON files to define the application’s infrastructure.
- Growth and Maturity (2018-2020): As serverless adoption grew, frameworks expanded their capabilities. They began to support multiple cloud providers (AWS, Azure, Google Cloud), enabling developers to build multi-cloud applications. They also introduced features like local testing, more sophisticated infrastructure as code capabilities, and integrations with other development tools.
- Current Trends (2021-Present): Modern serverless frameworks emphasize developer experience, security, and observability. They focus on simplifying the entire development lifecycle, from local development to deployment and monitoring. Many frameworks are incorporating advanced features like support for CI/CD pipelines, improved security integrations, and more robust debugging tools. They are also increasingly focusing on helping developers manage the complexity of serverless applications at scale.
The Serverless Framework, for example, continues to evolve, supporting new features and cloud providers, demonstrating the ongoing growth and refinement of this technology.
Core Components of a Serverless Framework
Serverless frameworks streamline the development and deployment of applications by abstracting away infrastructure management. They provide a structured environment for building applications that leverage cloud provider services, enabling developers to focus on code rather than server provisioning and maintenance. This section details the core components that constitute a typical serverless framework and how they interact to automate deployment processes.
Functions
Functions are the fundamental building blocks of serverless applications. These are individual, self-contained units of code that execute in response to specific events. They are designed to be stateless, meaning they don’t retain any information from previous executions, ensuring scalability and reliability.* A function is a piece of code that performs a specific task. For example, a function might process a file upload, resize an image, or send a notification.
- Functions are triggered by events.
- Functions are typically written in common programming languages, such as Python, Node.js, Java, or Go.
- Functions are deployed and managed by the serverless framework. The framework handles the scaling, execution, and monitoring of functions.
Events
Events are occurrences that trigger the execution of functions. These events can originate from various sources, including user actions, scheduled tasks, or other cloud services. The serverless framework defines how these events are mapped to function invocations.* Events act as triggers that initiate the execution of a function.
- Examples of events include HTTP requests, database updates, file uploads, and scheduled timers.
- Events are typically provided by the cloud provider’s services. For example, AWS Lambda supports events from services like API Gateway, S3, DynamoDB, and CloudWatch Events.
- The framework configures event sources and maps them to specific functions. This mapping is often defined in a configuration file, such as `serverless.yml`.
Triggers
Triggers are the mechanisms that connect events to functions. They define how and when a function is invoked in response to an event. Triggers often involve configuring specific parameters, such as event types, routing rules, and security settings.* Triggers are responsible for initiating the execution of a function when a specific event occurs.
- They act as the intermediary between events and functions.
- Triggers can be configured to handle various event types, such as HTTP requests, database changes, or scheduled tasks.
- They manage the invocation of functions, including passing event data and handling errors.
Deployment Automation
Serverless frameworks automate the deployment process, streamlining the release of applications to production. This automation typically involves a series of steps that manage infrastructure, code, and configurations.* The framework uses a configuration file (e.g., `serverless.yml`) to define the application’s resources, including functions, events, and triggers.
- The framework packages the code and dependencies, ensuring they are ready for deployment.
- The framework provisions and configures the necessary cloud resources, such as functions, API gateways, and databases.
- The framework deploys the code and configuration to the cloud provider.
- The framework handles updates and rollbacks, ensuring that the application remains available and consistent.
Architectural Diagram
The following diagram illustrates the flow of a serverless application deployment using a framework. This example showcases an API Gateway trigger activating a Lambda function in response to an HTTP request.“`[Diagram Description:A rectangular box labeled “User” represents the user initiating the action. An arrow points from the “User” box to a box labeled “API Gateway,” which represents the entry point for the application.
The API Gateway box is connected to a box labeled “Serverless Framework” via an arrow. This box signifies the role of the serverless framework in managing the deployment and configuration. The “Serverless Framework” box is connected to a box labeled “Lambda Function” via an arrow, which indicates the execution of the function. An arrow connects the “Lambda Function” to a “Database” box, representing interaction with the database.
Finally, an arrow returns from the “Lambda Function” back to the “API Gateway” box, indicating a response to the user. All boxes are labeled in plain text. ]“`The diagram represents a typical deployment flow:
- A user initiates an action (e.g., sending an HTTP request).
- The request is received by the API Gateway, which acts as the trigger.
- The API Gateway triggers the Serverless Framework.
- The Serverless Framework invokes the Lambda Function.
- The Lambda Function interacts with a database (e.g., querying or updating data).
- The Lambda Function returns a response to the API Gateway.
- The API Gateway returns the response to the user.
Deployment Automation with Serverless Frameworks

Serverless frameworks streamline the deployment process by automating tasks traditionally handled manually. This automation is crucial for achieving the agility and scalability that serverless architectures promise. By automating deployments, developers can focus on writing code and business logic rather than the intricacies of infrastructure management.
Deployment Automation with Serverless Frameworks: Methods
Serverless frameworks utilize various methods to automate the deployment of serverless applications. These methods range from Infrastructure as Code (IaC) to seamless integration with Continuous Integration and Continuous Delivery (CI/CD) pipelines. Understanding these methods is critical for selecting the appropriate deployment strategy.Infrastructure as Code (IaC) is a cornerstone of serverless deployment automation. IaC allows developers to define and manage infrastructure through code, enabling repeatable and consistent deployments.
Serverless frameworks leverage IaC principles to define and provision cloud resources, such as functions, APIs, and databases.* Infrastructure as Code (IaC): IaC enables the declarative definition of infrastructure, allowing for version control, repeatability, and automation. Serverless frameworks typically use configuration files (e.g., YAML, JSON) to describe the desired state of the infrastructure.
Strengths
Repeatability
Deployments can be consistently replicated across different environments (e.g., development, staging, production).
Version Control
Infrastructure configurations can be tracked and managed using version control systems, facilitating collaboration and rollback capabilities.
Automation
IaC automates the provisioning and configuration of infrastructure, reducing manual effort and human error.
Scalability
Infrastructure can be scaled up or down easily by modifying the configuration files.
Weaknesses
Complexity
IaC configurations can become complex, especially for large-scale applications.
Learning Curve
Developers need to learn the syntax and concepts of the IaC tool (e.g., CloudFormation, Terraform).
Debugging
Debugging IaC configurations can be challenging, as errors may not always be immediately apparent.Continuous Integration and Continuous Delivery (CI/CD) integration is another key method for automating serverless deployments. CI/CD pipelines automate the build, test, and deployment processes, enabling faster release cycles and improved code quality.* CI/CD Integration: Serverless frameworks integrate with CI/CD platforms to automate the build, test, and deployment processes.
This integration allows developers to automatically deploy code changes to the cloud upon code commits.
Strengths
Faster Release Cycles
CI/CD pipelines automate the deployment process, reducing the time it takes to release new features and bug fixes.
Improved Code Quality
Automated testing within CI/CD pipelines helps identify and fix bugs early in the development process.
Reduced Risk
Automated deployments minimize the risk of human error and deployment failures.
Increased Efficiency
CI/CD pipelines automate repetitive tasks, freeing up developers to focus on more important work.
Weaknesses
Setup Complexity
Setting up and configuring CI/CD pipelines can be complex and time-consuming.
Maintenance Overhead
CI/CD pipelines require ongoing maintenance and monitoring.
Dependency on External Services
CI/CD pipelines rely on external services, such as build servers and testing frameworks.The selection of the most appropriate deployment method depends on the specific requirements of the project. For simple applications, IaC alone may suffice. However, for complex applications, CI/CD integration is generally recommended to automate the entire deployment process.Here’s a comparison table:| Feature | Infrastructure as Code (IaC) | CI/CD Integration ||———————|————————————————|—————————————————-|| Focus | Infrastructure provisioning and configuration | Automated build, test, and deployment || Automation Level | High | Very High || Complexity | Moderate to High | Moderate to High || Use Cases | Defining and managing infrastructure | Automating the entire deployment pipeline || Key Benefit | Repeatability, version control, automation | Faster release cycles, improved code quality, reduced risk |Now, consider a step-by-step procedure for deploying a simple function using the Serverless Framework (a popular framework for building serverless applications):* Install the Serverless Framework: Use npm (Node Package Manager) to install the Serverless Framework globally: `npm install -g serverless`
Create a New Project
Navigate to your desired project directory and create a new serverless project using a template: `serverless create –template aws-nodejs –path my-service` (This creates a project using the AWS Node.js template.)
Configure the `serverless.yml` File
Open the `serverless.yml` file in your project directory. This file defines the function’s configuration, including the runtime, handler, and events that trigger the function. “`yaml service: my-service frameworkVersion: ‘3’ provider: name: aws runtime: nodejs18.x functions: hello: handler: handler.hello events:
http
path: /hello method: get “`* Implement the Function Code: Open the `handler.js` file and implement the function’s logic. “`javascript ‘use strict’; module.exports.hello = async (event) => return statusCode: 200, body: JSON.stringify( message: ‘Go Serverless v3.0! Your function executed successfully!’, input: event, , null, 2 ), ; ; “`* Deploy the Function: Deploy the function to AWS using the Serverless Framework CLI: `serverless deploy`
Test the Function
After deployment, the Serverless Framework will output the API endpoint URL. Access this URL in your browser or using a tool like `curl` to test the function.This process demonstrates how the Serverless Framework uses IaC (through the `serverless.yml` file) to define and deploy the function, automating the provisioning of the necessary AWS resources. While this example doesn’t explicitly showcase CI/CD integration, the Serverless Framework integrates seamlessly with CI/CD platforms, allowing for the automation of these steps as part of a continuous deployment pipeline.
Infrastructure as Code (IaC) in Serverless Deployments
Serverless frameworks revolutionize deployment by embracing Infrastructure as Code (IaC) principles. This approach treats infrastructure management similarly to application code development, enabling automation, version control, and consistent deployments. IaC streamlines the creation, modification, and destruction of cloud resources, critical for the agility and scalability serverless architectures demand.
Leveraging IaC for Resource Provisioning
Serverless frameworks utilize IaC to define and manage the underlying infrastructure required for an application. This encompasses all cloud resources, including functions, APIs, databases, storage buckets, and event triggers. The framework parses configuration files, typically written in formats like YAML or JSON, to understand the desired state of the infrastructure. It then interacts with the cloud provider’s APIs to provision, configure, and manage these resources.
This automated provisioning eliminates manual configuration, reduces errors, and accelerates deployment cycles. The IaC approach ensures that the infrastructure aligns with the application’s code, maintaining consistency and predictability across environments.
Benefits of IaC for Deployment Automation
IaC provides significant advantages for deployment automation in serverless environments. The benefits include:
- Version Control: IaC configurations are text-based files that can be stored in version control systems like Git. This allows for tracking changes, reverting to previous states, and collaborating effectively on infrastructure configurations.
- Repeatability: IaC ensures that infrastructure can be consistently recreated in different environments (e.g., development, staging, production) with identical configurations. This minimizes discrepancies and reduces the risk of deployment failures.
- Automation: IaC enables the automation of infrastructure provisioning and management tasks, eliminating manual processes and reducing the time required for deployments.
- Scalability: IaC facilitates the scaling of resources based on demand. Configurations can be easily modified to increase or decrease the capacity of serverless functions or other cloud services.
- Cost Optimization: IaC allows for the efficient management of resources, ensuring that only necessary resources are provisioned, and unused resources are automatically removed, contributing to cost optimization.
- Compliance and Security: IaC can be used to enforce security best practices and compliance requirements by defining and enforcing infrastructure configurations that adhere to specific standards.
Examples of IaC Configurations
Serverless frameworks often employ YAML or JSON for defining infrastructure configurations. These configurations describe the resources to be created, their properties, and their relationships.
Here’s an example of a simplified YAML configuration for deploying a serverless function using the Serverless Framework:
service: my-serviceprovider: name: aws runtime: nodejs18.x region: us-east-1functions: hello: handler: handler.hello events: -http: path: /hello method: get In this example:
service: my-servicedefines the name of the service.provider:specifies the cloud provider (AWS), runtime (Node.js 18.x), and region.functions:defines the serverless function named “hello.”handler: handler.hellospecifies the function’s entry point.events:defines the trigger for the function (an HTTP GET request to the /hello path).
A similar configuration can be expressed in JSON:
"service": "my-service", "provider": "name": "aws", "runtime": "nodejs18.x", "region": "us-east-1" , "functions": "hello": "handler": "handler.hello", "events": [ "http": "path": "/hello", "method": "get" ] These configurations, whether in YAML or JSON, are interpreted by the serverless framework to provision the necessary AWS resources (e.g., Lambda function, API Gateway endpoint) and configure their relationships. When the serverless framework deploys, it creates the resources described in the configuration file, and the application becomes operational.
CI/CD Integration with Serverless Frameworks
Serverless frameworks significantly streamline the integration with Continuous Integration and Continuous Deployment (CI/CD) pipelines, enabling automated build, test, and deployment processes. This integration is crucial for efficient software development lifecycles, allowing developers to rapidly iterate and release updates with minimal manual intervention. By leveraging CI/CD, serverless applications can benefit from improved reliability, faster release cycles, and reduced operational overhead.
Integration with CI/CD Pipelines
Serverless frameworks facilitate seamless integration with CI/CD systems through various mechanisms, allowing for automated deployment and management of serverless functions and associated resources. This integration often involves utilizing command-line interfaces (CLIs) provided by the serverless framework, which can be incorporated into CI/CD scripts to automate tasks such as building, testing, and deploying code changes. Moreover, frameworks support various deployment strategies like blue/green deployments, which further enhances the robustness and resilience of the application.
The ability to automate these processes is essential for maintaining a continuous delivery pipeline, where code changes can be rapidly and reliably released to production.
Setting Up a CI/CD Pipeline for Automated Deployments
Setting up a CI/CD pipeline for serverless deployments involves several key steps, from code repository integration to automated testing and deployment. The process typically starts with integrating the code repository (e.g., GitHub, GitLab, Bitbucket) with a CI/CD platform (e.g., AWS CodePipeline, Azure DevOps, Jenkins, CircleCI). When code changes are pushed to the repository, the CI/CD pipeline is triggered, initiating the build, test, and deployment stages.
Each stage in the pipeline performs specific actions, such as building the application, running unit and integration tests, and deploying the serverless functions and infrastructure.
Stages in a CI/CD Pipeline for Serverless Deployment
The following table Artikels the stages involved in a CI/CD pipeline for serverless deployment. This structure provides a standardized approach, ensuring that each stage is clearly defined and executed consistently. The tools listed are examples, and the specific tools used may vary based on the chosen CI/CD platform and the project’s requirements.
| Stage | Action | Tool | Description |
|---|---|---|---|
| Code Commit/Trigger | Code changes are pushed to the repository, triggering the pipeline. | Git (GitHub, GitLab, Bitbucket) | The CI/CD pipeline is initiated when a code commit or pull request is created or merged. This trigger is the starting point for the automated process. |
| Build | Build the application code, including any dependencies. | Serverless Framework CLI, Package Managers (npm, pip) | The build stage compiles the code and packages it along with its dependencies. The Serverless Framework CLI is often used to prepare the application for deployment. |
| Test | Run unit tests, integration tests, and potentially end-to-end tests. | Testing Frameworks (Jest, Mocha, Pytest), CI/CD Platform | Testing is a critical stage, ensuring the code functions as expected. Automated tests are executed to validate the functionality of the serverless functions. If tests fail, the pipeline is stopped. |
| Deploy | Deploy the serverless application and infrastructure to the cloud. | Serverless Framework CLI, Cloud Provider CLI (AWS CLI, Azure CLI, Google Cloud SDK) | The deployment stage involves deploying the serverless functions and associated infrastructure (e.g., API gateways, databases) to the cloud provider. The Serverless Framework CLI is utilized to manage the deployment process, often integrating with the cloud provider’s CLI. This can also involve various deployment strategies, such as blue/green deployments for minimal downtime. |
Common Serverless Frameworks and Their Features
Serverless frameworks offer developers a streamlined approach to building and deploying applications without the complexities of server management. They abstract away infrastructure concerns, allowing a greater focus on writing code and responding to events. This section explores several prominent serverless frameworks, comparing their features and capabilities to aid in informed decision-making for various project needs.
Popular Serverless Frameworks
Several frameworks have gained significant traction in the serverless landscape, each providing a unique set of features and catering to different cloud providers and use cases. Understanding the strengths and weaknesses of each framework is crucial for selecting the most appropriate one for a given project.
- AWS Serverless Application Model (SAM): Developed by Amazon Web Services (AWS), SAM is designed specifically for deploying serverless applications on AWS. It leverages AWS CloudFormation under the hood, providing a declarative way to define and manage infrastructure.
- Serverless Framework: This open-source framework supports multiple cloud providers, including AWS, Azure, Google Cloud Platform, and others. It simplifies the deployment and management of serverless functions and related resources.
- Azure Functions: A serverless compute service offered by Microsoft Azure. Azure Functions allows developers to execute code without managing servers, providing event-driven compute capabilities.
- Google Cloud Functions: Google Cloud’s serverless execution environment. It enables developers to create event-driven functions that respond to various triggers, such as HTTP requests, database changes, and more.
Feature Comparison
A comparative analysis of the features offered by different serverless frameworks reveals their strengths and weaknesses, highlighting the trade-offs involved in selecting a particular framework. The following table provides a concise overview.
| Framework | Supported Programming Languages | Event Sources | Deployment Targets | Key Features |
|---|---|---|---|---|
| AWS SAM | Node.js, Python, Java, Go, C#, Ruby, PowerShell | API Gateway, S3, DynamoDB, Kinesis, SNS, SQS, CloudWatch Events, EventBridge | AWS | Simplified infrastructure definition, integrated with AWS services, local testing support, CloudFormation integration. |
| Serverless Framework | Node.js, Python, Java, Go, C#, Ruby, Swift, Kotlin, PHP | API Gateway, S3, DynamoDB, Kinesis, SNS, SQS, CloudWatch Events, Azure Event Hubs, Google Cloud Pub/Sub, HTTP endpoints | AWS, Azure, Google Cloud Platform, Cloudflare Workers, and more | Multi-cloud support, extensive plugin ecosystem, easy deployment and management, streamlined development workflow. |
| Azure Functions | C#, JavaScript, Python, PowerShell, Java | HTTP triggers, Azure Blob Storage, Azure Queue Storage, Azure Cosmos DB, Event Hubs, Service Bus, Timer triggers | Azure | Tight integration with Azure services, built-in monitoring and logging, easy integration with other Azure services. |
| Google Cloud Functions | Node.js, Python, Go, Java, .NET | HTTP triggers, Cloud Storage, Cloud Pub/Sub, Cloud Firestore, Cloud Storage, Firebase, Cloud Scheduler | Google Cloud Platform | Event-driven architecture, integration with Google Cloud services, automatic scaling, pay-per-use pricing. |
The table above highlights some of the core differences between these frameworks. For example, while AWS SAM is tightly coupled with the AWS ecosystem, offering deep integration with its services, the Serverless Framework provides multi-cloud support, making it suitable for projects that need to deploy across different providers. Azure Functions excels within the Azure environment, offering seamless integration with Azure services.
Google Cloud Functions, similarly, provides excellent integration with Google Cloud services. The choice of framework often depends on the cloud provider preference, the need for multi-cloud support, and the specific requirements of the application. For instance, a company already heavily invested in the AWS ecosystem might find AWS SAM the most natural fit, while a startup experimenting with different cloud providers might prefer the Serverless Framework for its portability.
Serverless Frameworks: Best Practices
Serverless frameworks, while offering significant advantages in deployment automation, require adherence to specific best practices to maximize efficiency, maintainability, and security. These practices encompass all stages of the development lifecycle, from version control to monitoring, ensuring a robust and scalable serverless application. Ignoring these best practices can lead to increased operational costs, debugging challenges, and security vulnerabilities.
Version Control Strategies
Effective version control is paramount for managing changes, collaborating effectively, and enabling rollback capabilities in a serverless environment. Employing a robust version control strategy is crucial for the longevity and maintainability of serverless applications.
- Utilize a Distributed Version Control System (DVCS): Git, being a widely adopted DVCS, allows for local branching, merging, and remote repository synchronization. This enables developers to work independently on features, and then merge their changes seamlessly. Using Git also offers a clear history of changes, allowing for easier debugging and rollback.
- Establish Clear Branching Strategies: Implement a branching strategy such as Gitflow or GitHub Flow. These strategies define how feature branches, development branches, and production branches interact, ensuring a structured workflow for code changes and deployments. For example, Gitflow uses separate branches for features, releases, and hotfixes, making it easier to manage different types of changes.
- Version Control Infrastructure as Code (IaC) Configuration Files: All IaC configuration files (e.g., CloudFormation templates, Terraform configurations, or serverless.yml files) should be version controlled alongside the application code. This ensures that infrastructure changes are tracked and managed in the same way as application code.
- Implement Meaningful Commit Messages: Commit messages should be concise and descriptive, clearly explaining the changes made. Adhering to a commit message convention (e.g., Conventional Commits) improves readability and facilitates automated change log generation. For example, a commit message should clearly state the specific functionality implemented or the bug fixed, along with any relevant context.
Testing Serverless Applications
Thorough testing is essential to ensure the reliability and correctness of serverless applications. The ephemeral nature of serverless functions and the distributed architecture necessitate a multi-layered testing approach.
- Unit Testing: Test individual functions in isolation to verify their logic and behavior. Use mocking frameworks to simulate dependencies and isolate functions for focused testing. This approach allows for testing specific components of a function’s code.
- Integration Testing: Verify the interactions between different functions and services. This involves testing the communication between functions, API gateways, databases, and other resources.
- End-to-End (E2E) Testing: Simulate user interactions to test the entire application flow, from the user interface to the backend services. E2E tests should cover critical user journeys and functionalities.
- Test Automation: Automate tests using testing frameworks like Jest, Mocha, or serverless-specific testing tools. Automation ensures that tests are run consistently and efficiently as part of the CI/CD pipeline.
- Test Driven Development (TDD): Write tests before writing the code. TDD promotes a more robust and testable codebase, improving the overall quality of the application.
Monitoring and Observability in Serverless Environments
Effective monitoring and observability are critical for identifying and resolving issues, optimizing performance, and understanding the behavior of serverless applications. Serverless environments require specific strategies to capture and analyze metrics, logs, and traces.
- Centralized Logging: Aggregate logs from all functions and services into a centralized logging platform (e.g., CloudWatch Logs, Splunk, or Datadog). This allows for easier analysis, troubleshooting, and correlation of events.
- Detailed Metrics Collection: Collect key metrics, such as invocation count, duration, errors, and cold starts, to monitor the performance and health of functions. CloudWatch Metrics, Prometheus, and other monitoring tools can be used to track these metrics.
- Distributed Tracing: Implement distributed tracing to track requests as they traverse multiple functions and services. Tools like AWS X-Ray or Jaeger provide insights into request latency, dependencies, and bottlenecks.
- Alerting and Notifications: Set up alerts based on predefined thresholds for key metrics and error rates. Configure notifications to be sent to the appropriate teams when issues arise.
- Proactive Performance Tuning: Analyze monitoring data to identify performance bottlenecks and optimize function configurations (e.g., memory allocation, timeout settings). Continuously monitor performance metrics and iterate on the application’s design and infrastructure to ensure optimal performance.
Checklist for Efficient Serverless Deployment Automation
This checklist provides a summary of essential practices for efficient serverless deployment automation, acting as a quick reference for developers and operations teams.
- Code Repository: Use a DVCS (e.g., Git) for version control of code and IaC configurations.
- CI/CD Pipeline: Implement a CI/CD pipeline for automated building, testing, and deployment.
- IaC: Utilize IaC (e.g., CloudFormation, Terraform) for infrastructure provisioning.
- Automated Testing: Integrate unit, integration, and E2E tests into the CI/CD pipeline.
- Configuration Management: Manage environment-specific configurations (e.g., API keys, database connection strings) securely.
- Rollback Strategy: Define a rollback strategy for reverting to previous versions in case of deployment failures.
- Monitoring and Alerting: Implement comprehensive monitoring, logging, and alerting.
- Security Best Practices: Apply security best practices, including least privilege access, input validation, and regular security audits.
- Documentation: Maintain clear and up-to-date documentation.
- Cost Optimization: Continuously monitor and optimize costs.
Troubleshooting Serverless Deployment Issues
Serverless deployments, while simplifying infrastructure management, introduce new challenges in troubleshooting. Debugging serverless applications requires a shift in perspective, focusing on distributed tracing, event logs, and the specific constraints of the Function-as-a-Service (FaaS) platform. Identifying and resolving issues promptly is crucial for maintaining application availability and performance.
Common Issues Encountered During Serverless Deployments
A variety of issues can arise during serverless deployments, often stemming from the distributed nature of the architecture and the ephemeral nature of function executions. Understanding these common problems is the first step toward effective troubleshooting.
- Configuration Errors: Incorrectly configured resources, such as IAM roles, API Gateway settings, or database connections, are frequent sources of deployment failures. These errors often manifest as permission denied errors or unexpected behavior in the deployed application.
- Code Errors: Errors within the function code itself, including syntax errors, logical flaws, or exceptions, can lead to function failures. These issues are exacerbated by the stateless nature of functions and the difficulty in replicating the execution environment locally.
- Timeout Issues: Serverless functions have execution time limits. If a function exceeds this limit, it will be terminated, resulting in a timeout error. This is particularly common for functions that perform long-running operations, such as data processing or API calls to slow endpoints.
- Concurrency Limits: Cloud providers impose concurrency limits on serverless functions to manage resource allocation. Exceeding these limits can lead to throttling and request failures. This is especially relevant for applications with high traffic volumes.
- Dependency Issues: Problems with function dependencies, such as missing libraries or incorrect versions, can prevent functions from executing correctly. Managing dependencies in a serverless environment requires careful attention to packaging and deployment.
- Event Triggering Problems: Issues with the event sources that trigger functions, such as incorrect event format or misconfigured event rules, can prevent functions from being invoked. This often results in the application not responding as expected.
- Cold Starts: Serverless functions may experience “cold starts,” where the function’s execution environment needs to be initialized before processing a request. This can lead to increased latency, particularly for infrequently invoked functions.
Techniques for Debugging and Resolving Serverless Deployment Issues
Effective debugging in a serverless environment relies on a combination of techniques, including logging, tracing, and monitoring. These techniques provide insights into function execution and allow developers to pinpoint the root cause of issues.
- Detailed Logging: Implement comprehensive logging within functions to capture relevant information, such as input parameters, function execution flow, and any error messages. Use structured logging formats (e.g., JSON) to facilitate easier analysis. Consider using a centralized logging service like CloudWatch Logs (AWS), Stackdriver Logging (GCP), or Azure Monitor (Azure) for efficient log aggregation and analysis.
- Distributed Tracing: Utilize distributed tracing tools, such as AWS X-Ray, to trace requests as they flow through the serverless application. This enables developers to visualize the interactions between different services and identify performance bottlenecks or error sources. Tracing helps to understand the call chain of different services and identify which one is causing the error.
- Monitoring and Alerting: Set up monitoring dashboards and alerting rules to track key metrics, such as function invocation count, error rates, and latency. This enables proactive identification of issues and timely intervention. Monitoring tools allow for a constant view of the system’s health.
- Local Development and Testing: Utilize local development environments and testing frameworks to simulate the serverless environment and debug functions before deployment. This can help catch many errors early in the development cycle. Tools like the Serverless Framework can aid in local testing.
- Version Control and Rollbacks: Employ version control systems, such as Git, to manage code changes and enable rollbacks to previous versions in case of deployment failures. This minimizes the impact of issues on application availability.
- Reviewing Cloud Provider’s Documentation and Support: Thoroughly consult the documentation of the chosen cloud provider. Understanding the limitations, best practices, and specific error codes is crucial for effective troubleshooting. Use the support channels provided by the cloud provider to get assistance with complex issues.
Examples of Error Messages and Their Possible Causes
Understanding common error messages and their potential causes is critical for rapid issue resolution. The following examples illustrate some typical error scenarios in serverless deployments.
- “ResourceNotFoundException: Function not found”
Possible Causes: The function name is misspelled in the configuration or the function was not deployed correctly. Also, the IAM role associated with the function may not have permission to invoke other resources.
- “AccessDeniedException: User: arn:aws:sts::… is not authorized to perform: lambda:InvokeFunction on resource: arn:aws:lambda:…”
Possible Causes: The IAM role associated with the function does not have the necessary permissions to access other AWS resources (e.g., S3 buckets, DynamoDB tables, API Gateway). Review the IAM role policy to ensure the correct permissions are granted.
- “Task timed out after X seconds”
Possible Causes: The function exceeded the configured timeout duration. This may be due to long-running operations, inefficient code, or external dependencies that are slow to respond. Optimize the function code, increase the timeout (if appropriate), or identify and resolve performance bottlenecks.
- “Internal Server Error”
Possible Causes: This is a generic error that often indicates a problem within the function code or the underlying infrastructure. Check the function logs for more specific error messages. Also, verify the function’s code and its dependencies.
- “InvalidParameterException: The request body could not be parsed as JSON”
Possible Causes: The event payload sent to the function is not in the expected JSON format. Review the event source configuration and the function’s input parameters to ensure they are compatible.
- “ThrottlingException: Rate exceeded”
Possible Causes: The function is being invoked at a rate that exceeds the configured concurrency limits. Consider increasing the concurrency limit or implementing strategies like queueing or retries to handle high traffic volumes.
Serverless Frameworks: Security Considerations
Serverless architectures, while offering numerous benefits like scalability and cost efficiency, introduce a new set of security challenges. Understanding and addressing these challenges is crucial for building secure and reliable serverless applications. This section delves into the security aspects of serverless frameworks, outlining best practices, potential vulnerabilities, and a comprehensive security checklist to bolster the safety of serverless deployments.
Security Best Practices for Serverless Deployments
Implementing robust security measures is paramount in serverless environments. Several best practices can significantly reduce the attack surface and protect sensitive data.
- Principle of Least Privilege: Grant functions only the necessary permissions to access resources. Avoid assigning overly permissive roles, which can expose your application to unnecessary risks. Utilize AWS IAM (Identity and Access Management) or equivalent services in other cloud providers to define granular access control. For example, instead of granting a function full access to an S3 bucket, restrict it to only read and write access to a specific folder within the bucket.
- Input Validation and Sanitization: Validate and sanitize all incoming data to prevent injection attacks, such as SQL injection and cross-site scripting (XSS). Use input validation libraries and frameworks to ensure data conforms to expected formats and types. Sanitize data before storing it in databases or using it in any processing operations.
- Secure Dependencies: Regularly update dependencies, including libraries and frameworks, to patch known vulnerabilities. Utilize dependency management tools and vulnerability scanners to identify and address potential security flaws in your project’s dependencies. Consider using a software composition analysis (SCA) tool to automatically scan your dependencies for vulnerabilities.
- Secret Management: Store sensitive information, such as API keys, database credentials, and passwords, securely. Avoid hardcoding secrets in your code. Utilize secure secret management services, like AWS Secrets Manager, Azure Key Vault, or Google Cloud Secret Manager, to manage and rotate secrets.
- Monitoring and Logging: Implement comprehensive logging and monitoring to detect and respond to security incidents. Collect logs from your serverless functions, API Gateway, and other relevant services. Use security information and event management (SIEM) tools to analyze logs and identify suspicious activities. Set up alerts to notify you of potential security threats.
- Regular Security Audits: Conduct regular security audits and penetration testing to identify vulnerabilities in your serverless applications. This can involve both automated scanning tools and manual code reviews. Penetration testing can simulate real-world attacks to assess the effectiveness of your security measures.
- Network Security: Configure network security appropriately, including using VPCs (Virtual Private Clouds) and security groups to restrict access to your serverless functions and other resources. Consider using API Gateway with private endpoints to restrict access to your API from the public internet.
Potential Security Vulnerabilities and Mitigation Strategies
Serverless architectures are susceptible to various security vulnerabilities. Identifying these vulnerabilities and implementing appropriate mitigation strategies is essential for protecting your applications.
- Injection Attacks: These attacks exploit vulnerabilities in input validation and sanitization. Mitigate these by validating and sanitizing all user inputs, using parameterized queries, and employing output encoding. For example, in a serverless function that interacts with a database, use parameterized queries to prevent SQL injection attacks.
- Denial-of-Service (DoS) Attacks: Serverless functions can be targeted by DoS attacks, which aim to exhaust resources and make your application unavailable. Implement rate limiting, Web Application Firewalls (WAFs), and other mechanisms to protect against DoS attacks. Cloud providers often offer built-in protection against DoS attacks.
- Insecure Dependencies: Using outdated or vulnerable dependencies can expose your application to security risks. Regularly update dependencies, scan for vulnerabilities, and consider using a software composition analysis (SCA) tool. The OWASP Dependency-Check is a good starting point for scanning dependencies.
- Data Breaches: Improperly secured data can lead to data breaches. Employ encryption at rest and in transit, use secure secret management, and implement strong access controls. Use HTTPS for all communications and encrypt sensitive data stored in databases or object storage.
- Function Hijacking: Attackers might attempt to gain control of your functions. Use strong authentication and authorization mechanisms, and regularly review function permissions. Implement multi-factor authentication (MFA) for all users with access to your serverless environment.
- Serverless Function Misconfiguration: Incorrect configuration of serverless functions can create security vulnerabilities. Regularly review and audit function configurations, and adhere to security best practices during deployment. Utilize Infrastructure as Code (IaC) to manage your serverless infrastructure consistently and securely.
Security Checklist for Serverless Applications
A comprehensive security checklist can help ensure the security of your serverless applications. This checklist can be used as a guide during development, deployment, and ongoing maintenance.
- Authentication and Authorization:
- Implement strong authentication mechanisms (e.g., OAuth, JWT).
- Enforce least privilege access control.
- Regularly review and update IAM roles and policies.
- Input Validation and Sanitization:
- Validate all user inputs.
- Sanitize data before processing and storage.
- Use parameterized queries to prevent injection attacks.
- Secret Management:
- Store secrets securely using dedicated secret management services.
- Avoid hardcoding secrets in code.
- Rotate secrets regularly.
- Dependency Management:
- Regularly update dependencies.
- Scan for vulnerabilities in dependencies.
- Use a software composition analysis (SCA) tool.
- Logging and Monitoring:
- Implement comprehensive logging.
- Monitor logs for suspicious activity.
- Set up alerts for security events.
- Network Security:
- Use VPCs and security groups to restrict access.
- Configure API Gateway with private endpoints where applicable.
- Use WAFs to protect against common web attacks.
- Infrastructure as Code (IaC):
- Use IaC to define and manage infrastructure.
- Implement automated security checks in the CI/CD pipeline.
- Regular Security Audits and Penetration Testing:
- Conduct regular security audits.
- Perform penetration testing to identify vulnerabilities.
- Compliance:
- Ensure compliance with relevant security standards and regulations (e.g., GDPR, HIPAA).
- Regularly review and update security policies and procedures.
Closing Summary
In conclusion, serverless frameworks have fundamentally transformed deployment automation, offering a powerful toolkit for building scalable, efficient, and cost-effective applications. By abstracting away infrastructure management, these frameworks empower developers to focus on code, accelerating development cycles and reducing operational burdens. From IaC integration to seamless CI/CD pipelines, the discussed strategies facilitate streamlined deployments and enhanced agility. As serverless technology continues to evolve, understanding these frameworks and their associated best practices is crucial for any developer aiming to optimize their application deployment strategies and embrace the future of cloud computing.
Top FAQs
What is the primary advantage of using a serverless framework?
The primary advantage is the elimination of server management, allowing developers to focus on code and business logic rather than infrastructure maintenance. This results in increased efficiency, reduced operational costs, and faster time-to-market.
How does a serverless framework handle scaling?
Serverless frameworks automatically scale resources based on demand. The cloud provider dynamically allocates and deallocates resources, ensuring optimal performance and cost efficiency without manual intervention.
What are the common triggers for serverless functions?
Common triggers include HTTP requests, scheduled events (cron jobs), database updates, file uploads, and messages from message queues. These triggers initiate the execution of serverless functions in response to specific events.
What is the role of Infrastructure as Code (IaC) in serverless deployments?
IaC allows you to define and manage infrastructure resources (e.g., functions, APIs, databases) as code. This enables version control, repeatability, and automation of infrastructure provisioning, making deployments more consistent and reliable.
How does serverless computing impact costs?
Serverless computing typically results in cost savings because you only pay for the compute time used by your functions. This “pay-per-use” model eliminates the need to pay for idle server capacity, making it more cost-effective than traditional server-based deployments, especially for applications with variable workloads.