In today’s cloud-centric world, safeguarding applications against SQL injection is paramount. This critical vulnerability allows malicious actors to manipulate database queries, potentially leading to data breaches, unauthorized access, and significant reputational damage. Understanding the intricacies of SQL injection, along with the robust defense mechanisms available, is essential for any organization operating in the cloud.
This guide delves into the core principles and practical strategies for preventing SQL injection in cloud applications. We will explore various aspects, from understanding the attack vectors and implementing secure coding practices to leveraging advanced security tools and adopting proactive monitoring techniques. This will provide you with a strong foundation for building and maintaining secure cloud applications.
Understanding SQL Injection in Cloud Context
SQL injection attacks pose a significant threat to cloud applications, potentially leading to data breaches, system compromise, and reputational damage. Understanding the nuances of these attacks within a cloud environment is crucial for implementing effective preventative measures. Cloud applications, with their reliance on databases and web interfaces, are particularly susceptible to these vulnerabilities.
Fundamental Concept of SQL Injection Attacks
SQL injection is a web security vulnerability that allows attackers to interfere with the queries that an application makes to its database. It occurs when user-supplied data is incorporated directly into an SQL query without proper sanitization or validation. This allows an attacker to manipulate the query, potentially gaining unauthorized access to sensitive data, modifying database contents, or even executing arbitrary commands on the database server.
Exploiting Cloud-Based Database Systems
Cloud-based database systems, such as those offered by AWS (Amazon Web Services), Azure (Microsoft Azure), and Google Cloud Platform (GCP), are often targeted by SQL injection attacks. Attackers exploit vulnerabilities in the application code that interacts with these databases. The cloud’s distributed nature and reliance on APIs can broaden the attack surface, making it easier for attackers to identify and exploit weaknesses.
Successful SQL injection can lead to the exposure of sensitive information, such as customer data, financial records, and intellectual property, all stored within the cloud environment.
Common Attack Vectors for Cloud Applications
Attackers employ various techniques to compromise cloud applications through SQL injection. Understanding these vectors is vital for implementing effective defenses.
- Web Forms: Web forms are a common entry point. Attackers inject malicious SQL code into form fields, such as username, password, or search queries. If the application doesn’t properly validate the input, the injected code is executed by the database.
- URL Parameters: URL parameters are also vulnerable. If an application uses parameters in a URL to construct SQL queries, attackers can modify these parameters to inject malicious code. For example, a URL like `https://example.com/products?id=123` could be exploited if the `id` parameter is not properly sanitized. An attacker might change the URL to `https://example.com/products?id=123; DROP TABLE users;–` to attempt to drop the `users` table.
- HTTP Headers: HTTP headers, such as the `User-Agent` or `Referer` headers, can also be exploited. If the application uses header values in SQL queries (e.g., for logging or tracking purposes), attackers can inject malicious SQL code into these headers.
- Cookies: Cookies can be manipulated by attackers. If the application uses cookie values in SQL queries, attackers can inject malicious SQL code into the cookie data.
- Error Messages: Attackers often use error messages to gather information about the database structure and the application’s code. By crafting malicious SQL injection attempts, they can trigger error messages that reveal the database type, table names, column names, and other valuable information. This information helps attackers refine their attacks and exploit specific vulnerabilities.
Example: An attacker might try to log in with the username ‘admin’ and the password ‘ ‘ OR ‘1’=’1′. This is a classic SQL injection attempt. If the application’s login query is constructed without proper sanitization, the query might look like this:
`SELECTFROM users WHERE username = ‘admin’ AND password = ” OR ‘1’=’1′;`
Because ‘1’=’1′ is always true, the query will return all rows from the ‘users’ table, effectively bypassing the password check.
Input Validation and Sanitization
Input validation and sanitization are fundamental to securing cloud applications against SQL injection attacks. These techniques work in tandem to ensure that data entering the application is safe and does not contain malicious code. Properly implemented, they significantly reduce the attack surface and protect sensitive data.
Importance of Input Validation as a Primary Defense Mechanism
Input validation acts as the first line of defense against SQL injection, preventing malicious code from ever reaching the database. It involves checking the data received from users or other sources to ensure it meets predefined criteria. This process helps to filter out potentially harmful inputs before they can be processed by the application.
- Prevents Malicious Code Execution: Input validation is crucial because it ensures that only expected data types and formats are accepted. By rejecting or modifying unexpected input, it prevents attackers from injecting SQL code.
- Protects Database Integrity: By preventing malicious SQL queries from reaching the database, input validation helps maintain the integrity and confidentiality of the data stored within.
- Simplifies Sanitization: Input validation often makes sanitization more manageable. Once the data has been validated, it can be sanitized more effectively because the range of possible inputs has been narrowed.
- Reduces Attack Surface: By implementing input validation at the entry points of an application, the attack surface is significantly reduced. This limits the points where an attacker can inject malicious code.
- Improves Application Reliability: Properly validated input leads to more predictable application behavior and reduces the likelihood of unexpected errors caused by malformed or malicious data.
Implementing Input Validation on the Server-Side Using Programming Examples
Server-side input validation is critical because it’s the final check before data interacts with the database. Client-side validation can be bypassed, making server-side validation essential. Here are examples in Python and PHP demonstrating how to validate user inputs.
Python Example:
This Python code snippet demonstrates server-side input validation using the Flask framework. It validates that the user ID is an integer before querying the database. This example assumes the use of a secure database connection and parameterized queries, which are also essential for preventing SQL injection.
from flask import Flask, request, jsonifyimport sqlite3app = Flask(__name__)def validate_user_id(user_id): """Validates that the user ID is an integer.""" try: user_id = int(user_id) return user_id except ValueError: return [email protected]('/get_user', methods=['GET'])def get_user(): user_id = request.args.get('user_id') validated_user_id = validate_user_id(user_id) if validated_user_id is None: return jsonify('error': 'Invalid user ID'), 400 conn = sqlite3.connect('mydatabase.db') # Replace with your database details cursor = conn.cursor() cursor.execute("SELECT- FROM users WHERE id = ?", (validated_user_id,)) user = cursor.fetchone() conn.close() if user: return jsonify('user': user) else: return jsonify('error': 'User not found'), 404if __name__ == '__main__': app.run(debug=True)
PHP Example:
This PHP code demonstrates input validation using the `filter_var` function, which is a standard way to validate input in PHP. This example validates that the email address is in a valid format. This also assumes the use of prepared statements, which is a crucial step to prevent SQL injection in PHP.
setAttribute(PDO::ATTR_ERRMODE, PDO::ERRMODE_EXCEPTION); $stmt = $conn->prepare("SELECT- FROM users WHERE email = ?"); $stmt->execute([$email]); $result = $stmt->fetchAll(); if (count($result) > 0) // User found else // User not found catch(PDOException $e) echo "Error: " .$e->getMessage(); $conn = null;?>
Comparing Different Sanitization Techniques for Various Data Types to Prevent SQL Injection
Sanitization is the process of removing or modifying potentially harmful characters or patterns from user inputs. It’s essential to employ different sanitization techniques based on the data type to effectively prevent SQL injection.
Here’s a table summarizing common sanitization techniques for different data types:
| Data Type | Sanitization Techniques | Description | Example (PHP) |
|---|---|---|---|
| Integers | Type casting, Regular expressions | Ensure the input is a number and remove non-numeric characters. | $id = (int) $userInput; |
| Strings | Escaping, Character encoding, Removing or replacing special characters. | Escape special characters or encode to prevent misinterpretation by the database. | $escapedString = mysqli_real_escape_string($connection, $userInput); |
| Dates | Format validation, Regular expressions | Verify the date format and ensure it matches the expected pattern. | $date = DateTime::createFromFormat('Y-m-d', $userInput); |
| Booleans | Type casting, String comparison | Convert the input to a boolean or compare against expected string values (e.g., “true”, “false”). | $isApproved = ($userInput === 'true') ? true : false; |
Explanation of Techniques:
- Escaping: This involves adding escape characters (e.g., backslashes) before special characters in strings. For example, in MySQL, single quotes, double quotes, and backslashes need to be escaped.
- Character Encoding: Ensure the correct character encoding (e.g., UTF-8) is used throughout the application and database to prevent character-based attacks.
- Removing or Replacing Special Characters: Remove or replace characters that can be used to manipulate SQL queries, such as single quotes, double quotes, semicolons, and comment markers.
- Type Casting: Convert the input to the expected data type (e.g., `(int)` for integers).
- Format Validation: Verify that the input conforms to a specific format (e.g., date formats, email addresses).
- Regular Expressions: Use regular expressions to validate and sanitize input by matching against predefined patterns and removing or replacing unwanted characters.
Parameterized Queries and Prepared Statements

Parameterized queries and prepared statements are fundamental techniques for preventing SQL injection vulnerabilities in cloud applications. They offer a robust and reliable approach to handling user-supplied data within SQL queries, ensuring that malicious input is treated as data rather than executable code. This approach is crucial for maintaining the security and integrity of cloud-based databases.
Parameterized Queries and Prepared Statements: Mitigation of SQL Injection Risks
Parameterized queries significantly mitigate SQL injection risks by separating the SQL code from the data. This separation prevents malicious actors from injecting SQL code into the query. Instead, the application sends the SQL query structure and the data separately to the database. The database then treats the data as literal values, not executable commands. This process effectively neutralizes any injected SQL code.
Code Examples: Prepared Statements in Popular Cloud Application Languages
Prepared statements are precompiled SQL statements that can be executed multiple times with different parameters. This approach offers both security and performance benefits. Below are examples illustrating the use of prepared statements in Python, Java, and Node.js, common languages for cloud application development.
- Python (using `psycopg2` for PostgreSQL):
In Python, using the `psycopg2` library, prepared statements are created and executed with parameterized values.
import psycopg2 try: conn = psycopg2.connect(database="mydatabase", user="myuser", password="mypassword", host="localhost", port="5432") cur = conn.cursor() # Prepared statement to select a user by username sql = "SELECT- FROM users WHERE username = %s" username = "malicious_user' --" # Example of potential SQL injection if not parameterized cur.execute(sql, (username,)) # Passing username as a parameter rows = cur.fetchall() for row in rows: print(row) except psycopg2.Error as e: print(f"Database error: e") finally: if conn: cur.close() conn.close() In this Python example, the `%s` placeholder in the SQL query indicates where the `username` parameter will be inserted. The `cur.execute()` method takes the SQL query and a tuple containing the parameter values. The database driver handles the escaping and quoting of the `username` value, preventing SQL injection.
In Java, JDBC (Java Database Connectivity) is used to interact with databases. Prepared statements are created using the `prepareStatement()` method.
import java.sql.*; public class PreparedStatementsExample public static void main(String[] args) String dbUrl = "jdbc:postgresql://localhost:5432/mydatabase"; String dbUser = "myuser"; String dbPassword = "mypassword"; try (Connection conn = DriverManager.getConnection(dbUrl, dbUser, dbPassword)) // Prepared statement to insert a new user String sql = "INSERT INTO users (username, password) VALUES (?, ?)"; PreparedStatement pstmt = conn.prepareStatement(sql); String username = "new_user"; String password = "secure_password"; pstmt.setString(1, username); // Set the first parameter pstmt.setString(2, password); // Set the second parameter int rowsAffected = pstmt.executeUpdate(); System.out.println(rowsAffected + " row(s) affected."); catch (SQLException e) System.err.println("SQL Exception: " + e.getMessage()); The Java code demonstrates how to create a `PreparedStatement` and set parameter values using `setString()`. The `?` placeholders in the SQL query are replaced with the provided values. JDBC handles the necessary escaping and quoting.
In Node.js, the `pg` library provides a PostgreSQL client. Prepared statements are created and executed using the `client.query()` method with an array of parameters.
const Client = require('pg'); async function runQuery() const client = new Client( user: 'myuser', host: 'localhost', database: 'mydatabase', password: 'mypassword', port: 5432, ); try await client.connect(); // Prepared statement to select a user by ID const query = text: 'SELECT- FROM users WHERE id = $1', values: [1], // Parameter values ; const result = await client.query(query); console.log(result.rows); catch (err) console.error('Error executing query', err); finally await client.end(); runQuery(); In this Node.js example, the `$1` placeholder represents the first parameter. The `values` array contains the parameter values. The `pg` library correctly handles the parameterization, preventing SQL injection.
Comparison Table: Parameterized Queries vs. String Concatenation
This table compares the advantages and disadvantages of using parameterized queries (prepared statements) versus string concatenation for building SQL queries. String concatenation is highly discouraged due to its vulnerability to SQL injection.
| Feature | Parameterized Queries | String Concatenation | Notes |
|---|---|---|---|
| Security | Significantly reduces the risk of SQL injection. Input is treated as data, not executable code. | Highly vulnerable to SQL injection. User-supplied data is directly inserted into the query string. | Parameterized queries are the secure default. |
| Performance | Can improve performance, especially for frequently executed queries, as the query plan can be cached. | Generally slower, as the database must recompile the query each time, especially with varying input. | Prepared statements can lead to performance gains through query plan caching. |
| Readability | Improves code readability and maintainability by separating the SQL query structure from the data. | Can lead to less readable and more complex code, particularly with many parameters. | Parameter markers make queries cleaner and easier to understand. |
| Complexity | Requires understanding and use of parameterized query syntax (e.g., placeholders). Most database drivers provide this functionality. | Simpler to write initially, but significantly increases the risk of vulnerabilities and maintenance. | The initial complexity is minimal, and the security benefits far outweigh the small learning curve. |
Least Privilege Principle
Implementing the least privilege principle is a critical security measure in cloud environments, especially when addressing SQL injection vulnerabilities. This principle dictates that users and applications should only be granted the minimum necessary access rights to perform their designated tasks. By limiting the scope of potential damage, the least privilege principle significantly reduces the impact of a successful SQL injection attack.
Applying the Least Privilege Principle to Database Access
The application of the least privilege principle in database access focuses on carefully defining and restricting the permissions granted to database users. This involves analyzing the specific operations each user or application needs to perform and granting only those privileges. For instance, a web application that only needs to read data from a database should be granted only SELECT privileges, not UPDATE, INSERT, or DELETE.
This prevents an attacker, exploiting a SQL injection vulnerability, from modifying or deleting data, even if they can execute malicious SQL code.
Configuring Database User Permissions to Minimize Attack Impact
To minimize the impact of a potential SQL injection attack, database user permissions must be configured meticulously. This typically involves the following steps:
- Identify User Roles: Determine the different roles that interact with the database, such as web application users, data analysts, and system administrators.
- Define Access Requirements: For each role, identify the specific database operations required. For example, a data analyst might need SELECT and JOIN privileges on specific tables, while a web application user might only need SELECT privileges on a subset of tables.
- Grant Minimal Permissions: Grant only the necessary privileges to each role. Avoid granting broad permissions like “GRANT ALL PRIVILEGES” unless absolutely necessary.
- Use Specific Permissions: Instead of granting broad permissions, use more granular permissions. For example, grant SELECT permission on specific columns within a table, rather than the entire table.
- Regularly Review Permissions: Periodically review and audit user permissions to ensure they remain appropriate and that no unnecessary privileges have been granted over time.
- Implement Principle of Separation of Duties: Ensure that no single user has excessive privileges. For example, the person who develops the database schema should not have the same level of access as the person who administers the database.
Best Practices for Managing Database User Roles and Permissions in Cloud Environments
Managing database user roles and permissions effectively is crucial for maintaining a robust security posture in cloud environments. The following best practices should be followed:
- Use Role-Based Access Control (RBAC): Implement RBAC to simplify permission management. Define roles with specific privileges and assign users to these roles. This reduces the complexity of managing individual user permissions.
- Automate Permission Management: Use Infrastructure as Code (IaC) tools to automate the provisioning and management of database users and permissions. This ensures consistency and reduces the risk of human error.
- Regularly Audit Permissions: Implement regular audits of database user permissions to identify and remediate any unauthorized access or excessive privileges. Consider using automated tools for this purpose.
- Monitor for Anomalous Activity: Implement monitoring and alerting systems to detect any unusual database activity, such as a sudden increase in queries or attempts to access unauthorized data.
- Isolate Database Instances: Where possible, isolate database instances to limit the blast radius of a potential attack. This means each application or service should have its own dedicated database instance with only the necessary connections.
- Employ Multi-Factor Authentication (MFA): Enforce MFA for all database access, including administrative access, to enhance security.
- Document Permissions: Maintain clear and up-to-date documentation of all database user roles, permissions, and access control policies. This is crucial for auditing and compliance purposes.
- Test Permission Configurations: Regularly test the permission configurations to ensure they function as intended and that users only have the necessary access. This can involve penetration testing or simulated attacks.
- Consider Using Secrets Management: Securely store database credentials using a secrets management solution. This helps to prevent hardcoding credentials in applications and reduces the risk of exposure.
- Apply the Principle of Defense in Depth: Implement multiple layers of security controls, including input validation, parameterized queries, and the least privilege principle, to create a robust defense against SQL injection attacks.
Web Application Firewalls (WAFs)
Web Application Firewalls (WAFs) are a crucial component in defending cloud applications against SQL injection attacks. They act as a security layer, inspecting incoming HTTP/HTTPS traffic and identifying malicious requests before they reach the application server. By analyzing traffic patterns and applying predefined rules, WAFs can effectively detect and block a wide range of SQL injection attempts, helping to protect sensitive data and maintain application integrity.
Detecting and Blocking SQL Injection Attempts
WAFs employ a multi-faceted approach to detect and block SQL injection attempts. They analyze incoming requests for suspicious patterns, comparing them against a set of rules designed to identify malicious payloads.
- Signature-Based Detection: WAFs utilize signature-based detection, comparing incoming requests against a database of known SQL injection attack patterns (signatures). When a match is found, the request is blocked or logged. These signatures often include common SQL injection s (e.g., “SELECT,” “UPDATE,” “DROP”) and attack vectors.
- Anomaly Detection: Some WAFs employ anomaly detection techniques. They establish a baseline of normal application behavior and flag requests that deviate significantly from this baseline. This can help identify zero-day attacks or sophisticated SQL injection attempts that don’t match known signatures.
- Behavioral Analysis: WAFs can also analyze the behavior of requests, looking for unusual patterns such as multiple requests to the same resource in a short period or unexpected data types in input fields. This helps identify and block automated SQL injection attempts and other malicious activities.
- Rate Limiting: WAFs can implement rate limiting to prevent attackers from overwhelming the application with a large number of requests. This helps mitigate brute-force attacks and denial-of-service attacks that may be used in conjunction with SQL injection.
Examples of WAF Rulesets
WAF rulesets are collections of rules that define how a WAF should inspect and respond to incoming traffic. These rules are often written in a specific language, such as the Open Web Application Security Project (OWASP) ModSecurity Core Rule Set (CRS). Here are some examples of WAF rulesets that protect against common SQL injection patterns:
- Filtering: Rules that block or flag requests containing common SQL injection s like “SELECT,” “UPDATE,” “INSERT,” “DELETE,” “DROP,” “UNION,” “WHERE,” and “OR.” For example, a rule might block any request containing the string “SELECT
– FROM users”. - Special Character Filtering: Rules that detect and block requests containing special characters often used in SQL injection, such as single quotes (‘), double quotes (“), backslashes (\), and semicolons (;). For instance, a rule could be designed to block any input that includes a single quote without proper escaping.
- SQL Injection Payload Detection: Rules that identify common SQL injection payloads, such as those used to bypass authentication, retrieve sensitive data, or modify database contents. For example, a rule might look for patterns like “1=1” or “OR 1=1–“.
- HTTP Parameter Analysis: Rules that analyze the values of HTTP parameters (e.g., GET and POST parameters) for SQL injection attempts. For instance, a rule might check the length and content of parameters to identify suspicious patterns.
- SQL Injection Heuristics: Rules that use heuristics to identify SQL injection attempts. These rules may look for combinations of s, special characters, and other indicators of malicious activity.
Cloud-Based WAF Solutions
Several cloud providers offer WAF solutions designed to protect web applications from SQL injection and other web-based attacks. These solutions often provide a range of features, including automated rule updates, bot mitigation, and DDoS protection. The following table details some of the features of various cloud-based WAF solutions.
| Feature | AWS WAF | Cloudflare WAF | Google Cloud Armor |
|---|---|---|---|
| Deployment | Deployed at the edge, integrates with other AWS services (e.g., CloudFront, Application Load Balancer). | Globally distributed network, operates at the edge of Cloudflare’s network. | Globally distributed network, integrates with Google Cloud Load Balancers. |
| Rule Sets | Managed rules (AWS Managed Rules, OWASP Core Rule Set), custom rules. | Managed rules (OWASP Core Rule Set, Bot Management), custom rules. | Managed rules (Google Cloud Armor Managed Rules, OWASP Core Rule Set), custom rules. |
| SQL Injection Protection | Pre-configured SQL injection rules, custom rule creation. | Pre-configured SQL injection rules, custom rule creation. | Pre-configured SQL injection rules, custom rule creation. |
| Bot Mitigation | Bot control features, CAPTCHA challenges. | Bot management, bot score-based mitigation. | Bot protection, rate limiting. |
| DDoS Protection | Layer 3, 4, and 7 DDoS protection. | Comprehensive DDoS protection. | DDoS protection. |
| Pricing | Pay-as-you-go based on usage. | Subscription-based, various tiers. | Pay-as-you-go based on usage. |
Regular Expression Usage
Regular expressions (regex) offer a powerful method for input validation, enabling developers to define patterns that user-provided data must match. This can be an effective layer of defense against SQL injection, as it allows for the identification and rejection of potentially malicious input before it reaches the database. However, it’s crucial to understand both the strengths and limitations of this approach.
Effective Use of Regular Expressions for Input Validation
Regular expressions are most effective when used to validate the format of specific input fields, such as email addresses, phone numbers, or numeric values. By defining a precise pattern, you can ensure that the input conforms to the expected structure, thereby reducing the likelihood of SQL injection attempts.For example, consider validating a user’s input for a username. You might want to allow only alphanumeric characters and underscores.
A regular expression like `^[a-zA-Z0-9_]+$` could be used to enforce this rule. This pattern means:* `^`: Matches the beginning of the string.
`[a-zA-Z0-9_]`
Matches any lowercase or uppercase letter, any digit, or an underscore.
`+`
Matches one or more occurrences of the preceding character set.
`$`
Matches the end of the string.Here’s how this could be implemented in PHP:“`php “`In this code:* `$_POST[‘username’]` retrieves the username from the submitted form data.
- `preg_match()` attempts to match the regular expression pattern against the username.
- If the pattern matches (the username is valid), the code proceeds. Otherwise, an error message is displayed.
Another example involves validating an email address:“`php “`This regular expression for email validation is more complex, checking for the basic structure of an email address, including the “@” symbol and a domain name. The regex checks for a valid structure:
`^[a-zA-Z0-9._%+-]+`
Matches one or more alphanumeric characters, periods, underscores, percentage signs, plus or minus signs at the beginning.
`@`
Matches the “@” symbol.
`[a-zA-Z0-9.-]+`
Matches one or more alphanumeric characters, periods, or hyphens.
`\.`
Matches a period (escaped because “.” has special meaning in regex).
`[a-zA-Z]2,$`
Matches two or more letters at the end (for the top-level domain).Regular expressions can also be used to filter out specific s or patterns commonly associated with SQL injection attempts. However, this approach is generally less effective than validating input format.
Filtering Out Malicious SQL Code with Regular Expressions
While format validation is the primary use case, regular expressions can also be employed to filter out common SQL injection attempts. This involves creating patterns that identify potentially dangerous s or sequences of characters. However, this approach is prone to bypasses.Here are some examples:* Preventing the use of `DROP TABLE`: You could use a regex to block this specific command. “`php “` The `i` flag makes the match case-insensitive.
This regex looks for the `DROP TABLE` command, which could be used to delete tables.
Blocking comment characters
SQL injection often uses comments to hide malicious code. “`php “` This checks for comment indicators (`–` or `/*`).* Preventing use of SQL s: You can block SQL s like `SELECT`, `UPDATE`, `INSERT`, `DELETE`, etc. “`php “` The `\b` represents a word boundary, preventing false positives.These examples demonstrate how regular expressions can be used to identify and block specific SQL injection attempts.
However, they are not foolproof. Attackers can often find ways to bypass these filters.
Potential Limitations of Relying Solely on Regular Expressions for SQL Injection Prevention
Relying solely on regular expressions for SQL injection prevention has significant limitations. Regular expressions are best suited for validating the format of input, not for comprehensively detecting and preventing all SQL injection attacks.Here are some key limitations:* Bypassability: Attackers are constantly developing new techniques to bypass regex-based filters. They can use various encoding methods, different character combinations, or obscure syntax to evade detection.
For example, an attacker might use hexadecimal encoding or string concatenation to hide malicious SQL code.
Complexity
Creating comprehensive regular expressions to cover all possible SQL injection attack vectors is extremely complex and difficult to maintain. Such regex would likely become overly long and prone to errors.
False Positives
Overly restrictive regular expressions can lead to false positives, blocking legitimate user input and disrupting application functionality.
Performance
Complex regular expressions can impact application performance, especially when used on high-traffic websites.
Limited Scope
Regular expressions are generally ineffective against SQL injection techniques that do not involve specific s or patterns, such as those that exploit type confusion or other vulnerabilities in the database.Therefore, while regular expressions can be a valuable tool in input validation, they should not be the sole line of defense against SQL injection. They should be used in conjunction with other security measures, such as parameterized queries, input sanitization, and web application firewalls.
Error Handling and Information Disclosure
Robust error handling is a critical aspect of secure cloud application development. Improperly configured error messages can inadvertently reveal sensitive information about the application’s internal workings, database structure, and underlying infrastructure, providing attackers with valuable insights that can be exploited for malicious purposes. This section focuses on the best practices for designing secure error handling mechanisms in cloud environments.
Configuring Error Handling to Prevent Sensitive Information Leakage
Effective error handling involves carefully managing how the application responds to unexpected events or errors. The primary goal is to provide useful feedback for debugging and troubleshooting without exposing sensitive information to potential attackers. This balance is achieved through a combination of techniques, including logging, user-friendly error messages, and secure exception handling.A common pitfall is displaying detailed error messages directly to users.
These messages can inadvertently expose information about the database schema, server configuration, or internal code structure. For instance, an error message revealing the specific version of a database management system (DBMS) or the exact SQL query that failed can provide attackers with a significant advantage.
Detailed Error Messages and Information for Attackers
Detailed error messages can inadvertently provide attackers with valuable information. Such information can be used to craft targeted attacks. The following are examples of how detailed error messages can be exploited:
- Database Schema Exposure: Error messages can reveal table names, column names, and data types within the database. An attacker can use this information to construct SQL injection payloads that target specific parts of the database. For example, an error message stating “Column ‘username’ not found in table ‘users'” clearly indicates the existence of a “users” table with a “username” column.
- Server-Side Code Information: Error messages may expose file paths, code snippets, and function names. This information can assist attackers in identifying vulnerabilities within the application’s code. A message like “Error in file /var/www/html/login.php on line 42” reveals the file path and line number where an error occurred, making it easier for an attacker to pinpoint the problematic code.
- Technology Stack Disclosure: Error messages often include information about the technologies used by the application, such as the web server, programming language, and database system. This information helps attackers tailor their attacks to specific vulnerabilities known to exist in these technologies. For instance, an error message mentioning “MySQL 5.7” immediately tells an attacker which version of MySQL is being used, allowing them to search for known exploits.
- Authentication Information: Errors related to authentication can sometimes reveal details about the authentication process, such as the type of authentication used (e.g., password-based, token-based) or the names of authentication-related functions. This information can be useful for attackers attempting to bypass authentication mechanisms.
Guidelines for Designing Secure Error Handling Mechanisms
Designing secure error handling mechanisms requires careful consideration of the information that is displayed to users versus what is logged internally. The following guidelines should be followed:
- Log Detailed Errors Internally: Implement comprehensive logging to capture detailed error information, including stack traces, database queries, and sensitive data. This information should be stored securely and only accessible to authorized personnel for debugging and troubleshooting purposes.
- Display Generic Error Messages to Users: Instead of displaying detailed error messages, provide generic, user-friendly messages that do not reveal sensitive information. Examples include “An error occurred while processing your request. Please try again later.” or “We are experiencing technical difficulties. Please contact support.”
- Implement Custom Error Pages: Design custom error pages for common HTTP status codes (e.g., 404 Not Found, 500 Internal Server Error). These pages should provide a consistent user experience and avoid exposing internal details.
- Sanitize Error Data: If any error data needs to be displayed, sanitize it to prevent cross-site scripting (XSS) vulnerabilities. This involves encoding or escaping special characters to prevent them from being interpreted as HTML or JavaScript.
- Regularly Review Error Logs: Regularly review error logs to identify potential security issues, such as unusual error patterns or suspicious activity. This helps to proactively detect and address vulnerabilities before they can be exploited.
- Use a Centralized Logging System: Utilize a centralized logging system to collect and analyze logs from all components of the cloud application. This facilitates efficient monitoring, analysis, and alerting.
- Monitor for Sensitive Data Exposure: Implement measures to prevent the exposure of sensitive data, such as passwords, API keys, and personally identifiable information (PII), in error messages or logs. Mask or redact sensitive data before logging it.
- Consider Error Handling Frameworks: Leverage error handling frameworks or libraries provided by the programming language or cloud platform. These frameworks often provide built-in mechanisms for logging, sanitizing, and displaying error messages securely.
Code Reviews and Security Audits
Regular code reviews and comprehensive security audits are crucial components of a robust security strategy for cloud applications. These practices help identify vulnerabilities early in the development lifecycle, reducing the risk of SQL injection and other security threats. Implementing these processes proactively minimizes the attack surface and strengthens the overall security posture of the application.
Importance of Regular Code Reviews
Code reviews are an essential practice for ensuring the security and quality of cloud application code. They involve a thorough examination of the codebase by peers, focusing on identifying potential vulnerabilities, including SQL injection flaws. Regular code reviews promote a culture of security awareness and help to ensure that developers adhere to secure coding practices.The benefits of conducting code reviews include:
- Early Vulnerability Detection: Code reviews can identify SQL injection vulnerabilities early in the development process, before the code is deployed to a production environment. This allows developers to fix the vulnerabilities before they can be exploited.
- Improved Code Quality: Reviews improve the overall quality of the codebase, leading to more maintainable and reliable software.
- Knowledge Sharing: Code reviews facilitate knowledge sharing among developers, improving the team’s understanding of secure coding practices.
- Compliance: Code reviews can help meet regulatory and compliance requirements.
Conducting a Security Audit
A security audit is a comprehensive assessment of a cloud application’s security posture. This process involves evaluating the application’s design, implementation, and operational practices to identify potential vulnerabilities and weaknesses. A security audit typically includes vulnerability scanning, penetration testing, and a review of the application’s security policies and procedures.The steps involved in conducting a security audit are:
- Planning and Scope Definition: Define the scope of the audit, including the application’s functionality, target environment, and specific security objectives.
- Information Gathering: Collect information about the application, including its architecture, technology stack, and data flow.
- Vulnerability Assessment: Use automated tools and manual techniques to identify potential vulnerabilities, including SQL injection flaws. This might involve source code analysis, dynamic analysis (e.g., fuzzing), and configuration reviews.
- Penetration Testing: Simulate real-world attacks to test the application’s defenses and identify exploitable vulnerabilities.
- Reporting and Remediation: Document the findings, including identified vulnerabilities and their severity. Provide recommendations for remediation and track the progress of fixes.
- Retesting: Verify that the identified vulnerabilities have been successfully addressed.
Code Review Checklist Template for SQL Injection
A code review checklist helps ensure that all aspects of SQL injection prevention are considered during the code review process. This checklist provides a structured approach to identifying and mitigating SQL injection vulnerabilities.The following checklist can be used during code reviews to identify SQL injection vulnerabilities:
- Input Validation: Verify that all user inputs are validated to ensure they conform to expected formats and lengths.
- Input Sanitization: Check for proper sanitization of user inputs to remove or neutralize potentially malicious characters.
- Parameterized Queries/Prepared Statements: Confirm that parameterized queries or prepared statements are used to prevent SQL injection.
- Escaping User Input: Ensure that user input is properly escaped when constructing SQL queries (if parameterized queries are not feasible). However, parameterized queries are always the preferred method.
- Least Privilege Principle: Review database access permissions to ensure the application uses the least privilege necessary.
- Error Handling: Check that error messages do not reveal sensitive information about the database structure or queries.
- Code Style and Security Best Practices: Confirm that the code adheres to secure coding standards and best practices.
- Dependency Analysis: Verify that all dependencies are up-to-date and free of known vulnerabilities.
For example, when reviewing a database query, the checklist might include these specific checks:
- Check: Is a parameterized query or prepared statement used?
- If Not: Is user input properly escaped using the database-specific escaping mechanism?
- Check: Are all user-supplied values being used directly in the SQL query without any sanitization or escaping?
- If Yes: Flag the query as a potential SQL injection vulnerability.
Database Security Best Practices
Implementing robust database security practices is crucial to mitigating SQL injection vulnerabilities in cloud applications. This involves configuring the database itself, securing connections, and regularly monitoring and auditing database activities. These practices, when combined with the input validation, parameterized queries, and other measures discussed earlier, significantly enhance the overall security posture of your application and data.
Database Configuration to Reduce SQL Injection Risks
Securing the database configuration involves several key settings that limit the potential impact of a successful SQL injection attack. This includes carefully managing user permissions, enabling auditing, and keeping the database software up to date. These measures reduce the attack surface and make it harder for attackers to gain unauthorized access or execute malicious code.
- Restrict Database User Privileges: Grant users only the minimum necessary privileges. Avoid using highly privileged accounts (e.g., `sa` or `root`) for application database connections. This principle of least privilege limits the damage an attacker can inflict if they compromise a user account.
- Disable Unnecessary Features: Disable or uninstall any database features that are not required for your application. This reduces the attack surface by eliminating potential entry points for attackers. For example, if you’re not using extended stored procedures, disable them.
- Enable Database Auditing: Configure database auditing to log all relevant database activities, including login attempts, data access, and SQL statement execution. This provides a detailed record of database activity, which can be invaluable for detecting and investigating suspicious behavior or potential SQL injection attempts. Auditing logs should be regularly reviewed and securely stored.
- Regularly Update Database Software: Keep your database software and related components (e.g., drivers, connectors) up to date with the latest security patches. Software updates often include fixes for known vulnerabilities, including those that could be exploited through SQL injection. Implement a regular patching schedule.
- Implement Strong Authentication: Enforce strong password policies and consider multi-factor authentication (MFA) for database user accounts, especially for administrative access. This makes it harder for attackers to gain unauthorized access to the database.
- Configure Database Firewall (if available): Some database systems offer built-in firewall capabilities that can be used to monitor and filter SQL traffic. Configure these firewalls to block suspicious queries and prevent unauthorized access attempts.
Securing Database Connections in Cloud Environments
Securing database connections in cloud environments is critical, given the distributed nature of cloud applications. This involves using encrypted connections, securely managing credentials, and implementing network segmentation to isolate database instances. These measures protect data in transit and prevent unauthorized access from compromised systems.
- Use Encrypted Connections (TLS/SSL): Always use encrypted connections (e.g., TLS/SSL) to protect data in transit between your application and the database. This prevents attackers from intercepting and reading sensitive information, such as credentials or data being queried.
- Securely Store and Manage Database Credentials: Never hardcode database credentials in your application code. Use a secure secrets management service (e.g., AWS Secrets Manager, Azure Key Vault, Google Cloud Secret Manager) to store and manage credentials. Rotate credentials regularly.
- Implement Network Segmentation: Isolate your database instances within a private network, accessible only to authorized applications. This limits the attack surface and prevents attackers from directly accessing the database from the public internet. Use security groups or network access control lists (ACLs) to restrict network traffic.
- Use Database Proxies: Consider using a database proxy to add an additional layer of security. Proxies can provide features like connection pooling, query caching, and traffic filtering, enhancing performance and security.
- Monitor Connection Activity: Regularly monitor database connection activity for suspicious patterns, such as unusual connection attempts, excessive query volumes, or connections from unexpected IP addresses. Use monitoring tools to alert you to potential security threats.
Database Security Hardening Measures
Database security hardening involves implementing a comprehensive set of measures to strengthen the security posture of your database systems. These measures should be continuously reviewed and updated to address evolving threats and vulnerabilities. This includes implementing access controls, regular backups, and security audits.
- Implement Strong Access Controls: Enforce strict access controls based on the principle of least privilege. Regularly review and update user permissions to ensure they align with current business needs.
- Regularly Back Up and Test Database Backups: Implement a robust backup and recovery strategy to protect against data loss. Regularly test your backups to ensure they can be successfully restored in case of a disaster.
- Perform Regular Security Audits and Penetration Testing: Conduct regular security audits and penetration testing to identify vulnerabilities and weaknesses in your database security configuration. Address any findings promptly.
- Monitor Database Performance and Security Logs: Continuously monitor database performance and security logs for any suspicious activity or anomalies. Use security information and event management (SIEM) systems to aggregate and analyze logs.
- Implement Data Encryption at Rest: Encrypt sensitive data at rest to protect it from unauthorized access if the database is compromised. This can involve using database-level encryption features or full disk encryption.
- Stay Informed About Database Security Best Practices: Keep up-to-date with the latest database security threats, vulnerabilities, and best practices. Subscribe to security alerts from your database vendor and industry organizations.
Security Information and Event Management (SIEM) Systems
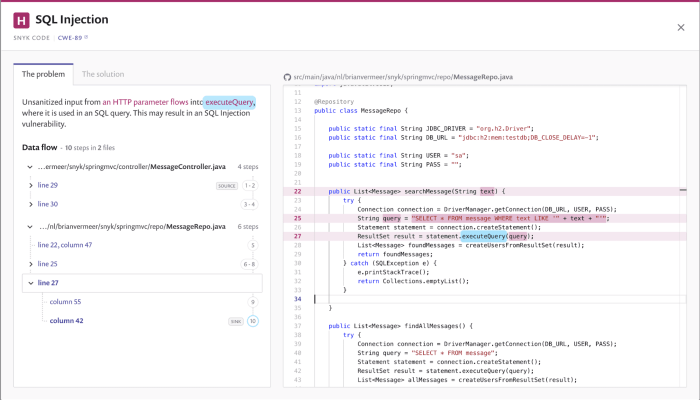
SIEM systems play a crucial role in proactively identifying and responding to potential SQL injection attacks within cloud environments. By centralizing and analyzing security-related data, SIEMs provide real-time visibility into database activities, enabling security teams to detect and mitigate threats effectively. They collect logs from various sources, including databases, web servers, and network devices, to identify suspicious patterns and anomalies that might indicate an ongoing SQL injection attempt.
SIEMs and SQL Injection Detection
SIEM systems are designed to monitor and analyze security events, providing valuable insights into potential SQL injection attacks. They achieve this by collecting and correlating security data from various sources, including database logs, web server logs, and network traffic.
- Log Collection and Aggregation: SIEMs gather logs from diverse sources, such as database management systems (DBMS), web servers, and network devices. These logs contain valuable information about user activities, database queries, and network traffic.
- Event Correlation: SIEMs correlate events from different sources to identify potential threats. For instance, a SIEM might correlate a series of failed login attempts on a web server with unusual database queries, which could indicate an SQL injection attempt.
- Anomaly Detection: SIEMs employ various techniques to detect anomalies in database activity. This includes monitoring query patterns, detecting unusual data access, and identifying suspicious user behavior.
- Alerting and Reporting: SIEMs generate alerts when suspicious activities are detected. These alerts are typically sent to security teams, allowing them to investigate and respond to potential threats. SIEMs also provide reporting capabilities, which can be used to track security incidents and generate compliance reports.
Configuring SIEM Alerts for Suspicious Database Activity
Effective alert configuration is crucial for promptly identifying and responding to SQL injection attempts. This involves defining rules and thresholds that trigger alerts based on specific criteria related to database activity.
- Query Pattern Analysis: Configure alerts to trigger when unusual query patterns are detected. This could involve monitoring for queries that contain suspicious s or characters, such as ‘SELECT’, ‘WHERE’, ‘UNION’, and special characters like single quotes (‘) or semicolons (;).
- User Behavior Analysis: Set up alerts to flag unusual user behavior. For example, if a user suddenly starts executing a large number of queries or accessing data they typically don’t access, it could indicate a potential SQL injection attempt.
- Error Message Monitoring: Monitor for specific error messages that might be indicative of SQL injection. For example, if a database returns an error message related to syntax errors or invalid input, it could suggest an injection attempt.
- Thresholds and Baselines: Establish baselines for normal database activity. Alerts can then be configured to trigger when activity deviates significantly from these baselines. For example, if the number of database queries suddenly spikes, it could be a sign of an attack.
- Alert Prioritization and Escalation: Prioritize alerts based on their severity and potential impact. Implement an escalation process to ensure that high-priority alerts are addressed promptly by the appropriate security personnel.
SIEM Solution Comparison
Choosing the right SIEM solution is critical for effectively monitoring and detecting SQL injection attempts. The following table provides a comparison of several SIEM solutions, highlighting their key features and capabilities. This comparison will help you evaluate different solutions based on your specific needs and requirements.
| SIEM Solution | Key Features | SQL Injection Detection Capabilities | Pricing/Licensing |
|---|---|---|---|
| Splunk Enterprise | Scalable architecture, advanced search and analytics, extensive integrations, customizable dashboards. | Real-time monitoring, anomaly detection, custom rule creation, threat intelligence integration, supports regex and pattern matching. | Subscription-based, based on data volume ingested. |
| Microsoft Sentinel | Cloud-native SIEM, integrates with Azure services, machine learning-based threat detection, automated incident response. | Built-in threat detection rules for SQL injection, integrates with Azure Monitor logs, supports custom rule creation, utilizes machine learning for anomaly detection. | Consumption-based pricing, based on data volume ingested and operations performed. |
| Elastic Security | Open-source, scalable, real-time search and analysis, integrates with Elasticsearch, customizable dashboards. | Supports log analysis, pattern matching, anomaly detection, provides pre-built rules for SQL injection, allows for custom rule creation. | Open-source, with commercial features and support available. Pricing depends on the chosen features and usage. |
| IBM QRadar SIEM | Comprehensive security analytics, real-time monitoring, threat intelligence integration, incident response capabilities. | Real-time monitoring of database activity, anomaly detection, pre-built and customizable rules for SQL injection detection, integration with vulnerability scanners. | Subscription-based, based on events per second (EPS) and managed services options. |
Continuous Monitoring and Threat Intelligence

Continuous monitoring and the integration of threat intelligence are crucial for proactively defending against SQL injection attacks in cloud applications. They provide real-time visibility into application behavior, enabling rapid detection and response to malicious activities. This proactive approach helps to minimize the impact of successful attacks and strengthen the overall security posture.
Importance of Continuous Monitoring for Threat Detection and Response
Continuous monitoring is essential for identifying and responding to SQL injection threats. This proactive approach provides real-time insights into application behavior, enabling security teams to detect and mitigate attacks as they occur.
- Real-time Visibility: Continuous monitoring tools provide immediate insights into application activity, allowing for the rapid identification of suspicious behavior that might indicate a SQL injection attempt. This includes monitoring database queries, network traffic, and user activity.
- Early Threat Detection: By analyzing logs, network traffic, and application behavior in real-time, continuous monitoring helps detect SQL injection attempts early in the attack lifecycle, before significant damage can occur.
- Rapid Incident Response: When a potential SQL injection attack is detected, continuous monitoring systems can trigger alerts and provide the information needed to quickly respond to the threat. This might include blocking malicious traffic, isolating compromised systems, or initiating other security measures.
- Improved Security Posture: The data collected through continuous monitoring can be used to improve the overall security posture. Analysis of attack patterns can inform security teams about vulnerabilities that need to be addressed, and provide insights for refining security controls.
- Compliance and Reporting: Continuous monitoring supports compliance efforts by providing detailed logs and reports on security events. This data can be used to demonstrate adherence to regulatory requirements and security best practices.
Integrating Threat Intelligence Feeds
Integrating threat intelligence feeds is a proactive strategy to enhance defenses against evolving SQL injection techniques. By staying informed about the latest threats and attack patterns, security teams can proactively adjust their defenses and mitigate potential risks.
- Staying Informed about Latest Threats: Threat intelligence feeds provide information about emerging SQL injection techniques, vulnerabilities, and attack patterns. This helps security teams stay ahead of attackers and proactively adjust their defenses.
- Proactive Defense Strategies: Integrating threat intelligence allows organizations to proactively identify and address vulnerabilities. This can include updating security configurations, implementing new security controls, or patching systems.
- Improved Alerting and Detection: Threat intelligence feeds can be integrated with security monitoring systems to improve the accuracy and effectiveness of alerts. This helps to reduce false positives and ensure that security teams are alerted to the most critical threats.
- Contextualizing Security Events: Threat intelligence provides context to security events. For instance, if a log entry indicates a suspicious query, threat intelligence can provide information on whether this query is associated with a known SQL injection exploit.
- Prioritizing Vulnerability Management: By identifying the vulnerabilities most likely to be exploited, threat intelligence can help organizations prioritize their vulnerability management efforts. This ensures that resources are focused on the most critical risks.
Comparison of Threat Intelligence Feeds
Threat intelligence feeds offer a variety of features and functionalities. Understanding the differences between these feeds is crucial for selecting the right solution for your specific needs. The following table compares several key features.
| Feature | Feed A | Feed B | Feed C | Feed D |
|---|---|---|---|---|
| Data Sources | Proprietary honeypots, open-source intelligence (OSINT), and commercial data. | OSINT, malware analysis, and vulnerability databases. | OSINT, dark web monitoring, and social media analysis. | Commercial threat intelligence feeds and industry partnerships. |
| Data Types | Indicators of compromise (IOCs), IP addresses, domains, file hashes, and malicious URLs. | IOCs, threat actors, attack patterns, and vulnerability information. | IOCs, threat actor profiles, phishing campaigns, and social engineering tactics. | IOCs, malware signatures, exploit kits, and vulnerability details. |
| Update Frequency | Real-time updates. | Hourly updates. | Daily updates. | Real-time and near real-time updates. |
| Integration Methods | API, STIX/TAXII, and SIEM integration. | API, CSV, and SIEM integration. | API, email alerts, and SIEM integration. | API, STIX/TAXII, and security platform integration. |
| Reporting & Analysis | Detailed reports, dashboards, and threat actor profiles. | Vulnerability analysis, threat actor analysis, and trending reports. | Phishing campaign analysis, social media analysis, and sentiment analysis. | Customizable dashboards, real-time alerts, and threat intelligence reports. |
| Pricing | Subscription-based, tiered pricing. | Freemium model, with paid options. | Free, with limited data. | Subscription-based, enterprise pricing. |
Conclusion
In conclusion, mitigating SQL injection risks in cloud applications requires a multi-layered approach. By embracing input validation, parameterized queries, the principle of least privilege, and robust security tools, organizations can significantly fortify their defenses. Furthermore, continuous monitoring, regular code reviews, and proactive threat intelligence are crucial for staying ahead of evolving threats. Implementing these best practices ensures a more secure and resilient cloud environment, protecting valuable data and maintaining user trust.
FAQ Summary
What is SQL injection?
SQL injection is a web security vulnerability that allows attackers to interfere with queries that an application makes to its database. It typically involves injecting malicious SQL code into input fields, such as login forms or search boxes, to manipulate the database.
What are the most common attack vectors for SQL injection in cloud applications?
Common attack vectors include exploiting vulnerabilities in input fields (e.g., forms, search boxes, URL parameters), insecure coding practices (e.g., string concatenation), and lack of proper input validation and sanitization.
How can I test my cloud application for SQL injection vulnerabilities?
You can use penetration testing tools, vulnerability scanners, and manual testing techniques. These methods involve submitting various inputs, including malicious SQL code, to identify potential vulnerabilities.
What are the differences between input validation and input sanitization?
Input validation checks if the input meets expected criteria (e.g., data type, length, format) before processing. Input sanitization modifies the input to remove or neutralize potentially harmful characters or code, making it safe for use in SQL queries.
Are Web Application Firewalls (WAFs) a complete solution for preventing SQL injection?
While WAFs are valuable, they are not a complete solution. They provide an additional layer of defense, but they should be used in conjunction with other security measures like secure coding practices and input validation.
Tags:
Related Articles
You might also be interested in these articles
Implementing a Secure Software Development Life Cycle (SDLC): A Practical Guide
Protecting your software from vulnerabilities is paramount in today's digital world, and this guide provides a comprehen...

Developing a Data Retention Policy for Regulatory Compliance
In today's complex regulatory environment, establishing a robust data retention policy is crucial for compliance and min...

Data Breach Notification: Compliance Requirements Explained
Discover insights and practical tips in this comprehensive guide about What Are The Compliance Requirements For Data Bre...