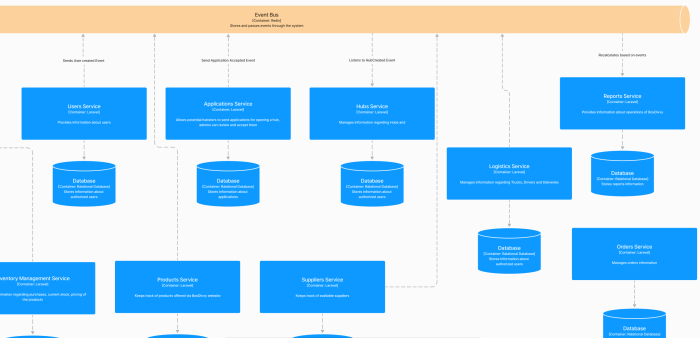
Crafting a robust multi-cloud networking strategy is crucial for businesses seeking to leverage the benefits of multiple cloud providers. This comprehensive guide provides a detailed roadmap for navigating the complexities of designing and implementing such a strategy, encompassing key considerations from planning and resource management to security and cost optimization.
The modern digital landscape demands flexibility and scalability, and a multi-cloud approach offers a solution. This guide dives into the intricacies of designing a multi-cloud networking strategy, ensuring seamless connectivity and optimal performance across different cloud environments. It emphasizes the importance of aligning the strategy with business objectives and understanding the unique security and cost implications of this approach.
Defining Multi-Cloud Networking

Multi-cloud networking is a strategy that leverages multiple cloud providers to enhance application flexibility and resilience. It involves establishing interconnected networks across various cloud environments, allowing seamless data transfer and application deployment. This approach offers significant advantages over traditional single-cloud architectures, but also presents unique challenges.This strategy enables businesses to optimize their cloud usage by leveraging the specific strengths of each provider, such as cost-effectiveness, specific services, or geographical proximity.
By distributing workloads and data across different cloud providers, organizations can achieve higher levels of redundancy, scalability, and disaster recovery capabilities.
Multi-Cloud Deployment Types
Different multi-cloud deployment models cater to diverse organizational needs and requirements. Hybrid cloud deployments combine on-premises infrastructure with one or more public cloud providers. This model offers a balance between control and scalability. Multi-tenant deployments involve sharing cloud resources among multiple organizations, typically in a managed service environment. This model is prevalent in shared hosting and cloud-based applications.
Other deployment models, such as pure multi-cloud (using multiple cloud providers without an on-premises component) or cloud bursting (using a cloud provider as a secondary resource to handle peak demand), also exist, offering unique advantages and disadvantages.
Core Principles of Multi-Cloud Networking
The core principles of multi-cloud networking revolve around efficient communication and resource management across different cloud environments. Key components include network connectivity, security protocols, and management tools. Secure and reliable network connectivity between cloud environments is critical to enabling seamless data exchange and application performance. Robust security protocols are essential to protect sensitive data and prevent unauthorized access.
Effective management tools are required to monitor and control resources across multiple clouds.
Benefits of Multi-Cloud Strategies
Adopting a multi-cloud strategy offers several advantages. Increased flexibility and choice is a primary benefit, allowing organizations to select the best services from various providers, optimizing cost and performance. Enhanced resilience and redundancy is another advantage, minimizing downtime and ensuring business continuity. Improved scalability and performance are achieved by leveraging the strengths of each provider and distributing workloads efficiently.
Drawbacks of Multi-Cloud Strategies
Multi-cloud strategies also present some challenges. Increased complexity in managing multiple cloud environments is a significant concern, demanding dedicated expertise and resources. Integration challenges between different cloud platforms can also arise, requiring significant effort to ensure seamless functionality. Security considerations become more complex as organizations need to manage security across various environments. Cost optimization can be complex to achieve with multiple providers, especially with unpredictable usage patterns and the need to monitor and manage costs across various accounts.
Single-Cloud vs. Multi-Cloud Architectures
| Feature | Single-Cloud Architecture | Multi-Cloud Architecture |
|---|---|---|
| Vendor Lock-in | High | Low |
| Cost Optimization | Potentially limited | Potentially higher |
| Scalability | Limited by single provider’s capacity | Enhanced by leveraging multiple providers |
| Resiliency | Dependent on single provider’s reliability | Enhanced by distributing workloads and data |
| Flexibility | Limited to the services offered by a single provider | Greater flexibility in choosing services from multiple providers |
| Complexity | Lower | Higher |
| Security | Managed by a single provider | Requires managing security across multiple providers |
This table highlights the key differences between single-cloud and multi-cloud architectures. Single-cloud environments often present higher vendor lock-in, while multi-cloud deployments allow for greater flexibility and potential cost optimization.
Planning the Strategy

Developing a robust multi-cloud networking strategy is crucial for organizations seeking to leverage the benefits of multiple cloud providers. This involves careful planning, meticulous execution, and a clear understanding of the intricate interplay between different cloud environments. A well-defined strategy ensures optimal resource utilization, enhanced security, and seamless application performance across various cloud platforms.
Aligning with Business Objectives
A successful multi-cloud strategy hinges on its alignment with the overall business objectives. The strategy must support and enable the achievement of key business goals, such as improved scalability, enhanced disaster recovery capabilities, and optimized cost management. Thorough analysis of current business needs and future projections is essential to ensure the multi-cloud network architecture supports evolving requirements. A clear understanding of how the multi-cloud strategy directly contributes to these goals is vital.
Step-by-Step Development Process
A systematic approach to developing a multi-cloud networking strategy is essential for its success. The process should involve the following key steps:
- Assessment of Existing Infrastructure: A comprehensive assessment of the existing network infrastructure and applications is critical. This includes evaluating current hardware, software, and security protocols. Identifying current limitations and strengths within the existing environment helps determine which cloud platforms are most suitable and how to integrate them effectively.
- Defining Cloud Provider Selection Criteria: Organizations must establish specific criteria for selecting cloud providers. These criteria should be based on factors such as cost, security features, compliance requirements, and service-level agreements. Consider the specific needs of different applications and departments when choosing providers.
- Network Design and Architecture: This phase involves creating a detailed network design encompassing the interconnection between different cloud environments. Consider network topologies, routing strategies, and security protocols for optimal performance and security. The design should accommodate future growth and potential changes in the cloud landscape.
- Security Planning: A robust security plan is indispensable in a multi-cloud environment. This plan should encompass policies, procedures, and technologies to protect data and applications across all cloud platforms. This involves a comprehensive risk assessment and implementation of suitable security controls.
- Testing and Validation: Thorough testing and validation of the multi-cloud network are critical to ensure its functionality and security. Simulate various scenarios, including failures and attacks, to assess the network’s resilience and identify potential vulnerabilities. Regular performance monitoring is necessary to ensure consistent operation.
Security Considerations in Multi-Cloud Environments
Multi-cloud environments introduce unique security challenges, necessitating a proactive approach. A robust security plan is crucial to mitigate risks and protect sensitive data. This plan must consider the diverse security protocols and policies of different cloud providers.
| Potential Security Risks | Mitigation Strategies |
|---|---|
| Data breaches across multiple cloud environments | Implementing strong access controls, encryption at rest and in transit, and regular security audits across all cloud platforms. |
| Lack of Visibility across multiple cloud environments | Utilizing centralized security management tools and employing consistent security policies across all cloud platforms. |
| Misconfigurations in cloud environments | Implementing automated security scans and regular vulnerability assessments. Implementing least privilege access policies and regular security awareness training for personnel. |
| Compliance violations across different cloud providers | Ensure that the multi-cloud strategy complies with all relevant industry regulations and standards. Employ tools to monitor compliance and ensure continuous adherence. |
| Compliance variations across cloud providers | Identify the specific compliance requirements of each cloud provider and develop strategies to meet these requirements. Develop a standardized security posture across all cloud platforms. |
Choosing Cloud Providers
Selecting appropriate cloud providers is critical to a successful multi-cloud strategy. This stage demands careful consideration of various factors, ensuring compatibility and optimal performance across different environments. Understanding the unique strengths and weaknesses of each provider is essential for building a resilient and scalable infrastructure.
Key Factors for Provider Selection
Careful evaluation of cloud providers is paramount to achieving the desired outcomes of a multi-cloud strategy. Factors to consider include cost-effectiveness, security measures, performance characteristics, and the specific needs of the applications being deployed. Provider reputations, financial stability, and regulatory compliance also play significant roles in long-term planning. A thorough assessment of these elements ensures a strategic selection process.
Evaluating Provider Interoperability
Interoperability between cloud providers is a crucial aspect of multi-cloud deployments. It refers to the ability of different cloud platforms to communicate and exchange data seamlessly. A lack of interoperability can lead to significant challenges in data migration, application integration, and management across the various clouds. Assessing interoperability ensures that data and applications can be effectively moved and managed across different cloud environments.
Comparison of Networking Capabilities
Cloud providers offer varying networking capabilities, impacting application performance and management complexity. Analyzing these capabilities is vital for selecting the right providers for a specific workload. A deep dive into the specifics of virtual private clouds (VPCs), virtual private networks (VPNs), load balancers, and other networking features is necessary to understand how they support application needs.
Cloud Provider Networking Feature Comparison
| Cloud Provider | VPC | VPN | Load Balancers | Other Features (e.g., DNS, Firewall) |
|---|---|---|---|---|
| Provider A | Highly customizable, robust security features, excellent performance | Secure connectivity, multiple options for network configuration | Flexible scaling, diverse types of load balancing, high availability | Comprehensive DNS management, robust firewall configurations, granular control over security |
| Provider B | Scalable, cost-effective, basic security features | Reliable connectivity, limited customization options | Basic load balancing, limited scaling options | Basic DNS management, firewall capabilities, less granular control |
| Provider C | Advanced features, premium pricing, excellent performance | Highly secure, comprehensive customization | Advanced features, extensive scaling options, high availability | Extensive DNS management, advanced firewall capabilities, detailed control over security |
This table provides a basic comparison of networking features offered by different cloud providers. The specific features and their implementations can vary considerably between providers, so it is crucial to thoroughly research and assess the providers to ensure alignment with your specific application and infrastructure requirements.
Networking Architecture Design
A well-defined multi-cloud networking architecture is crucial for seamless communication and resource sharing across various cloud environments. This architecture ensures efficient data transfer, secure access, and consistent policies across different cloud providers. Effective design considerations are essential to support application performance, scalability, and security in a dynamic multi-cloud landscape.This section details different multi-cloud networking architectures, their component roles, and practical use cases.
It also presents a comprehensive table illustrating the interactions between networking components within a multi-cloud environment.
Multi-Cloud Networking Architectures
Different approaches to connecting cloud resources across multiple providers shape the overall multi-cloud networking strategy. Key architectures include overlay and underlay models.
- Overlay Networking: This approach abstracts the underlying physical infrastructure of each cloud. Virtual networks are created on top of the existing cloud networks, providing a consistent view of the resources across different providers. Overlay networks enable consistent networking policies and simplified management, irrespective of the physical locations of the resources. This simplifies management and security enforcement across different cloud providers.
- Underlay Networking: In contrast to overlay, underlay networking directly connects the physical networks of different cloud providers. This approach often involves VPNs and dedicated connections, offering greater control and potentially lower latency, but also requires more intricate configuration and management across the cloud providers.
Networking Components in Multi-Cloud
The selection and configuration of networking components directly impact the performance, security, and manageability of a multi-cloud environment.
- Virtual Private Networks (VPNs): VPNs are critical for establishing secure connections between on-premises networks and cloud environments, as well as between different cloud providers. They encrypt data transmissions, protecting sensitive information during transit. A key consideration is ensuring consistent VPN policies across all cloud environments to maintain consistent security.
- Firewalls: Firewalls are essential for controlling network traffic and enforcing security policies. In a multi-cloud setup, firewalls must be strategically placed to monitor and filter traffic between different cloud environments and on-premises locations. Comprehensive security rules are needed to address the diverse security demands of a multi-cloud environment.
- Load Balancers: Load balancers distribute network traffic across multiple cloud instances, ensuring high availability and optimal performance. In a multi-cloud setup, load balancers can be deployed across different providers, providing a scalable and fault-tolerant mechanism for distributing traffic.
Use Cases for Different Architectures
The choice of multi-cloud networking architecture depends on the specific needs of the application and organization.
- Overlay Architecture Use Case: A company with existing applications running in different cloud environments may opt for an overlay architecture to maintain consistency in their network policies and configurations. This allows for easy management and seamless communication between applications running in various cloud providers.
- Underlay Architecture Use Case: A company requiring low latency and high bandwidth for critical applications, such as financial trading or real-time data processing, might employ an underlay architecture. This direct connection offers superior performance compared to overlay, albeit with greater complexity in setup and management.
Multi-Cloud Networking Component Interactions
The table below illustrates the interaction between different networking components within a multi-cloud environment.
| Component | Description | Interaction with other components |
|---|---|---|
| VPN | Securely connects different cloud environments and on-premises networks | Facilitates secure communication between cloud providers and on-premises networks, interacting with firewalls to control traffic |
| Firewall | Controls network traffic and enforces security policies | Works in conjunction with VPNs to filter and monitor traffic, ensuring only authorized traffic passes through |
| Load Balancer | Distributes network traffic across multiple instances | Distributes traffic across multiple instances in different cloud environments, interacting with firewalls for security |
| Overlay Network | Abstracted network on top of existing cloud networks | Provides a consistent network view across different providers, allowing consistent policies across cloud environments |
| Underlay Network | Direct connection of physical networks | Enables high bandwidth and low latency, but requires complex management across different providers |
Inter-Cloud Connectivity
Establishing secure and reliable connections between diverse cloud environments is crucial for a successful multi-cloud strategy. This involves careful consideration of various connectivity methods, security protocols, and potential cost implications. Effective inter-cloud networking allows seamless data exchange and application deployment across different cloud providers, promoting flexibility and resilience.A robust inter-cloud strategy ensures consistent performance, enabling applications to leverage the strengths of multiple cloud providers without compromising security or manageability.
This is vital for businesses seeking to optimize their cloud infrastructure and gain a competitive edge.
Methods for Inter-Cloud Connectivity
Several methods facilitate secure and reliable connections between different cloud environments. These methods range from simple VPN solutions to more complex, dedicated connections. Understanding the nuances of each method is key to making informed decisions.
- Virtual Private Networks (VPNs): VPNs provide encrypted connections over the public internet, enabling secure communication between cloud environments. They are relatively cost-effective but may experience latency issues, particularly for high-bandwidth applications. VPNs can be implemented relatively quickly, making them suitable for initial inter-cloud connections.
- Direct Connect: Direct Connect establishes a dedicated connection between cloud environments using physical or virtual leased lines. This eliminates the latency issues associated with VPNs, enabling faster data transfer rates. Direct Connect solutions are often more expensive than VPNs but are critical for high-performance applications, such as real-time data processing and mission-critical workloads.
- Cloud Interconnects: Cloud providers offer dedicated interconnects that facilitate low-latency, high-bandwidth communication between different cloud environments. These services often come with a variety of features, such as automated routing and traffic management. Cloud interconnects are typically more expensive than VPNs but provide superior performance and greater control.
- Hybrid Cloud Gateways: Hybrid cloud gateways serve as a central point of control for managing traffic between on-premises data centers and cloud environments. They are often used in conjunction with VPNs or Direct Connect, facilitating secure and consistent connectivity across the entire infrastructure. This is particularly useful when managing a hybrid cloud strategy.
Security Considerations for Inter-Cloud Communication
Security is paramount in inter-cloud communication. Comprehensive security measures are essential to protect sensitive data and prevent unauthorized access.
- Authentication and Authorization: Implementing robust authentication and authorization mechanisms is critical to controlling access to inter-cloud resources. This involves using strong passwords, multi-factor authentication, and role-based access control.
- Data Encryption: Encrypting data transmitted between cloud environments is essential to protect sensitive information from unauthorized interception. Strong encryption protocols, such as TLS/SSL, are vital.
- Network Segmentation: Segmenting networks helps isolate sensitive data and applications, limiting the impact of security breaches. Proper network segmentation practices are vital for maintaining security across multiple cloud environments.
- Regular Security Audits: Regularly auditing security protocols and configurations is essential to identify and address vulnerabilities. These audits should be comprehensive and cover all aspects of the inter-cloud connection.
Inter-Cloud Connectivity Cost Analysis
The cost of inter-cloud connectivity varies significantly depending on the chosen method and the volume of data transferred.
| Connectivity Method | Description | Typical Cost Factors |
|---|---|---|
| VPN | Encrypted connection over the public internet | Lower initial cost, potential latency issues, bandwidth costs |
| Direct Connect | Dedicated connection using leased lines | Higher initial cost, lower latency, bandwidth costs |
| Cloud Interconnects | Dedicated connection from cloud provider | High initial cost, high bandwidth, potential service fees |
| Hybrid Cloud Gateways | Central control point for hybrid infrastructure | Cost varies based on complexity and features, integration costs |
Resource Management
Effective resource management is critical for optimizing the performance and cost-effectiveness of a multi-cloud strategy. Properly allocating and monitoring resources across multiple cloud providers ensures consistent service levels and avoids unnecessary expenditure. This involves not only understanding the available resources but also proactively managing their utilization.
Strategies for Managing Resources Across Multiple Cloud Providers
Managing resources across diverse cloud providers requires a comprehensive strategy. This involves consistent monitoring and control across all providers, enabling efficient allocation and preventing overspending. Key strategies include:
- Centralized Resource Visibility and Control: Employing a central platform to monitor and manage resources across all cloud environments is crucial. This allows for real-time insights into resource utilization, enabling proactive adjustments and cost optimization. This ensures visibility into resource allocation across different cloud providers, providing a unified view for effective management.
- Automated Resource Allocation and Scaling: Automation is key for adapting to fluctuating workloads and ensuring resources are available when needed. Automated scaling solutions based on pre-defined rules can dynamically adjust resources, optimizing performance and minimizing costs.
- Standardized Resource Naming and Tagging Conventions: Implementing consistent naming and tagging conventions across all cloud providers simplifies resource identification and management. This makes it easier to track and manage resources across the various cloud platforms.
- Cost Optimization Strategies: Implement strategies to reduce costs associated with resource utilization. This includes optimizing resource configurations for efficiency, leveraging reserved instances where appropriate, and closely monitoring billing reports.
Importance of Centralized Resource Management Tools
Centralized resource management tools provide a single pane of glass for managing resources across multiple cloud providers. This approach significantly simplifies administration and facilitates efficient resource allocation and monitoring. These tools enable proactive cost management and provide a clear picture of overall resource utilization across all platforms.
Examples of Tools That Facilitate Multi-Cloud Resource Management
Several tools are available to facilitate the management of resources in a multi-cloud environment. Some of the prominent examples include:
- Cloudability: Offers a unified view of cloud costs and resource utilization across different cloud providers, facilitating cost optimization and resource management.
- RightScale: A comprehensive platform enabling automated deployment, management, and scaling of applications and infrastructure across multiple clouds. It provides a single interface for orchestrating operations across various cloud platforms.
- CloudBolt Software: A cloud management platform that provides a centralized view of cloud resources and simplifies management across multiple cloud environments. It supports a range of cloud providers and offers automation capabilities.
- Azure Arc: Enables management of on-premises and hybrid resources through a single Azure portal, facilitating a more unified approach to resource management across various environments.
Features of Various Resource Management Tools
The table below showcases a comparison of features offered by some popular multi-cloud resource management tools.
| Tool | Centralized Management | Cost Optimization | Automation | Cloud Provider Support |
|---|---|---|---|---|
| Cloudability | Yes | Excellent | Limited | Multiple |
| RightScale | Yes | Good | Excellent | Multiple |
| CloudBolt Software | Yes | Good | Good | Multiple |
| Azure Arc | Yes | Good | Good | Azure, Hybrid |
Monitoring and Management
Effective multi-cloud networking relies heavily on robust monitoring and management capabilities. Without real-time visibility into network performance across disparate cloud environments, troubleshooting issues and optimizing resource utilization becomes significantly more challenging. This section details the critical aspects of monitoring and managing multi-cloud networks, emphasizing the importance of proactive management and timely issue resolution.Comprehensive monitoring and management strategies are essential for maintaining optimal performance and stability within a multi-cloud infrastructure.
This involves not only identifying and resolving immediate issues but also anticipating potential problems and proactively adjusting configurations to maintain consistent performance and security.
Importance of Network Performance Monitoring
Monitoring network performance across multiple cloud environments is crucial for maintaining service levels and preventing outages. Real-time performance data enables proactive identification of bottlenecks, capacity issues, and security vulnerabilities. Effective monitoring allows for swift identification of issues, enabling faster resolution and minimal impact on end-users.
Tools for Multi-Cloud Network Monitoring and Management
Various tools cater to multi-cloud network monitoring and management needs. Some popular options include:
- Cloud provider-specific tools: Each major cloud provider offers its own suite of monitoring tools. These tools often provide detailed insights into resource utilization, network traffic, and performance metrics within their respective environments. For example, AWS CloudWatch, Azure Monitor, and Google Cloud Monitoring offer comprehensive visibility into cloud resources and network performance within their platforms.
- Third-party network management platforms: Specialized third-party tools offer a unified view across multiple cloud environments. These tools aggregate data from different cloud providers, offering a consolidated dashboard for monitoring and managing the entire multi-cloud infrastructure. These platforms typically provide advanced analytics and reporting capabilities, enabling users to identify trends and patterns in network behavior.
- Network performance monitoring tools: Specialized tools focus on network traffic, latency, and packet loss across the entire network infrastructure, including the connections between different cloud environments. These tools can pinpoint specific points of congestion or bottlenecks, facilitating optimization efforts.
Establishing Alerts for Critical Network Issues
Proactive alerts are vital for swiftly addressing critical network issues. Alerts should be configured for specific thresholds of performance metrics, such as latency exceeding a certain value, packet loss exceeding a percentage, or CPU utilization exceeding a threshold. The configuration of these alerts should consider the specific needs and performance objectives of the organization. These alerts are crucial for preventing service disruptions and minimizing downtime.
Real-Time Visibility into Multi-Cloud Network Activity
Real-time visibility into multi-cloud network activity is paramount for effectively managing and troubleshooting issues. By monitoring network traffic, resource utilization, and performance metrics in real-time, organizations can quickly identify and respond to potential problems. Real-time dashboards and visualizations are key components in achieving this visibility, allowing for immediate identification of issues and their rapid resolution. A unified dashboard providing real-time data from multiple cloud providers is essential.
Security Considerations
Multi-cloud deployments, while offering flexibility and resilience, introduce unique security challenges. Protecting data and applications across diverse cloud environments requires a comprehensive strategy that addresses the specific vulnerabilities inherent in this architecture. A robust security posture is crucial to maintaining business continuity and compliance.Careful consideration of security throughout the multi-cloud lifecycle is paramount. This includes planning, implementation, and ongoing monitoring to ensure the security of data, applications, and infrastructure across all cloud environments.
Security best practices must be consistently applied across all environments, regardless of the cloud provider.
Security Challenges in Multi-Cloud Deployments
Multi-cloud environments present several security challenges compared to single-cloud deployments. These include:
- Varying Security Models: Different cloud providers often employ distinct security models, access controls, and compliance frameworks. Managing consistent security policies across these varied environments can be complex.
- Increased Attack Surface: The expansion of infrastructure across multiple cloud providers expands the attack surface. Compromising one environment can potentially expose others if adequate security measures aren’t in place to prevent cross-environment attacks.
- Data Sprawl and Management: Data residing across multiple clouds requires robust data governance and access control mechanisms. Maintaining data integrity and compliance across these distributed data stores can be complex and resource-intensive.
- Complexity in Identity and Access Management (IAM): Managing user identities and access privileges across multiple cloud environments requires sophisticated IAM solutions to ensure proper authorization and prevent unauthorized access.
Strategies for Securing Inter-Cloud Communication
Effective communication between different cloud environments is essential for seamless application operation. However, this connectivity also presents security risks. Here are crucial strategies:
- Network Segmentation and Virtual Private Clouds (VPCs): Implementing robust network segmentation within and between cloud environments, utilizing VPCs, is vital. This isolates resources and limits the impact of potential breaches.
- Encryption in Transit and at Rest: Employing encryption for all data in transit and at rest across different cloud environments is critical. This ensures data confidentiality and integrity.
- Zero Trust Architecture: Adopting a zero-trust security model mandates verification for every user and device attempting access, regardless of location or environment. This significantly enhances security.
- Security Information and Event Management (SIEM) Integration: Implementing a SIEM solution to collect and analyze security logs from various cloud environments provides a centralized view of security events and potential threats.
Security Best Practices for Multi-Cloud Environments
Implementing best practices across different cloud environments is crucial for robust security.
- Consistent Security Policies and Standards: Establish and enforce consistent security policies and standards across all cloud environments to ensure uniform protection.
- Regular Security Audits and Penetration Testing: Conduct regular security audits and penetration testing to identify vulnerabilities and weaknesses in the multi-cloud architecture.
- Cloud Provider Security Best Practices: Adhere to security best practices recommended by each cloud provider to leverage their security features and services.
- Employee Training and Awareness: Educate employees on security threats and best practices related to multi-cloud environments to mitigate the risk of human error.
Security Protocol Effectiveness in Multi-Cloud Scenarios
The effectiveness of security protocols can vary depending on the specific multi-cloud scenario.
| Security Protocol | Effectiveness in Single-Cloud | Effectiveness in Multi-Cloud | Example Scenario |
|---|---|---|---|
| Secure Shell (SSH) | High | High, but requires careful configuration across providers | SSH access to virtual machines across AWS and Azure |
| Transport Layer Security (TLS/SSL) | High | High, essential for secure communication | Secure data transfer between cloud environments |
| Virtual Private Network (VPN) | High | Moderate, complexity increases with multiple providers | Connecting on-premises networks to multiple cloud environments |
| Cloud Access Security Broker (CASB) | Moderate | High, essential for centralized policy enforcement | Centralized security policies across different cloud environments |
Cost Optimization
Optimizing costs is a crucial aspect of any multi-cloud strategy. A well-designed multi-cloud approach can potentially offer cost advantages over a single-cloud solution by allowing organizations to leverage the best pricing models and services from different providers. Careful planning and execution are paramount to realizing these potential savings.A successful multi-cloud cost optimization strategy necessitates a deep understanding of each cloud provider’s pricing models, service offerings, and resource utilization patterns.
This understanding is essential to identify opportunities for cost savings and to implement appropriate strategies. By leveraging the strengths of each cloud provider, organizations can achieve significant cost reductions.
Strategies for Optimizing Multi-Cloud Costs
Understanding the diverse pricing structures of various cloud providers is critical for cost optimization. Different providers may excel in specific areas, such as compute, storage, or networking. Recognizing these nuances allows for the selection of the most economical services for each need.
- Right-sizing Resources: Avoid over-provisioning resources in any cloud environment. Employ tools and methodologies to precisely match resource allocation with actual needs. This proactive approach prevents unnecessary spending on idle capacity.
- Leveraging Spot Instances: Utilize spot instances, which are significantly cheaper than on-demand instances, if the application’s workload can tolerate temporary interruptions. This strategy can lead to substantial savings for workloads with flexible requirements.
- Utilizing Reserved Instances: Commit to specific resources for predictable workloads. Reserved instances offer discounted pricing compared to on-demand instances, providing considerable cost savings in the long run.
- Implementing Cost Management Tools: Utilize cloud-provider-specific cost management tools or third-party solutions. These tools provide detailed cost breakdowns, allowing organizations to pinpoint areas of high expenditure and make informed decisions to optimize resource usage.
Opportunities for Cross-Provider Cost Savings
Identifying opportunities for leveraging cost savings across different providers is essential for maximizing the benefits of a multi-cloud strategy. This often involves migrating workloads to the most cost-effective provider for specific functions.
- Data Migration: Analyze data storage needs and identify the most cost-effective storage solutions across different providers. This might involve migrating data to a provider specializing in cost-effective storage solutions.
- Application Optimization: Evaluate applications and workloads to identify potential cost savings by moving specific components to providers that excel in those areas. This might involve moving database services to a provider specializing in database solutions at a lower cost.
- Shared Services: Implement shared services across different cloud environments to eliminate redundancy and achieve economies of scale. This might involve using a common platform for logging, monitoring, or security tools across all cloud providers.
Cost-Saving Strategies for Multi-Cloud Networking
Multi-cloud networking can present opportunities for cost savings by allowing organizations to choose the best networking services from each provider.
- Optimizing Inter-Cloud Connectivity: Choose the most cost-effective method for inter-cloud communication, considering factors such as bandwidth requirements and data transfer rates. Evaluate different networking options (e.g., VPNs, direct connect) for inter-cloud connectivity.
- Leveraging Cloud-Specific Networking Services: Explore cloud-specific networking services, such as VPN gateways or virtual private networks (VPNs), to optimize network performance and costs.
- Automating Network Management: Automate network management tasks to reduce manual intervention and associated costs. This includes automating scaling, configuration, and monitoring.
Potential Cost Savings Opportunities Table
The following table Artikels potential cost savings opportunities in a multi-cloud networking strategy:
| Opportunity | Description | Potential Savings |
|---|---|---|
| Right-sizing Resources | Optimizing resource allocation to match actual needs. | 10-30% |
| Leveraging Spot Instances | Utilizing spot instances for flexible workloads. | 20-50% |
| Data Migration | Migrating data to the most cost-effective provider. | 5-20% |
| Application Optimization | Moving specific application components to cost-effective providers. | 10-25% |
| Shared Services | Implementing shared services across providers. | 5-15% |
Implementation and Maintenance
Implementing a robust multi-cloud networking strategy requires careful planning and execution. This involves a phased approach, starting with pilot deployments in specific environments before scaling to production. Careful consideration of potential roadblocks and contingency plans is crucial for a smooth transition.Successfully managing a multi-cloud network demands ongoing vigilance and adaptability. Regular monitoring, proactive maintenance, and continuous optimization are vital for maintaining performance, security, and cost-effectiveness.
Addressing issues swiftly and efficiently prevents cascading failures and ensures business continuity.
Step-by-Step Implementation Guide
This phased approach facilitates a controlled migration and minimizes disruption. Begin with a pilot project in a non-production environment to test the chosen networking architecture, inter-cloud connectivity, and resource management tools. Monitor performance metrics and security protocols rigorously during the pilot phase. Gradually expand the deployment to other environments as validated and refined. Crucially, involve stakeholders across the organization for alignment and buy-in throughout the process.
Ongoing Maintenance and Management
Maintaining a multi-cloud network necessitates a structured approach to monitoring, troubleshooting, and adapting to evolving needs. This involves establishing clear communication channels between teams responsible for different cloud environments. Regularly assess performance metrics, security configurations, and resource utilization to identify potential bottlenecks or vulnerabilities. Continuous optimization of the network topology and resource allocation is vital to maximize efficiency and minimize costs.
Best Practices for Maintaining a Multi-Cloud Network
Implementing standardized operational procedures (SOPs) across all cloud environments is essential. This ensures consistency in maintenance activities and minimizes errors. Employ automated tools for routine tasks like monitoring and patching to reduce manual intervention and increase efficiency. Regularly review and update security configurations to mitigate potential threats. Establish clear incident response protocols to ensure rapid and effective resolution of issues.
Maintenance Task Frequency Table
| Maintenance Task | Frequency | Description |
|---|---|---|
| Security Audits | Monthly | Comprehensive review of security configurations and policies across all cloud environments. |
| Performance Monitoring | Daily | Tracking key performance indicators (KPIs) such as latency, bandwidth utilization, and resource availability. |
| Network Configuration Updates | Quarterly | Review and update network configurations to address evolving requirements and vulnerabilities. |
| Resource Optimization | Semi-annually | Assess resource utilization and identify opportunities for optimization, including right-sizing virtual machines and optimizing storage configurations. |
| Inter-cloud Connectivity Testing | Weekly | Verify the reliability and performance of inter-cloud connections. |
Last Point
In conclusion, designing a multi-cloud networking strategy requires careful planning, meticulous consideration of security protocols, and a deep understanding of the unique characteristics of each cloud provider. This guide has provided a structured approach to developing a robust, secure, and cost-effective multi-cloud networking architecture. By understanding the interconnectedness of various components, businesses can effectively navigate the complexities and reap the benefits of this increasingly popular approach.
Clarifying Questions
What are the key factors to consider when choosing cloud providers for a multi-cloud setup?
Interoperability, networking capabilities (e.g., VPC, VPN, load balancers), security features, and pricing models are crucial considerations. Evaluating the providers’ ability to seamlessly integrate with each other is paramount.
What are some common security risks in a multi-cloud environment, and how can they be mitigated?
Potential risks include misconfigurations, lack of centralized security policies, and inadequate monitoring. Mitigation strategies include employing robust security tools, implementing consistent security policies across providers, and establishing proactive monitoring and response procedures.
How can I optimize costs in a multi-cloud environment?
Cost optimization involves evaluating pricing models, leveraging cost savings opportunities across providers, and using tools for resource optimization and usage monitoring.
What tools can help with managing resources across multiple cloud providers?
Centralized resource management tools, specifically designed for multi-cloud environments, help consolidate and simplify resource management across various cloud platforms. These tools provide a unified view of resources and facilitate efficient allocation and control.