In the realm of serverless computing, Lambda function versions and aliases represent critical mechanisms for managing deployments, enabling traffic control, and ensuring application stability. These features provide a robust framework for developers to iterate on code, roll back to previous states, and orchestrate deployments with precision. Understanding the nuances of versions and aliases is paramount for building scalable, resilient, and maintainable serverless applications.
This exploration delves into the core concepts of Lambda function versioning and aliasing, elucidating their roles in the software development lifecycle. We’ll examine the creation and management of versions, the purpose and benefits of aliases, and how these features work in tandem to facilitate sophisticated deployment strategies. Furthermore, the discussion will encompass practical applications, security considerations, and automation techniques, equipping you with the knowledge to leverage these powerful tools effectively.
Lambda Function Versions
Lambda function versions are a critical aspect of managing and deploying serverless applications. They provide a mechanism for maintaining different iterations of a Lambda function’s code and configuration, enabling developers to roll back to previous states, experiment with new features safely, and facilitate various deployment strategies. Understanding versions is fundamental for building robust and scalable serverless applications.
Core Concepts of Lambda Function Versions
Lambda function versions represent a specific, immutable snapshot of a Lambda function’s code and configuration at a particular point in time. Every time you publish a new version of your function, AWS creates a new version with a unique identifier, typically a number, starting from 1. The `$LATEST` version is a special version that always points to the latest code and configuration that you’ve uploaded, regardless of whether it has been explicitly published as a numbered version.
- Immutability: Once a version is created, it cannot be modified. This ensures that deployments are predictable and that you can always revert to a known good state. Changes to the function’s code or configuration create a new version.
- Unique Identifiers: Each version is identified by a unique ARN (Amazon Resource Name), which includes the function name and the version number (e.g., `arn:aws:lambda:REGION:ACCOUNT_ID:function:FUNCTION_NAME:1`). This allows you to target specific versions for invocation, event source mappings, and other services.
- Published Versions: Versions are explicitly published by the developer. This publishing action freezes the code and configuration at that point.
Significance of Versioning in Lambda Functions
Versioning is essential for managing the lifecycle of Lambda functions and provides several key benefits. It facilitates safe deployments, enables rollback capabilities, and allows for different deployment strategies.
- Safe Deployments: By publishing new versions, developers can deploy changes without affecting the currently running production version. This allows for testing and validation of the new code before switching traffic.
- Rollback Capabilities: If a new version introduces bugs or performance issues, you can easily revert to a previous, known-good version. This minimizes downtime and impact on users.
- Deployment Strategies: Versions enable various deployment strategies such as blue/green deployments and canary deployments.
- Isolation: Versions provide isolation. Different versions can have different configurations, such as environment variables or memory allocations, allowing for testing different setups.
Role of Immutable Versions in Lambda Deployments
The immutability of Lambda function versions is a core principle that supports safe and reliable deployments. Because versions are immutable, you can confidently deploy a new version knowing that the previous version will remain unchanged.
- Predictability: Immutable versions ensure that the behavior of a deployed function remains consistent, regardless of any subsequent code changes.
- Reduced Risk: Immutability minimizes the risk of unexpected behavior changes during deployments.
- Simplified Management: Immutable versions simplify management by providing a clear history of changes and enabling easy rollback to a known good state.
Lambda Function Version Lifecycle Illustration
The lifecycle of a Lambda function version can be visualized as a series of snapshots, with each version representing a specific point in time. The `$LATEST` version is always mutable and points to the current working code.
Illustration Description:
Imagine a timeline representing the lifecycle of a Lambda function named “MyFunction”. At the start, the function exists as `$LATEST`, represented by a box. Code is uploaded and configured, and the `$LATEST` version is updated. The developer then decides to publish this as version 1 (V1). V1 becomes an immutable snapshot, represented by a separate box.
Subsequent code changes are uploaded, and `$LATEST` is updated again. Then, the developer publishes this new code as version 2 (V2). V2 becomes another immutable snapshot. Finally, a developer might choose to deploy V2, leaving the original V1 available for rollback if any issues arise. Each version has a unique ARN, and the ability to target specific versions during invocation.
Version Creation and Management
Managing Lambda function versions is crucial for implementing robust deployments, enabling rollback capabilities, and facilitating efficient resource allocation. Proper versioning allows for iterative development and testing without disrupting production environments. This section will explore the processes involved in creating and managing Lambda function versions.
Creating a New Version of a Lambda Function
Creating a new version of a Lambda function essentially captures a snapshot of the function’s code and configuration at a specific point in time. This process does not alter the active function (identified by the `$LATEST` version). Instead, it creates an immutable copy, allowing for the controlled deployment of new features or bug fixes.The process involves the following steps:
1. Access the Lambda Function
Navigate to the AWS Lambda console and select the desired function.
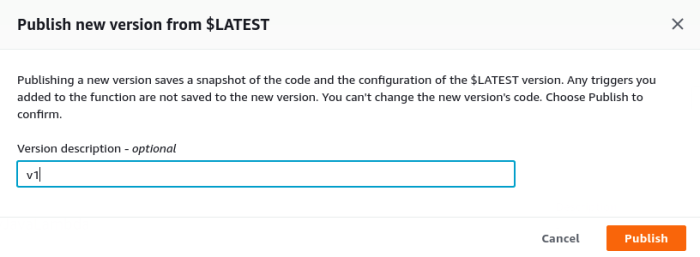
2. Publish a New Version
Within the function’s configuration, locate the “Actions” dropdown menu. Select “Publish new version.”
3. Provide a Description (Optional)
In the publishing dialog, you can optionally provide a descriptive label for the new version to aid in identification.
4. Publish the Version
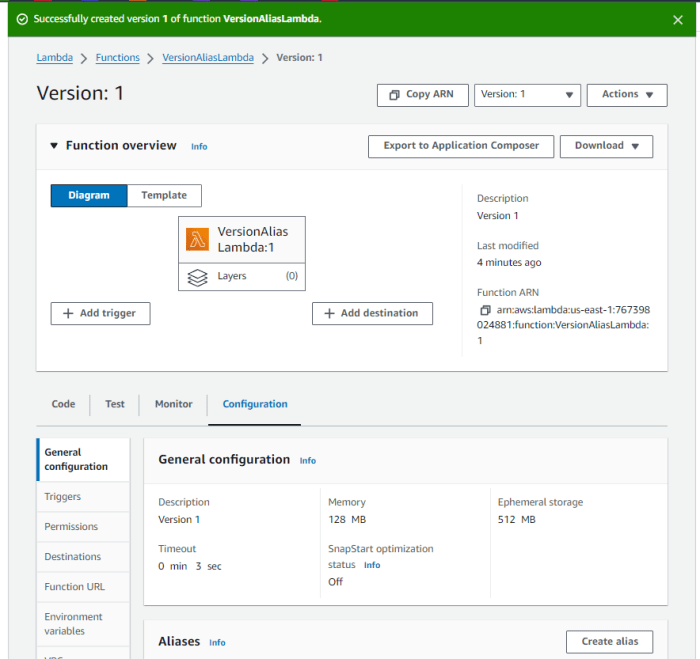
Click “Publish” to initiate the version creation.Upon successful completion, a new version number (e.g., `v2`, `v3`) will be assigned to the function. This version number becomes part of the function’s Amazon Resource Name (ARN), which is essential for referencing and managing specific versions.
Managing Existing Lambda Function Versions Through the AWS Console
The AWS console provides a user-friendly interface for managing Lambda function versions. This interface facilitates the following operations:* Viewing Versions: The console displays a list of all function versions, including the `$LATEST` version and any published versions. Each version’s configuration, code size, and associated aliases are readily accessible.
Configuring Aliases
Aliases are logical pointers that map to specific function versions. The console allows for creating, updating, and deleting aliases. Aliases are vital for traffic management and controlled deployments.
Monitoring Metrics
The console provides access to CloudWatch metrics for each function version, including invocation counts, error rates, and latency. This enables performance analysis and troubleshooting.
Testing Versions
You can invoke specific versions of the function directly from the console using test events, allowing for isolated testing and validation.
Deleting Versions
While deleting versions is possible, it is generally not recommended, as it can impact aliases and deployments. It is important to understand the implications before deleting any version.The console’s intuitive design simplifies the process of managing versions, enabling developers to maintain control over their function deployments.
Creating a New Version Using the AWS CLI
The AWS Command Line Interface (CLI) provides a programmatic method for creating and managing Lambda function versions. This is particularly useful for automating deployments and integrating versioning into CI/CD pipelines. The command used to create a new version is `aws lambda publish-version`.The basic syntax is:“`bashaws lambda publish-version –function-name
`
` (optional) provides a human-readable description of the version.
Example:“`bashaws lambda publish-version –function-name my-lambda-function –description “Updated error handling”“`This command creates a new version of the `my-lambda-function` function and assigns it a version number. The output will include the version’s ARN and other details. The AWS CLI allows for greater automation and integration with other services.
Common Versioning Strategies
Choosing the appropriate versioning strategy depends on the specific application’s requirements and deployment goals. Here are some common strategies:* Blue/Green Deployments: This strategy involves deploying a new version (green) alongside the existing version (blue). Traffic is gradually shifted from the blue version to the green version, allowing for testing and rollback if issues arise. Aliases are typically used to manage traffic routing.
For example, a company might use a blue/green deployment to update its customer-facing Lambda function. They would deploy a new version (green) and test it with a small percentage of live traffic. If the new version performs well, they gradually increase the traffic to the green version, and eventually switch all traffic over. If there are problems, they can quickly switch back to the blue version.* Canary Deployments: Similar to blue/green deployments, canary deployments involve routing a small percentage of traffic to the new version (canary) to test its performance in a production environment.
The canary version is monitored for errors and performance issues. If the canary performs well, traffic is gradually increased until it replaces the original version. Consider a scenario where a financial technology firm is deploying a new version of its fraud detection Lambda function. They might start by routing 1% of all transaction requests to the new version.
They would then monitor the new version’s performance, looking for any errors or increases in latency. If the canary performs well, the firm might increase traffic to 10%, then 25%, and so on, until all traffic is routed to the new version.* Rolling Updates: In a rolling update, the new version is deployed to a subset of the infrastructure, and then the traffic is gradually shifted to the new version.
This is a more gradual approach than blue/green or canary deployments and can be useful when dealing with infrastructure limitations. For example, an e-commerce company deploying a new version of its product catalog Lambda function might use a rolling update. They would first deploy the new version to a small number of servers. Then, they would gradually increase the number of servers running the new version, while simultaneously decreasing the number of servers running the old version.
This approach ensures that the new version is tested in a real-world environment, and minimizes the risk of downtime.* Version Pinning: This strategy involves specifying a specific version of the function to be used by other services or applications. This ensures that those services always use the same version of the function, providing stability and preventing unexpected behavior caused by updates.
A company that uses several Lambda functions to process user data might pin its core data processing function to a specific version to ensure data consistency across its applications. This prevents any unexpected behavior that might be caused by changes to the data processing logic.These strategies offer flexibility in managing Lambda function deployments, enabling developers to release new features, fix bugs, and maintain system stability with greater confidence.
Lambda Function Aliases
Lambda function aliases provide a flexible and controlled mechanism for managing different versions of your Lambda functions, facilitating easier deployment strategies and simplifying traffic management. They act as pointers to specific function versions, allowing you to decouple the function’s underlying code from the client’s access point. This decoupling is crucial for implementing various deployment strategies like blue/green deployments and canary releases, minimizing downtime and risk during updates.
Definition and Purpose of Lambda Function Aliases
Aliases in AWS Lambda are essentially named pointers to specific versions of a Lambda function. Their primary purpose is to enable flexible management of function versions and simplify the process of updating and deploying new code. An alias does not contain any code itself; it simply directs traffic to a specific version. This indirection provides significant advantages in terms of deployment control, rollback capabilities, and traffic management.Aliases serve to:
- Isolate Function Versions: Aliases allow you to have multiple versions of a function active simultaneously. This is essential for implementing strategies like blue/green deployments, where you can have a “blue” version (the current production version) and a “green” version (the new version being tested).
- Facilitate Controlled Rollouts: They enable controlled rollouts, such as canary deployments, where a small percentage of traffic is initially routed to the new version. This allows you to monitor the performance and stability of the new version before fully deploying it.
- Provide Stable Endpoints: Aliases provide stable endpoints for client applications. Instead of clients having to update their configurations every time a new function version is deployed, they can refer to an alias (e.g., “production”, “staging”), which is then updated to point to the appropriate version.
- Support Version-Specific Configuration: Aliases can have their own configurations, such as environment variables, that are specific to the version they point to. This allows you to configure different versions for different environments or testing scenarios.
Benefits of Using Aliases in Lambda Function Deployments
Utilizing aliases in Lambda function deployments offers several key benefits that enhance operational efficiency, reduce risk, and improve the overall reliability of your applications. These benefits stem from the ability to manage traffic flow, control deployment strategies, and facilitate easy rollbacks.The advantages include:
- Simplified Deployment Strategies: Aliases streamline the implementation of advanced deployment strategies. For instance, with blue/green deployments, an alias can be switched to point to the new “green” version once it has been tested and validated, minimizing downtime.
- Reduced Risk of Production Outages: Canary deployments, made possible by aliases, allow for the gradual rollout of new versions, minimizing the impact of potential issues. A small percentage of traffic is initially routed to the new version, and the deployment is rolled back if errors are detected.
- Easy Rollback Capabilities: If a new version of a function causes issues, you can quickly revert to a previous, stable version by simply updating the alias to point to the desired version. This minimizes the impact of errors on end-users.
- Improved Traffic Management: Aliases facilitate fine-grained control over traffic distribution. You can use weighted aliases to route a specific percentage of traffic to different function versions.
- Environment-Specific Configuration: Each alias can have its own set of environment variables. This allows you to configure versions of your function differently for various environments (e.g., development, staging, production).
Differences Between Versions and Aliases
Lambda function versions and aliases, while related, serve distinct purposes and offer different functionalities. Understanding their differences is crucial for effective Lambda function management. Versions represent immutable snapshots of the function’s code and configuration, while aliases are mutable pointers to specific versions.The key differences are:
- Mutability: Versions are immutable; once created, they cannot be changed. Aliases, on the other hand, are mutable and can be updated to point to different versions.
- Purpose: Versions provide a way to track different code revisions, while aliases provide a way to manage traffic and implement deployment strategies.
- Direct Invocation: Versions can be invoked directly using a specific ARN (Amazon Resource Name), which includes the version number. Aliases are invoked through a stable ARN that does not include the version number.
- Configuration: Versions inherit the configuration of the base function at the time of their creation. Aliases can have their own configurations, such as environment variables, that override the function’s default settings.
Comparison of Lambda Function Versions and Aliases
This table provides a comparative analysis of Lambda function versions and aliases, highlighting their key characteristics and functionalities across various criteria. This comparison clarifies the distinct roles of each component in managing and deploying Lambda functions.
| Criteria | Lambda Function Version | Lambda Function Alias | Purpose | Mutability |
|---|---|---|---|---|
| Definition | An immutable snapshot of a function’s code and configuration. | A named pointer to a specific function version. | To track different code revisions. | To manage traffic and deployment strategies. |
| Mutability | Immutable (cannot be changed after creation). | Mutable (can be updated to point to a different version). | ||
| Invocation | Invoked using an ARN that includes the version number. | Invoked using a stable ARN (without the version number). | ||
| Configuration | Inherits the configuration of the base function at the time of version creation. | Can have its own configuration (e.g., environment variables) that overrides the function’s default settings. |
Alias Creation and Configuration
Lambda function aliases provide a mechanism for managing different versions of a function in a controlled manner, enabling features like blue/green deployments and canary releases. This section details the process of creating and configuring aliases, including traffic weighting, for effective function version management.
Creating a New Alias for a Lambda Function
Creating a new alias involves assigning a human-readable name to a specific version of a Lambda function. This alias acts as a pointer to that version.To create an alias:
- Access the Lambda function in the AWS Management Console or use the AWS CLI.
- Navigate to the “Aliases” tab within the function’s configuration.
- Click the “Create alias” button.
- Provide a descriptive name for the alias (e.g., “PROD”, “BETA”, “CANARY”).
- Select the function version to associate with the alias. This can be either the latest published version ($LATEST) or a specific version number (e.g., “1”, “2”).
- Optionally, add a description to clarify the alias’s purpose.
- Click “Create”.
The alias is now created, and all invocations targeted at this alias will execute the specified function version. For example, if an alias named “PROD” is associated with version “2”, all requests sent to the function’s ARN using the “PROD” alias will invoke version “2”.
Configuring an Alias with Specific Function Versions
Configuring an alias involves associating it with a particular version of a Lambda function. This association is crucial for controlling which version is executed when the alias is invoked. The initial creation step directly addresses this, but understanding the configuration’s implications is paramount.To configure an alias with a specific function version, the following steps are performed:
- Access the Lambda function in the AWS Management Console or through the AWS CLI.
- Navigate to the “Aliases” tab.
- Select the alias you wish to configure.
- In the alias configuration, you’ll find a setting that specifies the function version associated with the alias.
- Modify this setting to point to the desired function version (e.g., version “3” instead of version “2”).
- Save the changes.
After saving, all invocations using that alias will now execute the newly associated function version. This is a fundamental operation in deployment strategies where a new version needs to be gradually rolled out.
Assigning Traffic Weights to Different Function Versions Using Aliases
Assigning traffic weights to different function versions using aliases allows for controlled and gradual deployments, such as canary releases or blue/green deployments. This enables the routing of a percentage of incoming traffic to different versions.The core concept involves configuring the alias’s traffic distribution:
- Access the Lambda function in the AWS Management Console or using the AWS CLI.
- Navigate to the “Aliases” tab.
- Select the alias you want to configure for weighted traffic.
- Under the “Traffic Configuration” section (or similar, depending on the AWS console version), you’ll find options to specify traffic weights.
- Add one or more versions to the traffic configuration.
- For each version, specify a percentage of traffic that should be routed to it. The total traffic percentages across all versions should sum up to 100%.
- Save the changes.
For instance, a “CANARY” alias might initially route 10% of the traffic to version “3” and 90% to version “2”. After monitoring the performance of version “3”, the traffic weight can be adjusted (e.g., 50% to version “3” and 50% to version “2”) or all traffic to version “3” can be directed.
Step-by-Step Procedure on How to Configure an Alias with Weighted Traffic Distribution
Configuring an alias with weighted traffic distribution involves defining how incoming requests are distributed across different function versions. This allows for controlled deployments and A/B testing of different versions.The procedure is as follows:
- Access the Lambda Function: Log in to the AWS Management Console and navigate to the Lambda service. Select the specific function for which you want to configure weighted traffic.
- Navigate to the Aliases Tab: Within the function’s configuration, click on the “Aliases” tab.
- Select the Alias: Choose the alias you want to configure for weighted traffic distribution (e.g., “CANARY”, “BETA”). If the alias doesn’t exist, create it first, associating it with a specific function version initially.
- Edit the Alias Configuration: Click the “Edit” button associated with the selected alias. This will bring up the alias configuration settings.
- Configure Traffic Distribution: Look for a section related to traffic distribution or weighted traffic. The specific wording might vary depending on the AWS console’s interface, but the functionality will be similar. It is often labeled as “Traffic Configuration” or “Weighted Traffic”.
- Add Function Versions and Weights: Click “Add Version” and then select the function version you want to include in the traffic distribution. Then, specify the percentage of traffic that should be routed to that version. Repeat this step for each version you want to include. The percentages must add up to 100%.
- Save the Configuration: After setting the traffic weights, click the “Save” button to apply the changes.
- Test the Configuration: Invoke the function using the alias. The AWS console or the AWS CLI can be used to test the distribution. Monitor CloudWatch metrics to verify that the traffic is being distributed according to the specified weights.
- Monitor and Adjust: Continuously monitor the performance and error rates of each function version. Based on the monitoring results, adjust the traffic weights to control the deployment’s rollout. For instance, if version “3” shows a high error rate, reduce its traffic weight.
This process allows for incremental rollouts, where a small percentage of traffic is initially routed to a new version (e.g., 10%), followed by increasing the traffic over time, as the new version proves stable. If issues are detected, the traffic can be quickly reverted to the previous stable version.
Using Aliases for Traffic Management
Aliases are instrumental in managing traffic to different versions of a Lambda function, particularly during deployment and rollback procedures. This capability enables developers to implement strategies like blue/green deployments, minimizing downtime and the risk associated with releasing new code.
Blue/Green Deployments with Aliases
Blue/green deployments leverage aliases to smoothly transition traffic between different function versions. This method involves having two identical environments: the “blue” environment (the current production version) and the “green” environment (the new, updated version). Aliases are used to route traffic to either the blue or green environment, allowing for a gradual and controlled rollout of the new version.
- Deployment Process: The process typically involves the following steps:
- Create a new function version (e.g., version $LATEST, or a numbered version like $1, $2, etc.) representing the updated code (the “green” environment).
- Create an alias (e.g., “staging”) that initially points to the new function version.
- Test the new function version by sending traffic through the “staging” alias to ensure it functions as expected.
- Create an alias (e.g., “prod”) that initially points to the original function version (the “blue” environment).
- Gradually shift traffic from the “prod” alias to the “staging” alias by adjusting the alias configuration. This can be done using weighted traffic distribution.
- Once the new function version is fully validated and all traffic is routed to it, the “staging” alias can be renamed to “prod” or the “prod” alias can be updated to point to the new function version.
- Benefits: Blue/green deployments with aliases provide several advantages:
- Reduced Downtime: The switch between environments is nearly instantaneous, minimizing service interruption.
- Risk Mitigation: If the new version has issues, traffic can be quickly routed back to the stable “blue” environment.
- Controlled Rollout: Traffic can be gradually shifted to the new version, allowing for monitoring and adjustments.
Traffic Management Examples
Aliases offer flexible traffic management options during deployments, including weighted routing and phased rollouts.
- Weighted Routing: AWS Lambda allows assigning weights to different aliases. For example, you can configure an alias to direct 10% of the traffic to a new version and 90% to the current version. This is achieved by setting the “RoutingConfig” property on the alias. The following example using the AWS CLI shows the configuration of an alias named “prod” with 10% of traffic to version $2 and 90% to version $1.
aws lambda update-alias \ --function-name my-function \ --name prod \ --routing-config ' "AdditionalVersionWeights": "2": 0.1 '
- Phased Rollouts: This approach gradually increases the traffic to the new version over time. This allows for monitoring performance and catching potential issues before affecting all users. For example, initially, only a small percentage of traffic is routed to the new version. The percentage is then increased incrementally, monitoring for errors and performance degradation at each stage. This approach is particularly useful for large-scale deployments where a complete switchover might be risky.
- Canary Deployments: A canary deployment is a specific type of phased rollout. It involves releasing the new version to a small subset of users (“canary” users) before wider deployment. This allows for identifying and fixing any problems before the entire user base is affected. The traffic is routed to the canary version by an alias.
Rolling Back with Aliases
Aliases facilitate swift rollbacks to a previous function version in case of issues with a new deployment.
- Rollback Procedure: The process is straightforward:
- Identify the previous stable function version (the “blue” environment).
- Update the alias that serves production traffic (e.g., “prod”) to point back to the stable version. This is usually done by updating the alias configuration to change the function version the alias points to.
- Monitor the function’s performance and logs to ensure the rollback was successful.
- Example: If version $2 of a function is experiencing errors, and the “prod” alias is pointing to it, you can quickly roll back by updating the “prod” alias to point to version $1. This immediately redirects all traffic to the stable version, minimizing impact on users.
Diagram: Blue/Green Deployment Strategy
The following diagram illustrates a blue/green deployment strategy using aliases.
+---------------------+ +---------------------+ +---------------------+| Client Requests | --> | Load Balancer | --> | Lambda Function |+---------------------+ +---------------------+ +---------------------+ | | | Alias: "prod" |-----> Function Version $1 (Blue - Stable) | (100% Traffic) | | | | Alias: "staging" |-----> Function Version $2 (Green - New) | (0% Traffic) | +---------------------+ | | V (Deployment Steps) | |+---------------------+ +---------------------+ +---------------------+| Client Requests | --> | Load Balancer | --> | Lambda Function |+---------------------+ +---------------------+ +---------------------+ | | | Alias: "prod" |-----> Function Version $2 (Green - New) | (100% Traffic) | | | | Alias: "staging" |-----> Function Version $1 (Blue - Stable) | (0% Traffic) | +---------------------+
The diagram illustrates the traffic flow during a blue/green deployment.
Initially, the “prod” alias directs all traffic to Function Version $1 (the “blue” environment). The “staging” alias points to Function Version $2 (the “green” environment) with no traffic. During the deployment, the load balancer sends requests to the Lambda function, which routes them through the “prod” alias to the current production version. After the testing phase, the “prod” alias is updated to point to Function Version $2, effectively switching all traffic to the new version.
The “staging” alias can be updated to point to the older version if a rollback is necessary.
Versioning and Aliases in Practice
The strategic combination of Lambda function versions and aliases provides a robust mechanism for managing serverless application deployments, facilitating controlled rollouts, and enabling effective traffic management. This approach allows developers to mitigate risks associated with updates, maintain application stability, and optimize resource utilization. This section will explore practical applications, common use cases, best practices, and common pitfalls associated with leveraging versions and aliases in real-world scenarios.
Real-World Examples of Versioning and Aliases Used Together
Versioning and aliases are frequently employed in tandem to streamline the deployment and management of serverless applications. Several illustrative examples highlight their synergistic benefits.
* Blue/Green Deployments: This strategy utilizes two aliases, typically “production” (pointing to a stable version) and “staging” (pointing to a new, potentially unstable version). New code is initially deployed to the “staging” alias. Once validated, traffic can be gradually or immediately shifted from “production” to “staging.” This allows for a controlled rollout, enabling rollback to the previous version if issues arise.
For example, a retail website could use this approach to update its product catalog service.
* Canary Deployments: This technique involves routing a small percentage of production traffic to a new function version (e.g., a version 2 alias) while the majority of traffic continues to use the stable version (e.g., a version 1 alias). This allows for monitoring of the new version’s performance under real-world load before a full rollout. If the canary version performs poorly, the traffic can be rolled back quickly.
A social media platform could use this to test a new feature, such as an improved search algorithm.
* A/B Testing: Aliases facilitate A/B testing by directing different user segments to different function versions. One alias (e.g., “feature-A”) could point to a version with feature A enabled, while another alias (e.g., “feature-B”) points to a version with feature B enabled. This allows for comparing the performance and user engagement of each feature. A marketing analytics company could use this to compare different ad campaign strategies.
Common Use Cases for Versioning and Aliasing in Serverless Applications
The versatility of Lambda function versions and aliases makes them applicable across a broad spectrum of serverless application scenarios.
* Continuous Integration and Continuous Deployment (CI/CD): Versioning and aliases are integral to automated deployment pipelines. Each code change can result in a new function version, and aliases manage the routing of traffic through various stages (development, staging, production).
* API Gateway Integration: When used with API Gateway, aliases enable the creation of multiple API endpoints that map to different function versions. This supports multiple API versions or testing different API implementations.
* Rollback Capabilities: In the event of a deployment failure or performance degradation, aliases provide a mechanism for quickly rolling back to a previous, known-good function version. This minimizes downtime and the impact on users.
* Testing and Development: Aliases allow developers to isolate and test specific function versions without affecting production traffic. This is particularly useful for debugging and experimenting with new features.
* Cost Optimization: By carefully managing function versions and traffic routing, organizations can optimize resource utilization and minimize unnecessary costs. For example, scaling a specific version to handle increased traffic.
Best Practices for Managing Lambda Function Versions and Aliases
Adopting best practices is critical to ensure the effective and reliable use of Lambda function versions and aliases.
* Version Immudability: Treat function versions as immutable. Once a version is created, do not modify its code or configuration. Deploy new code as a new version.
* Descriptive Naming: Use meaningful names for aliases (e.g., “production,” “staging,” “dev”) and versions (e.g., “v1,” “v2,” or using semantic versioning). This enhances readability and maintainability.
* Automated Deployments: Implement automated deployment pipelines that handle version creation, alias updates, and traffic management. This reduces manual errors and improves deployment speed.
* Monitoring and Alerting: Establish comprehensive monitoring and alerting to track the performance of different function versions. Set up alerts to detect errors, latency issues, or resource consumption anomalies.
* Traffic Weighting: Use traffic weighting strategically to control the percentage of traffic routed to different function versions. This is particularly useful for canary deployments and gradual rollouts.
* Infrastructure as Code (IaC): Define and manage Lambda functions, versions, and aliases using Infrastructure as Code tools (e.g., AWS CloudFormation, Terraform). This promotes consistency, repeatability, and version control.
* Regular Testing: Conduct thorough testing of all function versions before deploying them to production. Include unit tests, integration tests, and performance tests.
Common Mistakes to Avoid When Using Versions and Aliases
Avoiding common pitfalls is essential to maximize the benefits of Lambda function versions and aliases.
* Modifying Existing Versions: Never directly modify a published version. This breaks the immutability principle and can lead to unexpected behavior.
* Incorrect Traffic Weighting: Improperly configured traffic weighting can lead to performance degradation, errors, or an uneven distribution of traffic.
* Lack of Monitoring: Failing to monitor the performance of different function versions can result in undetected issues that impact users.
* Ignoring Rollback Strategies: Without a clear rollback strategy, a deployment failure can lead to significant downtime and user impact.
* Insufficient Testing: Deploying untested function versions to production can introduce bugs and instability.
* Over-reliance on Manual Processes: Manual deployments and configuration changes are prone to errors and can slow down development cycles.
* Ignoring Resource Limits: Exceeding Lambda function resource limits (memory, execution time) can lead to failures.
Versioning and Aliasing with Event Sources
Lambda function versions and aliases provide powerful mechanisms for managing deployments, testing, and traffic routing. Integrating these features with event sources allows for precise control over how different versions or aliases of a Lambda function respond to incoming events. This is crucial for implementing strategies like blue/green deployments, canary releases, and controlled rollbacks, ensuring service availability and minimizing the impact of potential issues.
Configuring Event Sources to Trigger Specific Lambda Function Versions or Aliases
Configuring event sources involves specifying the target Lambda function, along with options to direct events to a particular version or alias. This is typically done during the event source creation or configuration process within the AWS Management Console, AWS CLI, or Infrastructure as Code (IaC) tools like CloudFormation or Terraform.
The primary mechanism for directing events is the function ARN (Amazon Resource Name). The function ARN includes the function name and, crucially, the version or alias.
- Directing Events to a Specific Version: When using a version, the ARN includes the version number (e.g., `arn:aws:lambda:REGION:ACCOUNT_ID:function:FUNCTION_NAME:1`). Any events triggered through this ARN will always invoke that specific version of the function. This guarantees that the function’s behavior remains consistent with the code deployed to that version. This is critical for scenarios where backward compatibility must be maintained.
- Directing Events to an Alias: When using an alias, the ARN includes the alias name (e.g., `arn:aws:lambda:REGION:ACCOUNT_ID:function:FUNCTION_NAME:ALIAS_NAME`). The alias then points to a specific version or a weighted distribution of versions. This provides flexibility in traffic management. For example, an alias named “PROD” might always point to the latest stable version, or it might gradually shift traffic from an older version to a newer one during a deployment.
- Event Source-Specific Configuration: The exact configuration steps vary depending on the event source. For example, configuring an S3 bucket trigger to invoke a specific version requires specifying the function ARN with the version number. For API Gateway, the integration configuration explicitly references the Lambda function ARN, including the version or alias.
Integrating API Gateway with Different Lambda Aliases
API Gateway facilitates the creation of REST, HTTP, and WebSocket APIs. Integration with Lambda functions using aliases enables several deployment strategies.
For instance, you can create an API Gateway stage for each alias, such as “dev,” “staging,” and “prod,” and map each stage to a different Lambda alias.
- Deployment and Testing: The “dev” stage can be mapped to a “DEV” alias, pointing to the latest development version of the Lambda function. Developers can deploy code, test it through the “dev” stage, and iterate quickly without affecting production.
- Staging and Validation: The “staging” stage can be mapped to a “STAGING” alias, which points to a version that has been thoroughly tested. This allows for user acceptance testing (UAT) or pre-production validation before deploying to production.
- Production Deployment: The “prod” stage is mapped to the “PROD” alias, which points to the stable, production-ready version of the Lambda function. This setup ensures that production traffic always hits the tested and stable code.
- Traffic Management: API Gateway allows you to define stages and their associated configurations. By updating the alias associated with a stage, you can redirect traffic. For example, during a blue/green deployment, the “PROD” stage might initially point to the “BLUE” alias (representing the current production version). When a new version (GREEN) is ready, the “PROD” alias can be updated to point to “GREEN.” This shift is instantaneous, and API Gateway handles the routing.
- Example: Consider an API Gateway endpoint `/users`. The “PROD” stage is configured to invoke `arn:aws:lambda:REGION:ACCOUNT_ID:function:my-function:PROD`. The “DEV” stage might invoke `arn:aws:lambda:REGION:ACCOUNT_ID:function:my-function:DEV`. The “PROD” alias can be updated to redirect the traffic from one version to another with minimal downtime.
Integrating Other AWS Services (e.g., S3, DynamoDB) with Lambda Versions or Aliases
Other AWS services, such as S3 and DynamoDB, can be configured to trigger Lambda functions. The same principles of using function ARNs with version or alias specifications apply.
- S3 Event Triggers: S3 can be configured to trigger a Lambda function upon object creation, deletion, or modification. The trigger configuration requires specifying the function ARN. By using a version-specific ARN, you can ensure that a specific version of the function processes S3 events. Using an alias ensures a controlled environment for processing events.
- DynamoDB Streams: DynamoDB Streams capture changes to a DynamoDB table. You can configure a Lambda function to process these changes. The Lambda function is invoked for each change record. The trigger configuration specifies the function ARN, including the version or alias. This enables processing of changes with a specific version or alias.
For example, you might have a “PROD” alias that processes production data and a “STAGING” alias for processing data in the staging environment.
- Example: An S3 bucket is configured to trigger a Lambda function (`my-function`). The trigger configuration uses the ARN `arn:aws:lambda:REGION:ACCOUNT_ID:function:my-function:1` (version 1). All new object uploads to the bucket will be processed by version
1. Later, you deploy a new version (version 2). To use the new version, you update the S3 trigger to use the ARN `arn:aws:lambda:REGION:ACCOUNT_ID:function:my-function:2`, or update the alias to point to version 2.
Diagram Illustrating the Integration of an Event Source with Multiple Lambda Aliases
The diagram illustrates the integration of an API Gateway with two Lambda aliases, “PROD” and “DEV”.
Diagram Description:
The diagram depicts the following elements:
- API Gateway: Represented as a rectangular box, serving as the entry point for incoming requests.
- “PROD” Alias: Represented as a rectangular box, pointing to a specific Lambda function version (e.g., version 1). It handles live production traffic.
- “DEV” Alias: Represented as a rectangular box, pointing to a different Lambda function version (e.g., version 2 or a different version). It is used for development and testing purposes.
- Lambda Function: The core component, represented as a box, which contains different versions.
- Traffic Flow: Arrows indicate the flow of traffic. Requests from API Gateway are routed to either the “PROD” or “DEV” alias based on the API Gateway configuration. Each alias then invokes its associated Lambda function version.
Key Relationships:
- API Gateway routes traffic to the Lambda function based on the configured stage and associated alias.
- The “PROD” alias receives live traffic and invokes a stable Lambda function version.
- The “DEV” alias handles development and testing and invokes a different Lambda function version.
Monitoring and Logging
Monitoring and logging are critical for understanding the behavior of Lambda function versions and aliases, enabling performance optimization, and facilitating efficient troubleshooting. Robust monitoring and logging practices provide insights into function execution, identify potential bottlenecks, and ensure application stability. They allow developers to proactively address issues and maintain the desired service level agreements (SLAs).
Monitoring Performance of Lambda Function Versions and Aliases
Monitoring the performance of Lambda function versions and aliases involves tracking key metrics to identify performance trends and anomalies. This includes observing execution duration, invocation counts, error rates, and other relevant indicators. Monitoring enables developers to compare the performance of different versions and aliases, allowing for informed decisions regarding traffic routing and version deployment.
- Utilizing CloudWatch Metrics: CloudWatch provides a comprehensive set of metrics for Lambda functions. These metrics, accessible through the CloudWatch console or API, are automatically generated for each function, version, and alias. Developers can create dashboards and set up alarms based on these metrics to monitor performance and receive notifications when thresholds are exceeded.
- Leveraging X-Ray for Tracing: AWS X-Ray provides a detailed view of the execution path of a Lambda function, including interactions with other AWS services. By enabling X-Ray tracing, developers can identify performance bottlenecks within the function’s code and the services it interacts with. This is particularly useful for diagnosing issues related to latency and errors.
- Implementing Custom Metrics: In addition to the standard metrics provided by CloudWatch, developers can create custom metrics to track specific aspects of their function’s performance. This is achieved by using the CloudWatch client library within the Lambda function code to publish custom metrics. Custom metrics can provide insights into application-specific performance characteristics.
Logging Execution Details of Different Versions and Aliases
Logging execution details is essential for understanding the behavior of Lambda functions, including version-specific behavior. Effective logging provides valuable information for debugging, auditing, and performance analysis. The logging configuration is crucial for managing log volume and ensuring efficient troubleshooting.
- Using CloudWatch Logs: Lambda functions automatically send logs to CloudWatch Logs. Each invocation generates a log stream containing execution details, including function logs, error messages, and any output from the function’s code. Developers can configure log groups and retention policies to manage the logs effectively.
- Version-Specific Logging: When working with multiple versions and aliases, it’s important to differentiate logs from each version. The Lambda service automatically includes metadata in the log messages, such as the function version and alias. This allows developers to filter and analyze logs specific to a particular version or alias.
- Structured Logging: Employing structured logging formats, such as JSON, enhances the ability to analyze logs. Structured logs make it easier to search, filter, and extract specific data points. Libraries are available for various programming languages to facilitate structured logging within Lambda functions.
- Log Filtering and Analysis: Tools like CloudWatch Logs Insights enable powerful log analysis. Developers can use queries to filter logs based on various criteria, such as version, alias, error messages, or specific log content. This enables quick identification of issues and performance analysis.
CloudWatch Metrics for Lambda Function Versions and Aliases
CloudWatch provides a rich set of metrics for monitoring Lambda functions, including version-specific metrics. These metrics offer valuable insights into the performance and health of the function. Understanding these metrics is crucial for effective monitoring and troubleshooting.
The following table lists important CloudWatch metrics for Lambda function versions and aliases:
| Metric Name | Description | Unit | Importance |
|---|---|---|---|
| Invocations | The number of times the function was invoked. | Count | Essential for understanding function usage and traffic volume. |
| Errors | The number of function invocations that resulted in an error. | Count | Indicates the health of the function and potential code issues. |
| Throttles | The number of times the function was throttled due to concurrency limits. | Count | Indicates potential scaling issues or resource constraints. |
| Duration | The amount of time the function took to execute. | Milliseconds | Critical for performance analysis and identifying latency issues. |
| ConcurrentExecutions | The number of function instances running concurrently. | Count | Indicates the level of concurrency and resource utilization. |
| IteratorAge | The age of the last record processed in seconds when using an event source that is an iterator (e.g., Kinesis, DynamoDB Streams). | Seconds | Indicates how far behind the function is in processing events. |
| DeadLetterErrors | The number of times the function was unable to send an event to a dead-letter queue. | Count | Indicates issues with dead-letter queue configuration or accessibility. |
| UnreservedConcurrentExecutions | The number of concurrent executions that are not using reserved concurrency. | Count | Helps to monitor how much unreserved concurrency is available. |
Security Considerations
Using Lambda function versions and aliases introduces several security implications that must be carefully managed to protect sensitive data and maintain the integrity of applications. Proper configuration and adherence to security best practices are crucial to mitigate potential risks.
Security Implications of Using Different Lambda Function Versions and Aliases
Versioning and aliasing, while offering flexibility, can inadvertently create security vulnerabilities if not handled correctly. These functionalities can expand the attack surface of a system.
- Increased Attack Surface: Each new version or alias represents a distinct entry point for potential threats. If not properly secured, an attacker could exploit vulnerabilities in any specific version or alias. For example, if an outdated version is accessible through an alias, it could be targeted by attackers.
- Configuration Drift: Misconfigurations across different versions or aliases can lead to inconsistencies in security settings. For instance, one version might have overly permissive IAM roles, while another is correctly configured. This drift can be exploited if an attacker discovers the misconfigured version.
- Access Control Complexity: Managing IAM permissions for multiple versions and aliases can be complex, increasing the risk of granting excessive privileges. A mistake in a policy could inadvertently allow unauthorized access to sensitive resources.
- Data Exposure: Inadequate versioning and alias management can lead to unintentional data exposure. For example, if an alias points to a version that logs sensitive information, that data could be accessible to unauthorized parties.
- Versioning Challenges: When new versions are deployed, it’s essential to verify the code’s security. An attacker could use vulnerabilities in the updated version if the security verification is insufficient.
Best Practices for Securing Lambda Function Versions and Aliases
Implementing a robust security posture for Lambda function versions and aliases involves several key practices.
- Principle of Least Privilege: Grant only the necessary permissions to each Lambda function version and alias. Avoid using overly permissive IAM roles, and instead, define granular permissions tailored to the specific needs of each version or alias.
- Regular Security Audits: Conduct regular security audits of Lambda functions, including all versions and aliases. This helps identify and remediate vulnerabilities and misconfigurations. Audits should include code reviews, penetration testing, and vulnerability scanning.
- Version Control and Code Reviews: Utilize version control systems like Git to track changes to Lambda function code. Implement a code review process to ensure that all code changes are reviewed by peers before deployment.
- Automated Security Scanning: Integrate automated security scanning tools into the CI/CD pipeline to identify vulnerabilities in the code and dependencies. This can help catch security issues early in the development process.
- Use of Secure Runtime Environments: Ensure that Lambda functions are running on the latest secure runtime environments. Regularly update the function’s runtime to patch security vulnerabilities.
- Encryption of Sensitive Data: Encrypt sensitive data at rest and in transit. Use AWS KMS (Key Management Service) to manage encryption keys.
- Monitoring and Logging: Implement comprehensive monitoring and logging to detect and respond to security incidents. Monitor for unauthorized access attempts, unusual activity, and errors. Use tools like AWS CloudWatch and AWS CloudTrail to collect and analyze logs.
- Immutable Infrastructure: Treat infrastructure as immutable. This means that once a Lambda function version is deployed, it should not be modified. Instead, deploy new versions with the necessary changes.
Managing IAM Permissions for Different Lambda Function Versions and Aliases
Effective IAM permission management is critical for securing Lambda function versions and aliases.
- Role-Based Access Control (RBAC): Use IAM roles to define the permissions for each Lambda function version and alias. Assign roles to functions based on their specific responsibilities.
- Version-Specific Permissions: Define IAM permissions specific to each Lambda function version. This allows you to control access to resources based on the version being used. For example, a testing version might have access to a development database, while a production version accesses a production database.
- Alias-Specific Permissions: Similarly, define IAM permissions for each alias. This is especially useful for controlling access to resources based on the traffic routing configuration. For example, an alias for a canary deployment could have limited access to resources.
- Use of Resource-Based Policies: Consider using resource-based policies, such as those attached to S3 buckets or KMS keys, to further restrict access. This adds an extra layer of security by explicitly granting access to specific resources.
- Least Privilege Principle Enforcement: Always apply the principle of least privilege when defining IAM permissions. Only grant the necessary permissions required for each version or alias to function correctly. Regularly review and update IAM policies to ensure they remain aligned with the principle of least privilege.
- IAM Policy Versioning: Implement versioning for IAM policies to track changes and easily revert to previous configurations if necessary. This can help in incident response and troubleshooting.
- Centralized Policy Management: Utilize centralized policy management tools to streamline the process of creating, managing, and enforcing IAM policies across all Lambda function versions and aliases.
Versioning and aliasing introduce complexities to access management, necessitating a robust and vigilant approach to security. Failure to implement proper security measures can lead to significant vulnerabilities, including unauthorized data access, service disruption, and potential compromise of the AWS account. Regularly auditing IAM permissions, implementing the principle of least privilege, and employing comprehensive monitoring and logging are critical for safeguarding Lambda function versions and aliases.
Automating Version and Alias Management
Automating the creation and management of Lambda function versions and aliases is crucial for achieving efficient deployment, rollback capabilities, and controlled traffic distribution. This automation minimizes manual intervention, reduces the risk of errors, and allows for consistent and repeatable deployments across different environments. Effective automation is essential for any organization leveraging Lambda functions at scale.
Infrastructure-as-Code for Version and Alias Management
Infrastructure-as-code (IaC) tools provide a declarative approach to defining and managing infrastructure, including Lambda function versions and aliases. This enables consistent, repeatable, and auditable deployments. Using IaC significantly reduces the chances of human error and promotes best practices.
- CloudFormation: AWS CloudFormation is a native IaC service that allows you to define your infrastructure as code using YAML or JSON templates.
- Defining Versions: In CloudFormation, you can specify the `FunctionName` and `PublishVersion` properties of the `AWS::Lambda::Function` resource. Setting `PublishVersion` to `true` automatically creates a new version upon each deployment.
- Creating Aliases: The `AWS::Lambda::Alias` resource is used to create and manage aliases. You define the alias name, the function version it points to (`FunctionVersion`), and optional routing configurations.
- Example (YAML):
Resources: MyLambdaFunction: Type: AWS::Lambda::Function Properties: FunctionName: !Sub "my-function-$AWS::Region" Handler: index.handler Runtime: nodejs18.x Code: ZipFile: | exports.handler = async (event) => return statusCode: 200, body: JSON.stringify('Hello from Lambda!') ; ; PublishVersion: true MyLambdaAlias: Type: AWS::Lambda::Alias Properties: FunctionName: !Ref MyLambdaFunction Name: "PROD" FunctionVersion: !GetAtt MyLambdaFunction.Version - Terraform: Terraform is a popular IaC tool that supports multiple cloud providers, including AWS. It uses a declarative configuration language (HCL – HashiCorp Configuration Language) to define infrastructure.
- Defining Versions: Terraform creates a new version of the Lambda function automatically when changes are made to the `filename` or `source_code_hash` attributes of the `aws_lambda_function` resource, and `publish` attribute is set to `true`.
- Creating Aliases: The `aws_lambda_alias` resource is used to manage aliases. You specify the function name, alias name, and function version.
- Example (HCL):
resource "aws_lambda_function" "example" function_name = "my-function-$data.aws_region.current.name" handler = "index.handler" runtime = "nodejs18.x" filename = "lambda_function_payload.zip" source_code_hash = filebase64sha256("lambda_function_payload.zip") publish = true resource "aws_lambda_alias" "example" name = "PROD" function_name = aws_lambda_function.example.function_name function_version = aws_lambda_function.example.version - Benefits of IaC:
- Version Control: IaC configurations can be stored in version control systems (e.g., Git), enabling tracking of changes and rollbacks.
- Repeatability: The same configuration can be applied to multiple environments (e.g., development, staging, production).
- Automation: IaC integrates seamlessly with CI/CD pipelines, automating the deployment process.
- Consistency: IaC ensures that infrastructure is deployed consistently across all environments.
CI/CD Pipelines for Deploying Lambda Function Versions and Aliases
CI/CD pipelines automate the build, test, and deployment of code changes. When deploying Lambda functions, these pipelines should include steps for creating new versions, updating aliases, and potentially performing traffic shifting. This automation ensures a streamlined and reliable deployment process.
- Pipeline Stages: A typical CI/CD pipeline for Lambda functions includes the following stages:
- Source: Retrieves the latest code from the version control repository (e.g., GitHub, GitLab, AWS CodeCommit).
- Build: Compiles the code (if necessary), packages the code into a deployment package (e.g., a ZIP file), and performs static code analysis.
- Test: Executes unit tests, integration tests, and potentially end-to-end tests.
- Deploy: Deploys the new version of the Lambda function and updates the relevant aliases.
- Monitor: Monitors the deployed function’s performance, logs, and errors.
- Deployment Strategies:
- All-at-Once Deployment: The new version of the function is deployed and the alias is immediately updated to point to it. This is the simplest strategy but can lead to downtime if the new version has issues.
- Canary Deployment: A small percentage of traffic is routed to the new version. If the new version performs well, the traffic is gradually increased. If issues are detected, the traffic is rolled back to the previous version.
- Blue/Green Deployment: Two identical environments (blue and green) are maintained. The new version is deployed to the green environment, and then traffic is switched from the blue to the green environment. This strategy minimizes downtime.
Diagram of a CI/CD Pipeline for Deploying Lambda Function Versions and Aliases
The diagram illustrates a CI/CD pipeline, showing the flow of code changes from source control to a production environment, including steps for versioning and alias management.
Diagram Description: The diagram shows a CI/CD pipeline for deploying Lambda functions. The pipeline begins with a “Source” stage, where code is retrieved from a repository (e.g., GitHub). The code then moves to a “Build” stage, where it’s compiled and packaged. Next is a “Test” stage, where unit and integration tests are run. Following testing, the “Deploy” stage deploys the function to AWS Lambda.
Within the “Deploy” stage, the function is versioned (a new version is created), and an alias (e.g., “PROD”) is updated to point to the new version. A “Monitor” stage follows deployment, collecting metrics and logs from the deployed function. The pipeline incorporates a feedback loop: monitoring data informs future development and deployment cycles.
Last Word
In summary, Lambda function versions and aliases are indispensable components for managing and deploying serverless applications. By mastering these features, developers can achieve greater control over deployments, minimize risk, and improve the overall robustness of their applications. From immutable versions to weighted traffic distribution, the capabilities offered by versions and aliases provide the foundation for building sophisticated and resilient serverless solutions.
As serverless technologies continue to evolve, a deep understanding of these concepts will remain essential for any developer aiming to thrive in this dynamic landscape.
Quick FAQs
What is the primary difference between a Lambda function version and an alias?
A version represents an immutable snapshot of a Lambda function’s code and configuration, while an alias is a pointer that maps to a specific function version, allowing for traffic management and deployment strategies.
Can I directly invoke a Lambda function alias?
Yes, you can invoke a Lambda function alias just like you would invoke a specific version or the latest version. The alias acts as an endpoint, and the underlying version handles the execution.
How do I roll back to a previous version of a Lambda function?
By updating an alias to point to a previous version of the function. This instantly directs all new traffic to the older version.
What happens to existing invocations when I update an alias?
Existing invocations that are in progress will continue to use the version the alias was pointing to at the time the invocation started. New invocations will use the new version the alias points to.
Is it possible to have multiple aliases for a single Lambda function?
Yes, you can create multiple aliases, each pointing to different versions. This allows for complex deployment scenarios, such as blue/green deployments or canary releases.