The journey into infrastructure management has been revolutionized by Infrastructure as Code (IaC), a paradigm shift that treats infrastructure as software. This approach enables the automated provisioning, configuration, and management of computing resources, transforming static and manual processes into dynamic, repeatable, and version-controlled operations. IaC offers a potent arsenal of benefits, including enhanced consistency, reduced errors, and accelerated deployment cycles across diverse target environments.
This exploration delves into the core principles, tools, and best practices of IaC, providing a roadmap for implementing and maintaining infrastructure in a programmatic manner. From selecting the right IaC tools to crafting maintainable code, conducting rigorous testing, and managing deployments, this guide equips you with the knowledge to master the art of infrastructure automation. The goal is to provide a robust understanding of how IaC principles can be leveraged across various environments, including cloud, on-premise, and hybrid setups, to optimize efficiency and enhance operational agility.
Introduction to Infrastructure as Code (IaC) for Target Environments
Infrastructure as Code (IaC) is a paradigm shift in managing and provisioning IT infrastructure. It involves treating infrastructure – servers, networks, load balancers, etc. – as code, allowing for automation, version control, and repeatable deployments. This approach enables consistent, scalable, and efficient infrastructure management across various target environments.
Core Concepts of IaC
IaC revolves around several fundamental concepts that differentiate it from traditional infrastructure management. These concepts contribute to its effectiveness and widespread adoption.
- Declarative vs. Imperative Approaches: IaC can be implemented using declarative or imperative approaches. Declarative IaC focuses on defining the desired state of the infrastructure. The IaC tool then determines how to achieve that state. Imperative IaC specifies the exact steps to build the infrastructure. The declarative approach is generally preferred for its idempotency and ease of management.
- Idempotency: IaC tools should be idempotent, meaning that applying the same configuration multiple times results in the same infrastructure state. This is a critical feature, ensuring that repeated deployments don’t inadvertently cause errors or inconsistencies.
- Version Control: IaC leverages version control systems (e.g., Git) to track changes to infrastructure code. This allows for collaboration, rollback to previous states, and auditing of infrastructure changes.
- Modularity and Reusability: IaC encourages modularity, allowing infrastructure components to be defined as reusable modules or templates. This promotes code reuse, reduces duplication, and simplifies complex infrastructure configurations.
- Automation: IaC automates the provisioning, configuration, and management of infrastructure. This reduces manual effort, minimizes human error, and accelerates deployment cycles.
Brief History of IaC and its Evolution
The evolution of IaC reflects the broader trends in software development and cloud computing. Its origins can be traced back to the early days of automation and scripting.
- Early Automation (Pre-2000s): The earliest forms of IaC involved scripting languages like shell scripts and batch files. These were used to automate basic server setup and configuration tasks.
- Configuration Management Tools (2000s): Tools like Chef, Puppet, and Ansible emerged, offering more sophisticated configuration management capabilities. These tools focused on managing the state of individual servers.
- Cloud Computing and IaC (2010s): The rise of cloud computing spurred the development of IaC tools that could provision entire infrastructure environments. Tools like Terraform and AWS CloudFormation gained prominence, enabling the definition and deployment of infrastructure across multiple cloud providers.
- Modern IaC (Present): Today, IaC is a mature practice, with a wide range of tools and approaches available. IaC is increasingly integrated with DevOps practices, enabling continuous integration and continuous delivery (CI/CD) pipelines for infrastructure.
Benefits of Using IaC in Various Target Environments
IaC offers significant benefits across a range of target environments, including on-premises data centers, public clouds, and hybrid cloud setups. These benefits contribute to increased efficiency, reduced costs, and improved agility.
- Increased Speed and Efficiency: IaC automates infrastructure provisioning, reducing the time required to deploy and configure resources. This accelerates deployment cycles and enables faster time-to-market for applications.
- Reduced Costs: Automation reduces manual effort, minimizing the risk of human error and the associated costs. IaC also enables more efficient resource utilization, optimizing cloud spending.
- Improved Consistency and Reliability: IaC ensures that infrastructure is consistently configured across all environments. This reduces the risk of configuration drift and improves the reliability of applications.
- Enhanced Scalability: IaC allows infrastructure to be easily scaled up or down to meet changing demands. This ensures that applications can handle peak loads and adapt to growth.
- Improved Security: IaC enables the implementation of security best practices across all infrastructure resources. Security configurations can be defined in code and version-controlled, ensuring consistent security posture.
- Enhanced Collaboration: IaC promotes collaboration between development and operations teams. Infrastructure code can be shared and managed using version control systems, facilitating teamwork and knowledge sharing.
- Disaster Recovery and Business Continuity: IaC simplifies disaster recovery by enabling the rapid recreation of infrastructure in a secondary location. Infrastructure can be provisioned quickly in the event of a failure.
Selecting IaC Tools and Technologies
Choosing the right Infrastructure as Code (IaC) tools and technologies is crucial for successful automation and management of target environments. This selection process significantly impacts efficiency, scalability, and maintainability. A well-considered choice aligns with the specific needs of the environment, team expertise, and long-term goals.
Comparing IaC Tools
The landscape of IaC tools is diverse, each with its strengths and weaknesses. A comparative analysis is essential for informed decision-making. The following table offers a comparison of popular IaC tools: Terraform, Ansible, CloudFormation, and Pulumi.
| Tool | Description | Key Features | Pros | Cons |
|---|---|---|---|---|
| Terraform | An infrastructure orchestration tool developed by HashiCorp. It uses a declarative approach to define infrastructure as code. |
|
|
|
| Ansible | An open-source configuration management and orchestration tool. It uses a simple, agentless architecture and YAML for configuration. |
|
|
|
| CloudFormation | A service provided by AWS for defining and managing AWS infrastructure. It uses JSON or YAML templates. |
|
|
|
| Pulumi | An infrastructure as code tool that allows you to define infrastructure using general-purpose programming languages. |
|
|
|
Factors for Choosing an IaC Tool
Selecting the right IaC tool involves careful consideration of several factors. These factors influence the tool’s suitability for a specific target environment and the overall success of IaC implementation.
- Target Environment: The cloud provider (AWS, Azure, GCP), on-premise infrastructure, or hybrid environment dictates tool compatibility. For instance, CloudFormation is specifically designed for AWS.
- Team Expertise: The team’s existing skill set is a critical factor. Tools like Ansible, with its YAML-based configuration, may be easier for teams familiar with scripting. Pulumi, requiring programming language knowledge, suits teams with software development experience.
- Infrastructure Complexity: Complex environments with intricate dependencies and requirements may benefit from tools with robust features for state management and orchestration, such as Terraform.
- Community Support and Documentation: A strong community and comprehensive documentation are essential for troubleshooting, learning, and staying current with best practices. Terraform and Ansible, with their large communities, excel in this area.
- Tool’s Ecosystem and Integrations: The availability of providers, modules, and integrations with other tools within the existing DevOps toolchain impacts efficiency. Terraform, with its extensive provider support, often leads in this aspect.
- Scalability and Performance: Consider the tool’s ability to handle large-scale infrastructure deployments and manage changes efficiently. Terraform is well-regarded for its scalability.
- Cost: While most IaC tools are open-source, the cost of associated services (e.g., cloud provider resources) and the time spent learning and implementing the tool should be considered.
Role of Configuration Management Tools in IaC
Configuration management tools play a crucial role in the broader IaC ecosystem. They focus on the consistent and automated configuration of software and systems after the infrastructure has been provisioned.
- Post-Provisioning Configuration: IaC tools like Terraform or CloudFormation are typically used to provision the infrastructure (e.g., virtual machines, networks). Configuration management tools then configure the software and settings on these provisioned resources.
- Idempotency: Configuration management tools are designed to be idempotent, meaning they can be run multiple times without unintended side effects. This ensures that the desired state of the system is always maintained.
- Automated Software Installation and Updates: These tools automate the installation, configuration, and updating of software packages on target systems. This ensures consistency and reduces manual effort.
- Configuration Enforcement: They enforce desired configurations across the environment, ensuring that systems adhere to security policies and operational standards.
- Examples of Configuration Management Tools: Popular configuration management tools include Ansible, Chef, and Puppet. Ansible is often used in conjunction with Terraform for infrastructure provisioning and configuration management.
Planning and Design for IaC Implementation
Effective Infrastructure as Code (IaC) implementation hinges on meticulous planning and design. This phase lays the groundwork for a successful and maintainable IaC strategy, ensuring that the infrastructure aligns with business requirements, is easily managed, and is resilient to changes. A well-defined plan minimizes risks, accelerates deployment cycles, and optimizes resource utilization.
Defining Infrastructure Requirements
Before writing any IaC code, a thorough understanding of the infrastructure requirements is crucial. This involves analyzing the application’s needs, performance expectations, security considerations, and compliance mandates.To properly define infrastructure requirements, consider the following aspects:
- Application Architecture: Analyze the application’s architecture, including components such as web servers, databases, load balancers, and caching mechanisms. This understanding informs the infrastructure design. For example, a three-tier web application (web, application, database) will dictate the need for separate environments for each tier, potentially with different scaling and security requirements.
- Performance and Scalability: Define performance metrics such as expected traffic volume, response times, and the need for horizontal scaling. Identify the expected growth rate of the application and plan for scaling resources accordingly. Consider the use of auto-scaling groups or other dynamic scaling mechanisms. For instance, if a web application anticipates a 10x increase in traffic during peak hours, the infrastructure must be designed to automatically scale resources to handle the load.
- Security Requirements: Define security policies and best practices, including network segmentation, access control, encryption, and vulnerability management. Implement security groups, firewalls, and intrusion detection systems. Comply with relevant security standards and regulations. For example, a financial application might require strict access controls and encryption for sensitive data, adhering to regulations like PCI DSS.
- Compliance and Governance: Identify relevant compliance requirements, such as GDPR, HIPAA, or industry-specific regulations. Define governance policies, including change management processes, approval workflows, and auditing mechanisms. IaC should facilitate compliance through automated configuration and auditing. For example, healthcare applications must comply with HIPAA regulations, which dictate specific security measures for protected health information. IaC can automate the configuration of these measures.
- Cost Optimization: Analyze resource utilization and costs. Implement cost optimization strategies, such as right-sizing instances, using reserved instances, and utilizing spot instances where appropriate. IaC can help manage costs by enabling resource provisioning and deprovisioning based on demand. For example, using spot instances for non-critical workloads can significantly reduce infrastructure costs.
Designing a Basic IaC Workflow for Web Application Deployment
A well-defined IaC workflow streamlines the deployment process, ensuring consistency, repeatability, and automation. This section Artikels a basic workflow for deploying a simple web application.The following steps are part of the basic IaC workflow for web application deployment:
- Code Repository: Store the IaC code (e.g., Terraform configuration files, Ansible playbooks) in a version control system (e.g., Git). This allows for versioning, collaboration, and rollback capabilities.
- Infrastructure Definition: Define the infrastructure components using IaC tools. This includes virtual machines, networks, security groups, load balancers, and any other necessary resources. For instance, a Terraform configuration file would describe the resources required for the web application.
- Testing: Validate the IaC code through testing, including unit tests, integration tests, and end-to-end tests. This ensures the code functions as expected before deployment. For example, use tools like Terratest to verify the Terraform configuration.
- Deployment: Deploy the infrastructure using the IaC tool. This typically involves running commands like `terraform apply` or `ansible-playbook`.
- Configuration Management: Configure the deployed infrastructure using configuration management tools (e.g., Ansible, Chef, Puppet) or through scripts embedded in the IaC code. This step installs software, configures services, and deploys the web application code.
- Monitoring and Logging: Implement monitoring and logging to track the application’s performance and health. Integrate monitoring tools (e.g., Prometheus, Grafana) and logging services (e.g., ELK stack).
- Rollback and Updates: Design a rollback strategy in case of deployment failures. Implement automated update processes to apply changes to the infrastructure and application code.
An illustration of this workflow can be visualized as follows:
The workflow begins with code stored in a repository (Git). The IaC tool, such as Terraform, reads the configuration, which is then validated and tested. Upon successful testing, the tool provisions the infrastructure. Configuration management tools (Ansible, Chef) then configure the deployed infrastructure and deploy the web application. Monitoring and logging systems are integrated to track the application’s performance and health. Finally, the system includes rollback and update mechanisms.
Organizing Infrastructure Code into Reusable Modules or Components
Modularizing IaC code promotes reusability, maintainability, and consistency. This involves breaking down the infrastructure definition into smaller, self-contained modules or components.Key strategies for organizing infrastructure code into reusable modules include:
- Module Design: Design modules with a specific purpose, such as creating a virtual machine, setting up a database, or configuring a network. Each module should have clear inputs (variables), outputs, and a well-defined scope.
- Directory Structure: Organize the code in a logical directory structure. For example, a project might have directories for modules, environments (dev, staging, prod), and configurations.
- Variables and Inputs: Define variables to customize the modules. Use input variables to pass parameters to modules, making them flexible and reusable. For example, a module for creating a virtual machine might accept variables for instance type, operating system, and network configuration.
- Outputs: Define outputs to expose information from the modules. This allows other modules or configurations to access the resources created by the module. For example, a module for creating a database might output the database connection string.
- Versioning: Use version control and tagging to manage module versions. This ensures that changes to modules are tracked and that dependencies are managed effectively.
- Testing and Documentation: Write tests for the modules to ensure they function as expected. Document the modules clearly, including their inputs, outputs, and usage instructions.
For example, consider the creation of a database instance. A reusable module could encapsulate all the necessary configurations, including instance type, storage, security settings, and network configuration. This module can then be reused across multiple environments (development, staging, production) with different input variables, such as database size or security group rules.
Writing IaC Code for Target Environments
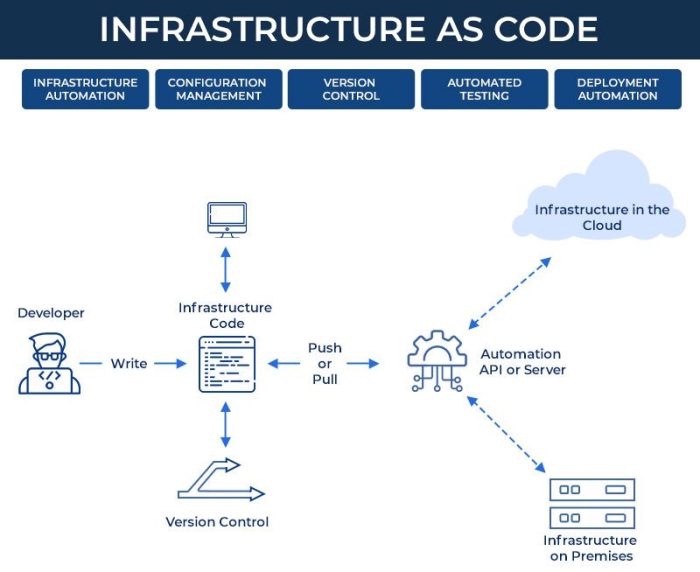
Implementing Infrastructure as Code (IaC) necessitates translating infrastructure requirements into a programmatic format. This involves utilizing specific tools and languages to define and manage infrastructure resources. The effectiveness of IaC hinges on the clarity, maintainability, and reusability of the code written. The subsequent sections detail the practical aspects of writing IaC code, encompassing syntax, resource creation, and best practices.
Demonstrating IaC Code Syntax and Structure
IaC tools employ distinct syntax and structures for defining infrastructure. The choice of tool dictates the language and organization of the code. For demonstration, we will use Terraform, a popular IaC tool, and its declarative HashiCorp Configuration Language (HCL). HCL is designed to be human-readable and supports modularity.The basic structure of a Terraform configuration file consists of blocks. Each block defines a specific resource, data source, or other configuration element.
A typical Terraform configuration file, `main.tf`, might look like this:“`terraformterraform required_providers aws = source = “hashicorp/aws” version = “~> 4.0” provider “aws” region = “us-east-1″resource “aws_instance” “example” ami = “ami-0c55b535168685792” # Example AMI ID instance_type = “t2.micro” tags = Name = “example-instance” “`This code defines a provider (AWS), specifies the region, and creates an AWS EC2 instance.
The `terraform` block specifies the provider requirements. The `provider` block configures the AWS provider, and the `resource` block defines the instance. The `ami` attribute specifies the Amazon Machine Image (AMI) ID, `instance_type` specifies the instance type, and `tags` adds metadata. This structure promotes a clear and organized approach to infrastructure definition.
Creating Infrastructure Resources Using IaC
Creating infrastructure resources with IaC involves defining the desired state of those resources within the configuration files. The process generally involves specifying resource types, attributes, and dependencies. The following steps are typically involved:* Define the Provider: This step involves specifying the cloud provider (e.g., AWS, Azure, GCP) and configuring authentication credentials and regions. This is typically done in a `provider` block within the configuration file.
For instance, in Terraform, the provider block defines the provider and its configuration.* Declare the Resources: Resources are declared using `resource` blocks. Each block specifies a resource type (e.g., `aws_instance` for an EC2 instance) and a name (e.g., `example`). Within the block, attributes are set to define the resource’s properties.* Configure Resource Attributes: Attributes within the resource block define the resource’s characteristics.
This includes parameters like the AMI ID, instance type, network settings, and storage configurations for a virtual machine. For example, the `ami` and `instance_type` attributes define the AMI and instance type of an AWS EC2 instance.* Manage Dependencies: IaC tools often automatically manage dependencies between resources. However, explicit dependencies can be defined using attributes like `depends_on` or through the order of resource declarations.
This ensures resources are created in the correct sequence.* Plan and Apply: Before applying the configuration, a plan is generated to show the changes that will be made. The `terraform plan` command analyzes the configuration and identifies the resources that need to be created, modified, or destroyed. The `terraform apply` command then executes the plan, creating or modifying the resources in the target environment.* Verify the Infrastructure: Once the `terraform apply` command completes, it is important to verify that the infrastructure is created correctly.
This can be done by checking the cloud provider’s console, using the IaC tool’s state file, or writing tests to validate the resources.For example, to create a virtual network (VPC) in AWS using Terraform:“`terraformresource “aws_vpc” “example” cidr_block = “10.0.0.0/16” tags = Name = “example-vpc” “`This code defines an AWS VPC with a CIDR block of `10.0.0.0/16` and tags the VPC with the name “example-vpc”.
Sharing Best Practices for Writing Maintainable and Readable IaC Code
Writing maintainable and readable IaC code is crucial for long-term success. Adhering to best practices enhances collaboration, reduces errors, and simplifies updates. Consider the following practices:* Use Modular Design: Break down large configurations into smaller, reusable modules. Modules encapsulate related resources and promote code reuse. For example, a module could define a network configuration, including VPCs, subnets, and security groups.* Implement Consistent Naming Conventions: Establish clear and consistent naming conventions for resources, variables, and modules.
This improves readability and makes it easier to understand the purpose of each component. Use a consistent naming scheme across all resources.* Document Your Code: Document your code thoroughly using comments and descriptions. Explain the purpose of each resource, variable, and module. This is critical for understanding the configuration and making changes in the future.* Use Variables and Outputs: Use variables to parameterize configurations, making them more flexible and reusable.
Define outputs to expose important information about the deployed infrastructure.* Apply Version Control: Store IaC code in a version control system (e.g., Git). This enables tracking changes, collaborating with others, and reverting to previous versions if needed.* Test Your Code: Implement testing to validate the configuration before deployment. Use tools like `terraform validate` to check for syntax errors and `terraform plan` to preview changes.
Consider using automated testing frameworks to verify the behavior of deployed resources.* Follow DRY Principle (Don’t Repeat Yourself): Avoid repeating code. Reuse existing modules and create new ones when needed to reduce redundancy.* Use a Linter and Formatter: Utilize linters and formatters to enforce code style and ensure consistency. Tools like `terraform fmt` automatically format Terraform code according to a standard style.By adopting these practices, organizations can significantly improve the quality and manageability of their IaC code, leading to more reliable and efficient infrastructure management.
Testing IaC Code
Testing Infrastructure as Code (IaC) is a critical practice for ensuring the reliability, consistency, and security of infrastructure deployments. Thorough testing helps identify and mitigate potential issues early in the development lifecycle, reducing the risk of costly errors and downtime in production environments. This section explores various testing strategies, designs a test suite for a simple IaC deployment, and details how to leverage testing frameworks to validate IaC code.
Testing Strategies for IaC Code
Effective IaC testing encompasses a range of strategies, each designed to validate different aspects of the infrastructure deployment. Employing a combination of these strategies provides comprehensive coverage and increases confidence in the IaC code’s correctness.
- Unit Tests: Unit tests focus on individual components or modules of the IaC code. They verify the functionality of specific resources, such as a single virtual machine configuration or a network security group rule. These tests typically involve mocking dependencies and asserting that the resource’s properties are correctly configured according to the code. For instance, a unit test might verify that a virtual machine’s CPU and memory settings are as defined in the IaC code.
- Integration Tests: Integration tests examine the interaction between multiple components or modules. They ensure that different parts of the infrastructure work together as expected. This involves deploying a subset of the infrastructure and verifying that the resources are interconnected and functioning correctly. An example of an integration test would be verifying that a web server can successfully communicate with a database server after deployment.
- End-to-End (E2E) Tests: E2E tests validate the entire infrastructure deployment, simulating real-world user scenarios. These tests deploy the complete infrastructure and verify that it meets the desired functionality and performance requirements. E2E tests often involve simulating user traffic, monitoring application performance, and validating that the system behaves as expected under load. An example would be testing the end-to-end functionality of a web application, from the user accessing the website to the database retrieving the requested information.
- Security Tests: Security tests assess the security posture of the deployed infrastructure. These tests can include vulnerability scanning, penetration testing, and compliance checks. Security tests help identify potential vulnerabilities and ensure that the infrastructure adheres to security best practices and organizational policies. For example, a security test might verify that network ports are closed or that security groups are configured according to least privilege principles.
- Policy Enforcement Tests: Policy enforcement tests ensure that the IaC code adheres to organizational policies and compliance requirements. These tests often involve using policy-as-code tools to define and enforce policies related to security, cost optimization, and governance. An example would be testing that all deployed resources are tagged correctly or that specific resource types are only deployed in approved regions.
- Drift Detection Tests: Drift detection tests compare the current state of the deployed infrastructure with the desired state defined in the IaC code. They identify any discrepancies or changes that have occurred outside of the IaC process, such as manual configuration changes. Drift detection helps maintain infrastructure consistency and prevent configuration drift.
Designing a Test Suite for a Simple IaC Deployment
Designing a comprehensive test suite involves defining test cases that cover different aspects of the infrastructure deployment. The test suite should include unit tests, integration tests, and potentially E2E tests, depending on the complexity of the infrastructure. This section details the creation of a test suite for a basic deployment.Consider a simple IaC deployment that provisions a single virtual machine (VM) in a cloud environment.
The VM is configured with a specific operating system, network settings, and storage. The following illustrates the components of a test suite:
- Unit Tests:
- Verify that the VM’s operating system is correctly specified in the IaC code.
- Validate the VM’s CPU and memory settings.
- Ensure that the network interface configuration is correct (e.g., IP address, subnet).
- Check that the storage volume size is as defined.
- Integration Tests:
- Verify that the VM can be accessed via SSH or another remote access protocol.
- Confirm that the VM can communicate with other resources within the same network (e.g., ping test).
- Test the functionality of any software installed on the VM.
- E2E Tests (Optional):
- If the VM is part of a larger application, test the end-to-end functionality of the application. For example, if the VM hosts a web server, test that the website is accessible and responds correctly.
- Security Tests:
- Verify that the VM’s firewall rules are configured correctly (e.g., only necessary ports are open).
- Scan the VM for known vulnerabilities.
- Policy Enforcement Tests:
- Verify that the VM is tagged with the correct metadata (e.g., environment, owner).
Using Testing Frameworks to Validate IaC Code
Testing frameworks automate the execution of tests and provide tools for managing and reporting test results. Using a testing framework simplifies the testing process and increases the reliability of the tests. The following section provides information on how to utilize testing frameworks to validate IaC code.Several testing frameworks are available for validating IaC code, each supporting different IaC tools and technologies.
Popular options include:
- Terratest: A Go library that provides testing capabilities for Terraform configurations. Terratest allows writing integration and E2E tests by deploying infrastructure and validating its properties. It supports various assertions and can interact with cloud providers.
- ChefSpec/InSpec: ChefSpec and InSpec are testing frameworks specifically designed for Chef cookbooks. ChefSpec is used for unit testing, and InSpec for compliance testing. They enable testing of resource configurations and policy enforcement.
- KitchenCI: A testing framework that supports multiple configuration management tools, including Chef, Puppet, and Ansible. KitchenCI facilitates testing infrastructure deployments across different platforms and environments.
- ServerSpec: A testing framework for infrastructure code, typically used with tools like Ansible, Chef, and Puppet. ServerSpec enables testing the state of servers and other resources.
- Test Kitchen: A testing framework for configuration management, such as Chef, Puppet, and Ansible. Test Kitchen helps in validating infrastructure deployments by running tests against different target environments.
The following illustrates an example of how to use Terratest to validate a Terraform configuration that provisions an AWS EC2 instance:“`gopackage testimport ( “testing” “github.com/gruntwork-io/terratest/modules/aws” “github.com/gruntwork-io/terratest/modules/terraform” “github.com/stretchr/testify/assert”)func TestTerraformEC2Instance(t
testing.T)
t.Parallel() terraformOptions := &terraform.Options TerraformDir: “../terraform”, // Path to the Terraform code defer terraform.Destroy(t, terraformOptions) terraform.InitAndApply(t, terraformOptions) // Get the instance ID from the Terraform output instanceID := terraform.Output(t, terraformOptions, “instance_id”) // Verify that the EC2 instance exists aws.GetInstance(t, instanceID, “us-east-1”) // Replace “us-east-1” with your region assert.NotEmpty(t, instanceID, “Instance ID should not be empty”) // Add additional assertions to validate the instance’s properties, such as: //
Instance type
//
Security group
// – Tags“`This example demonstrates how to:
- Define a `TestTerraformEC2Instance` function, which serves as the test case.
- Specify the path to the Terraform code using `TerraformDir`.
- Use `terraform.InitAndApply` to deploy the infrastructure.
- Use `terraform.Output` to retrieve outputs from the Terraform configuration, such as the instance ID.
- Utilize `aws.GetInstance` to verify that the EC2 instance exists.
- Add assertions to validate the instance’s properties.
This approach allows you to automate testing and verify that the IaC code functions as intended, reducing the risk of errors and ensuring the infrastructure meets the required specifications.
Deploying IaC to Target Environments
Deploying Infrastructure as Code (IaC) to target environments represents the culmination of the IaC lifecycle. This stage involves translating the code, which defines the desired infrastructure state, into actual resources within the target environment. This process must be executed systematically and safely to minimize disruption and ensure the infrastructure aligns with the defined specifications. Effective deployment strategies incorporate automation, version control, and robust failure handling mechanisms to provide a reliable and repeatable infrastructure provisioning process.
Step-by-Step Procedure for Deploying IaC Code
The deployment of IaC code typically follows a structured, automated process to ensure consistency and reduce the risk of human error. This process is often orchestrated by a CI/CD pipeline, integrating version control, testing, and deployment steps.
- Environment Preparation: Before deployment, the target environment may need preparation. This could involve setting up network configurations, security groups, and access controls. It is crucial to ensure the environment is in a known, stable state before applying IaC changes.
- Code Acquisition: The IaC code, stored in a version control system (e.g., Git), is retrieved. The specific branch or commit representing the desired infrastructure state is selected.
- Dependency Resolution: If the IaC code relies on external modules, libraries, or other dependencies, these are resolved and installed. This may involve fetching modules from a package repository or specifying dependencies within the IaC code itself.
- Plan Generation (Dry Run): Most IaC tools offer a “plan” or “dry run” feature. This step analyzes the IaC code and compares it with the current state of the target environment. It identifies the changes that will be made during the deployment. The plan allows for reviewing and validating the proposed changes before they are applied.
- Execution (Apply): Based on the generated plan, the IaC tool executes the changes in the target environment. This involves creating, modifying, or deleting resources to match the desired state defined in the IaC code. The execution process should be automated and idempotent, meaning that repeated executions with the same code should produce the same result.
- Verification: After the deployment, verification steps are performed to confirm that the infrastructure has been deployed correctly. This can include automated tests, monitoring of resources, and validation of configurations. If verification fails, the deployment is considered unsuccessful, and rollback procedures are initiated.
- Post-Deployment Activities: Once the infrastructure is successfully deployed and verified, post-deployment activities may be necessary. These can include configuring applications, integrating with monitoring systems, and generating documentation.
Role of Version Control in IaC Deployments
Version control is fundamental to effective IaC deployments. It enables tracking changes, collaboration, and the ability to revert to previous states. Using version control promotes reproducibility, auditability, and the overall reliability of the infrastructure management process.
- Tracking Changes: Version control systems (e.g., Git) meticulously track all changes made to the IaC code. Each modification is associated with a commit, including a descriptive message explaining the change. This detailed history enables teams to understand the evolution of the infrastructure over time.
- Collaboration: Version control systems facilitate collaborative development. Multiple team members can work on the IaC code concurrently, using features like branching and merging to integrate their changes. This allows for parallel development and streamlined code reviews.
- Rollback Capabilities: If a deployment introduces errors or unexpected behavior, version control allows for a rapid rollback to a previous, known-good state. This minimizes downtime and mitigates the impact of deployment failures.
- Auditing and Compliance: Version control provides a comprehensive audit trail of all infrastructure changes. This is essential for compliance with regulations and internal security policies. The audit trail includes who made the changes, when they were made, and the specific changes that were implemented.
- Reproducibility: Version control ensures the reproducibility of the infrastructure. By checking out a specific commit, it is possible to recreate the exact infrastructure state at that point in time. This is critical for testing, disaster recovery, and environment consistency.
Strategies for Handling Deployment Failures and Rollbacks
Deployment failures are inevitable, and effective strategies are essential for mitigating their impact. Rollback mechanisms are critical for returning the infrastructure to a stable state when deployment issues arise.
- Automated Rollbacks: IaC tools often provide built-in rollback capabilities. These allow the tool to automatically revert to a previous state if the deployment fails. This is often achieved by saving a snapshot of the infrastructure before the deployment or by automatically reverting to the previous version of the IaC code.
- Idempotency: IaC code should be designed to be idempotent. This means that applying the same code multiple times should result in the same outcome. Idempotency ensures that even if a deployment fails mid-process, subsequent attempts will resume from the point of failure without causing unintended side effects.
- Monitoring and Alerting: Implement robust monitoring and alerting systems to detect deployment failures quickly. These systems should track key metrics and trigger alerts when issues arise, enabling rapid response and intervention.
- Testing and Validation: Thorough testing, including unit tests, integration tests, and end-to-end tests, is crucial before deployment. This helps to identify potential issues early in the development cycle, reducing the likelihood of deployment failures.
- Deployment Strategies: Employ deployment strategies like blue/green deployments or canary deployments to minimize the impact of failures. These strategies involve deploying the new infrastructure alongside the existing infrastructure and gradually shifting traffic to the new version.
- Disaster Recovery Plans: Develop comprehensive disaster recovery plans that include procedures for restoring the infrastructure in the event of a catastrophic failure. These plans should address various failure scenarios and Artikel the steps required to recover the infrastructure.
Managing and Maintaining IaC Infrastructure
The ongoing management and maintenance of Infrastructure as Code (IaC) deployments are critical for ensuring the stability, security, and efficiency of target environments. This involves adapting IaC code to reflect changes, addressing infrastructure drift, and implementing robust monitoring and logging strategies. Effective management minimizes downtime, streamlines updates, and allows for proactive issue resolution.
Updating and Modifying IaC Code
Adapting IaC code is a continuous process necessitated by evolving requirements, changes in application architecture, and security updates. The process should be systematic to avoid introducing errors and ensure consistency.
- Version Control: Utilizing a version control system, such as Git, is fundamental. Every change to IaC code should be tracked, allowing for rollbacks, collaboration, and auditing. Each modification is a new commit with a descriptive message detailing the nature of the change.
- Change Management Process: Implementing a change management workflow ensures that all modifications are reviewed, tested, and approved before deployment. This workflow typically involves creating a feature branch, making the changes, creating a pull request, undergoing code review, and then merging the changes into the main branch after approval.
- Testing: Thorough testing is paramount. This includes unit tests for individual components, integration tests to verify interactions between components, and end-to-end tests to simulate real-world scenarios. Tests should be automated to ensure repeatable validation.
- Incremental Changes: Making small, incremental changes is preferable to large, sweeping modifications. This approach simplifies debugging and reduces the risk of introducing significant issues. Each change should be tested and validated before proceeding to the next.
- Idempotency: IaC code should be designed to be idempotent. This means that applying the same configuration multiple times should produce the same result, preventing unintended side effects.
- Documentation: Keeping the IaC code well-documented is crucial for understanding the infrastructure configuration. This includes commenting within the code, maintaining a separate documentation repository, and updating documentation with every change.
Handling Infrastructure Drift
Infrastructure drift refers to discrepancies between the intended state defined in IaC code and the actual state of the infrastructure. Drift can occur due to manual changes, configuration errors, or software updates. Addressing drift is crucial for maintaining consistency and predictability.
- Detection Mechanisms: Implementing tools to detect infrastructure drift is essential. These tools compare the actual state of the infrastructure with the state defined in the IaC code. Common tools include configuration management tools (e.g., Ansible, Chef, Puppet) with drift detection capabilities, as well as specialized drift detection tools.
- Automated Remediation: Ideally, drift should be automatically remediated. This involves using the IaC tool to bring the infrastructure back into the desired state. For example, if a manual change has altered a configuration file, the IaC tool can automatically overwrite it with the correct configuration.
- Manual Remediation: In cases where automated remediation is not possible or practical, manual intervention may be required. This involves identifying the cause of the drift, correcting the IaC code, and redeploying the infrastructure.
- Regular Audits: Performing regular audits of the infrastructure helps identify and address drift proactively. Audits involve comparing the actual state of the infrastructure with the IaC code and investigating any discrepancies.
- Policy Enforcement: Implementing policies to restrict manual changes to the infrastructure can help prevent drift. This can involve using role-based access control (RBAC) and other security measures to limit who can make changes.
Monitoring and Logging IaC Deployments
Monitoring and logging are vital for gaining visibility into IaC deployments, identifying issues, and ensuring the overall health and performance of the infrastructure. These practices provide valuable insights into the deployment process, resource utilization, and application behavior.
- Monitoring Tools: Utilizing monitoring tools to track the performance and health of the infrastructure. These tools collect metrics such as CPU usage, memory consumption, network traffic, and error rates. Popular monitoring tools include Prometheus, Grafana, and Datadog.
- Logging Infrastructure: Implementing comprehensive logging for all IaC deployments. Logs should capture information about deployments, configuration changes, and any errors that occur. Log aggregation tools like the ELK stack (Elasticsearch, Logstash, Kibana) or Splunk are frequently used to centralize and analyze logs.
- Alerting: Configuring alerts to notify administrators of critical events, such as deployment failures, performance degradation, or security breaches. Alerts can be sent via email, SMS, or other notification channels.
- Deployment Tracking: Tracking the status of IaC deployments, including success, failure, and the duration of the deployment. This can be achieved using deployment pipelines and reporting tools.
- Performance Analysis: Analyzing performance metrics and logs to identify bottlenecks and optimize the infrastructure. This involves identifying slow-running processes, inefficient resource utilization, and other performance issues.
- Security Monitoring: Monitoring security-related events, such as unauthorized access attempts, configuration changes, and suspicious activity. This is crucial for detecting and responding to security threats.
Security Considerations in IaC
Infrastructure as Code (IaC) introduces significant advantages in terms of automation, version control, and reproducibility. However, this shift also presents new security challenges. IaC code, being declarative and executable, becomes a critical component of the attack surface. Therefore, securing IaC requires a proactive and comprehensive approach, integrating security considerations throughout the entire IaC lifecycle, from code creation to deployment and maintenance.
Failing to address these concerns can lead to vulnerabilities that compromise the confidentiality, integrity, and availability of the infrastructure and the applications it supports.
Security Best Practices for Writing and Deploying IaC Code
Implementing security best practices is crucial for minimizing risks. These practices should be integrated into the development and deployment pipelines.
- Principle of Least Privilege: Grant only the necessary permissions to the IaC code and associated service accounts. Avoid assigning excessive privileges, which could allow attackers to escalate their access. This principle should extend to all aspects of the infrastructure provisioned by IaC, ensuring that resources only have the minimum required permissions to function. For example, using roles and policies in cloud environments to define the specific actions a service account can perform.
- Secrets Management: Never hardcode sensitive information, such as passwords, API keys, and database credentials, directly into the IaC code. Instead, utilize secure secrets management solutions, such as HashiCorp Vault, AWS Secrets Manager, or Azure Key Vault. These tools allow for the secure storage, retrieval, and rotation of secrets. Consider the use of environment variables and configuration management tools for runtime configuration.
- Input Validation and Sanitization: When IaC code accepts user inputs or external data, validate and sanitize them to prevent injection attacks, such as SQL injection, command injection, and cross-site scripting (XSS). This involves verifying the data type, length, and format of the inputs, and sanitizing them to remove any malicious code. This practice is particularly important when using IaC to configure network security groups or firewall rules.
- Regular Code Reviews: Conduct regular code reviews, both automated and manual, to identify potential security vulnerabilities, such as insecure coding practices, misconfigurations, and logic errors. Utilize static code analysis tools to automatically scan the code for common vulnerabilities. Manual code reviews should be performed by experienced security professionals.
- Infrastructure Hardening: Use IaC to configure and enforce security hardening measures on the provisioned infrastructure. This includes disabling unnecessary services, applying security patches, configuring firewalls, and implementing intrusion detection and prevention systems (IDPS). This practice ensures that the infrastructure is configured securely from the outset.
- Automated Security Scanning: Integrate security scanning tools into the IaC pipeline to automatically scan the code and the deployed infrastructure for vulnerabilities. This can include static code analysis, dynamic analysis, and compliance checks. Tools such as Trivy, Checkov, and Snyk can be used to identify vulnerabilities in IaC code and deployed infrastructure.
- Immutable Infrastructure: Design IaC deployments to be immutable. This means that once an infrastructure component is deployed, it should not be modified in place. Instead, any changes should be implemented by creating a new version of the component and redeploying it. This approach simplifies security patching and reduces the risk of configuration drift.
- Regular Security Audits: Perform regular security audits of the IaC code and the deployed infrastructure to identify any security vulnerabilities or misconfigurations. These audits should be performed by independent security professionals and should include penetration testing.
Common Security Vulnerabilities in IaC Deployments
IaC deployments are susceptible to various security vulnerabilities. Understanding these vulnerabilities is crucial for proactive mitigation.
- Hardcoded Secrets: The inclusion of sensitive information, such as passwords, API keys, and database credentials, directly in the IaC code, presents a significant risk. If the code is compromised, attackers can easily access these secrets. This can lead to unauthorized access to sensitive data and systems.
- Insecure Configuration: Incorrectly configured infrastructure components, such as open ports, weak encryption settings, and default credentials, can create vulnerabilities. This includes misconfigured network security groups, firewall rules, and access control lists (ACLs).
- Lack of Input Validation: Failing to validate and sanitize user inputs or external data can lead to injection attacks. This allows attackers to inject malicious code into the infrastructure.
- Insufficient Access Controls: Granting excessive privileges to service accounts or users can lead to unauthorized access and privilege escalation. This includes using broad permissions and failing to adhere to the principle of least privilege.
- Configuration Drift: Changes made to the infrastructure outside of the IaC code can introduce inconsistencies and vulnerabilities. This includes manual configuration changes and patching that is not automated.
- Supply Chain Attacks: Vulnerabilities in third-party modules or dependencies used in IaC code can expose the infrastructure to attacks. This includes using outdated or compromised modules.
- Misconfigured Storage: Improperly configured storage buckets, such as S3 buckets or Azure Blob storage, can expose sensitive data to the public. This includes failing to encrypt data at rest and using insecure access control lists (ACLs).
- Outdated Software and Patches: Deploying infrastructure with outdated software or failing to apply security patches can create vulnerabilities. This includes not automating the patching process and not using the latest versions of software.
Security Checklist for IaC Projects
A security checklist provides a structured approach to ensure that security considerations are addressed throughout the IaC lifecycle.
- Planning and Design:
- Define security requirements and compliance standards.
- Identify and document all sensitive data and systems.
- Select secure IaC tools and technologies.
- Implement a secrets management strategy.
- Writing IaC Code:
- Avoid hardcoding secrets. Use a secrets management solution.
- Implement the principle of least privilege.
- Validate and sanitize all user inputs.
- Use secure coding practices.
- Follow a secure coding style guide.
- Use code linters and static analysis tools.
- Testing IaC Code:
- Perform regular code reviews.
- Conduct automated security scans.
- Test for common vulnerabilities (e.g., misconfigurations, insecure settings).
- Test the IaC code in a staging environment before deploying to production.
- Deploying IaC to Target Environments:
- Automate security configuration.
- Enforce infrastructure hardening measures.
- Monitor infrastructure for security events.
- Implement automated patching and updates.
- Use immutable infrastructure where possible.
- Managing and Maintaining IaC Infrastructure:
- Regularly audit IaC code and deployed infrastructure.
- Monitor for configuration drift.
- Implement a vulnerability management program.
- Update IaC code and infrastructure regularly.
- Perform penetration testing.
IaC for Different Target Environments (e.g., Cloud, On-Premise)
The implementation of Infrastructure as Code (IaC) varies significantly depending on the target environment. Cloud environments, with their APIs and readily available services, offer distinct advantages compared to on-premise infrastructure. Hybrid cloud environments introduce additional complexities, necessitating careful planning and tool selection. Understanding these differences is crucial for successful IaC adoption.
IaC Implementations for Cloud Environments (AWS, Azure, GCP)
Cloud providers like Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP) offer various IaC tools and services, each with its strengths and weaknesses. Choosing the appropriate tool depends on factors such as team expertise, the complexity of the infrastructure, and desired level of control.
- AWS: AWS provides several IaC options, including AWS CloudFormation, Terraform, and the AWS Cloud Development Kit (CDK). CloudFormation is AWS’s native IaC service, enabling the definition and management of infrastructure using JSON or YAML templates. It integrates tightly with AWS services, offering robust features like drift detection and stack rollback. Terraform, a third-party tool, supports multiple cloud providers and on-premise infrastructure, enabling infrastructure as code portability.
The AWS CDK allows developers to define infrastructure using familiar programming languages like TypeScript, Python, and Java. For example, a CloudFormation template might define an EC2 instance, a security group, and an Elastic Load Balancer, specifying their configurations and dependencies.
- Azure: Azure offers Azure Resource Manager (ARM) templates, Bicep, and Terraform. ARM templates use JSON or Bicep, a domain-specific language that simplifies template creation, to define and deploy Azure resources. Azure also supports Terraform, providing flexibility for multi-cloud deployments. ARM templates are well-integrated with Azure services, enabling features like role-based access control (RBAC) and deployment history tracking. For instance, an ARM template could define a virtual network, virtual machines, and storage accounts, specifying their configurations and dependencies.
Bicep offers a more concise and user-friendly syntax compared to JSON, making template authoring easier.
- GCP: GCP utilizes Google Cloud Deployment Manager, Terraform, and Cloud Foundation Toolkit. Deployment Manager uses YAML or Python to define infrastructure. Terraform also provides multi-cloud support, offering a consistent approach across different cloud providers. The Cloud Foundation Toolkit provides a set of pre-built modules and best practices to streamline infrastructure deployments. For example, a Deployment Manager configuration could define a Compute Engine instance, a Cloud Storage bucket, and a Cloud SQL database, specifying their configurations and dependencies.
Terraform can be used to manage these resources, providing a unified approach alongside resources from other cloud providers or on-premise infrastructure.
Specific Challenges of Using IaC in On-Premise Environments
Implementing IaC in on-premise environments presents unique challenges compared to cloud deployments. These challenges often stem from the lack of standardization, the need for manual configuration, and the complexity of managing physical hardware.
- Lack of Standardization: On-premise environments often lack the standardized APIs and services found in the cloud. This necessitates the use of more specialized tools and configurations. Different vendors and hardware configurations can lead to inconsistencies, making it challenging to create reusable IaC modules.
- Manual Configuration: Many on-premise infrastructure components require manual configuration, such as physical servers, network devices, and storage arrays. This manual intervention can introduce errors and delays, making it difficult to automate infrastructure provisioning.
- Complexity of Managing Physical Hardware: Managing physical hardware requires dealing with physical access, power, cooling, and other environmental considerations. IaC tools need to integrate with hardware management systems, which can be complex and vendor-specific.
- Limited Automation Capabilities: On-premise environments often have limited automation capabilities compared to cloud environments. Automation tools might not support all the features needed to manage the infrastructure, requiring manual workarounds or custom scripts.
- Security Concerns: Security is a critical concern in on-premise environments, where infrastructure is often more exposed to physical threats. IaC solutions must incorporate robust security measures to protect against unauthorized access and data breaches.
Designing an IaC Solution for a Hybrid Cloud Environment
Hybrid cloud environments combine on-premise infrastructure with cloud resources, introducing new complexities for IaC. A well-designed IaC solution for a hybrid cloud must address these challenges while ensuring consistency, portability, and security.
- Tool Selection: Choose IaC tools that support both cloud and on-premise environments, such as Terraform or Ansible. These tools enable infrastructure definition across different platforms using a unified approach. Consider the team’s expertise and the level of control required when selecting the tool.
- Infrastructure Abstraction: Create abstractions to hide the differences between cloud and on-premise infrastructure. This can be achieved by using modules or templates that abstract away the underlying implementation details. For instance, a module for creating a database could abstract away the differences between an on-premise database server and a cloud-based database service.
- Centralized Configuration Management: Implement a centralized configuration management system to manage configuration files and secrets across all environments. Tools like HashiCorp Vault or AWS Secrets Manager can securely store and manage sensitive information. This helps maintain consistency and security across all infrastructure components.
- Network Connectivity: Establish secure network connectivity between the on-premise environment and the cloud. This can involve setting up VPN connections, Direct Connect, or other network configurations. IaC should automate the configuration of these network components to ensure secure communication between the environments.
- Orchestration and Automation: Use orchestration tools to automate the deployment and management of resources across both environments. Tools like Kubernetes or HashiCorp Nomad can orchestrate containerized applications. IaC should integrate with these orchestration tools to automate the deployment and scaling of applications.
- Monitoring and Logging: Implement a unified monitoring and logging solution to collect data from both cloud and on-premise environments. This enables centralized monitoring and troubleshooting. IaC should automate the deployment and configuration of monitoring and logging agents.
- Security Best Practices: Implement security best practices throughout the IaC lifecycle, including using secure templates, encrypting sensitive data, and implementing access controls. Regularly audit the IaC code and infrastructure to identify and address security vulnerabilities.
Advanced IaC Techniques
Implementing Infrastructure as Code (IaC) transcends basic deployments, enabling sophisticated management of complex infrastructure environments. Advanced IaC techniques empower organizations to automate intricate workflows, enhance resilience, and optimize resource utilization across diverse platforms. This section explores these advanced practices, including CI/CD integration and disaster recovery planning, providing a comprehensive understanding of how to leverage IaC for maximum efficiency and scalability.
IaC for Complex Deployments
Managing complex deployments necessitates a structured and automated approach to ensure consistency, repeatability, and reduced manual intervention. This involves leveraging IaC to define intricate infrastructure architectures, including multi-tiered applications, distributed systems, and hybrid cloud environments.Complex deployments often involve:
- Modularization and Reusability: Breaking down infrastructure into reusable modules and components. This promotes code reusability, reduces redundancy, and simplifies maintenance. For example, a module could define a specific database configuration, a web server setup, or a networking component.
- Templating and Parameterization: Utilizing templates and parameters to create flexible and adaptable infrastructure definitions. Parameters allow for customization based on environment, region, or specific application requirements.
- Orchestration and Automation: Employing orchestration tools and automation workflows to manage the deployment and configuration of multiple resources across different environments. This includes tools like Terraform, Ansible, and CloudFormation, which facilitate the coordinated provisioning and management of resources.
- Versioning and Collaboration: Implementing version control systems (e.g., Git) to track changes to IaC code, enabling collaboration among team members, and facilitating rollback capabilities.
- State Management: Employing state management mechanisms to track the current state of the infrastructure and ensure that changes are applied consistently. This prevents configuration drift and ensures that the infrastructure reflects the desired state.
A practical example involves deploying a multi-tier web application with a load balancer, web servers, and a database. IaC code would define each component as a separate module, parameterized for different environments (development, staging, production). The orchestration tool would then deploy and configure these modules in a coordinated manner, ensuring that the application is deployed consistently across all environments.
IaC for Continuous Integration and Continuous Delivery (CI/CD)
Integrating IaC with CI/CD pipelines streamlines the deployment process, enabling automated testing, validation, and deployment of infrastructure changes. This approach promotes faster release cycles, reduced errors, and improved agility.The integration of IaC with CI/CD involves the following steps:
- Version Control Integration: IaC code is stored in a version control system (e.g., Git). Any changes to the infrastructure code trigger the CI/CD pipeline.
- Automated Testing: Before deployment, the IaC code undergoes automated testing. This includes:
- Syntax Validation: Checking the code for syntax errors and ensuring it adheres to the IaC tool’s syntax rules.
- Static Analysis: Analyzing the code for potential security vulnerabilities, best practice violations, and code quality issues.
- Policy Enforcement: Verifying that the IaC code complies with defined infrastructure policies and governance rules.
- Infrastructure Validation: Validating the infrastructure configuration before deployment. This involves simulating the deployment process to identify potential issues.
- Automated Deployment: If all tests pass, the CI/CD pipeline automatically deploys the infrastructure changes to the target environment.
- Rollback Mechanisms: Implementing rollback mechanisms to revert to a previous, known-good state in case of deployment failures or issues.
Consider a scenario where a change is made to the web server configuration defined in IaC. The change is committed to the Git repository, triggering the CI/CD pipeline. The pipeline then performs syntax validation, static analysis, and policy enforcement. If all tests pass, the pipeline deploys the updated web server configuration to the staging environment. After successful testing in staging, the pipeline automatically deploys the configuration to the production environment.
IaC-Based Disaster Recovery Plan
An IaC-based disaster recovery (DR) plan ensures business continuity by automating the provisioning and configuration of infrastructure in a secondary location or environment in the event of a disaster. This approach reduces recovery time and minimizes downtime.An IaC-based DR plan typically includes the following components:
- Infrastructure Replication: Replicating critical infrastructure components (e.g., databases, application servers) to a secondary site or environment. IaC automates the provisioning and configuration of these replicated resources.
- Data Replication: Implementing data replication strategies to ensure data consistency between the primary and secondary sites.
- Automated Failover: Automating the failover process to the secondary site in the event of a disaster. IaC can be used to update DNS records, configure load balancers, and bring up the secondary infrastructure.
- Testing and Validation: Regularly testing the DR plan to ensure that it functions as expected. IaC facilitates the automated testing of the failover and recovery procedures.
- Cost Optimization: Employing cost optimization strategies to minimize the cost of the DR infrastructure. This might involve using cheaper resources or optimizing the replication frequency.
An example scenario: a company uses IaC to provision and configure its primary production environment in a primary cloud region. The DR plan uses IaC to define a secondary environment in a different cloud region. In the event of a disaster in the primary region, the automated failover process, orchestrated by IaC, provisions and configures the infrastructure in the secondary region, and redirects traffic to the secondary environment.
The IaC ensures the secondary environment is a replica of the primary one, with the same configurations and application settings, guaranteeing a quick and reliable recovery.
Outcome Summary
In conclusion, the adoption of IaC represents a pivotal evolution in infrastructure management, offering significant advantages in terms of automation, consistency, and scalability. This guide has navigated the essential facets of IaC, from its foundational concepts and tool selection to the nuances of code writing, testing, deployment, and ongoing management. By embracing the principles and practices Artikeld, organizations can unlock the full potential of infrastructure automation, streamlining operations, mitigating risks, and accelerating the delivery of applications and services.
The journey toward infrastructure-as-code is a continuous process of learning, adapting, and refining, ensuring a future-proof and efficient IT infrastructure.
Questions Often Asked
What are the primary advantages of using IaC?
IaC offers several key benefits: increased consistency, reduced manual errors, faster deployments, improved scalability, enhanced version control, and better auditability. It also fosters collaboration and enables automation, leading to more efficient and reliable infrastructure management.
How does IaC integrate with CI/CD pipelines?
IaC seamlessly integrates with CI/CD pipelines. IaC code is version-controlled, tested, and deployed automatically as part of the CI/CD process. This automation ensures that infrastructure changes are tested and validated before they are deployed to production environments, improving reliability and reducing the risk of errors.
What are the key considerations when choosing an IaC tool?
When selecting an IaC tool, consider factors such as the target environment (cloud, on-premise, or hybrid), the complexity of your infrastructure, team expertise, community support, and the tool’s features (e.g., state management, modularity, and declarative vs. imperative approaches). The specific needs of the project will heavily influence the best choice.
How can I handle infrastructure drift with IaC?
Infrastructure drift occurs when the actual state of your infrastructure deviates from the state defined in your IaC code. To address this, use tools that support state management (e.g., Terraform, Ansible) and regularly reconcile your infrastructure with the IaC code. Implement automated checks and monitoring to detect and correct any discrepancies.