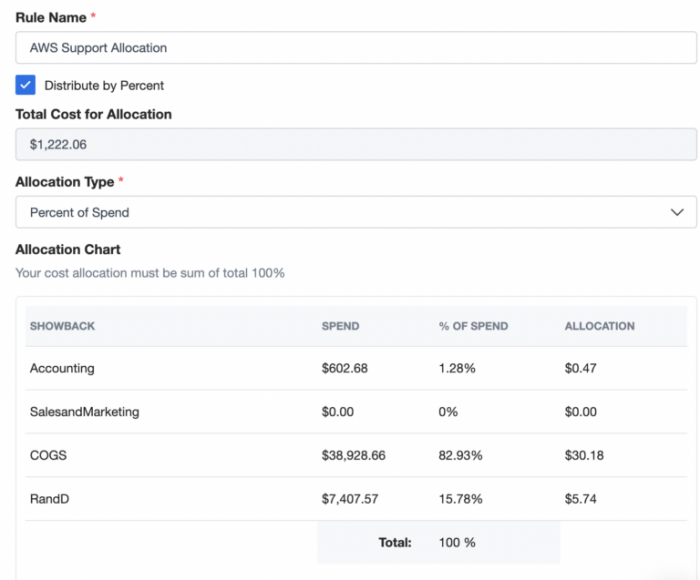
Smooth Transition: From Showback to Chargeback for Efficient IT Cost Management
Transitioning from showback to chargeback can significantly improve cost transparency and accountability within your organization. This article provid...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

Transitioning from showback to chargeback can significantly improve cost transparency and accountability within your organization. This article provid...

This article delves into the critical topic of leader election in distributed systems, exploring various algorithms, from centralized to decentralized...

This comprehensive guide dives deep into the financial landscape of serverless computing, exploring initial infrastructure costs, operational expendit...

This comprehensive guide delves into the essential practices of effective code reviews, highlighting their crucial role in enhancing software quality...
Designing a successful cloud architecture requires a strategic approach that aligns business goals with technical needs and cloud provider capabilitie...

This comprehensive guide dives into the world of Jenkinsfiles, exploring their crucial role in automating Continuous Integration and Continuous Delive...

Cloud sustainability is a critical topic, examining the intersection of environmental responsibility and financial efficiency in cloud computing. Busi...

In the ever-evolving digital world, File Integrity Monitoring (FIM) serves as a crucial security layer, vigilantly protecting your data and systems fr...
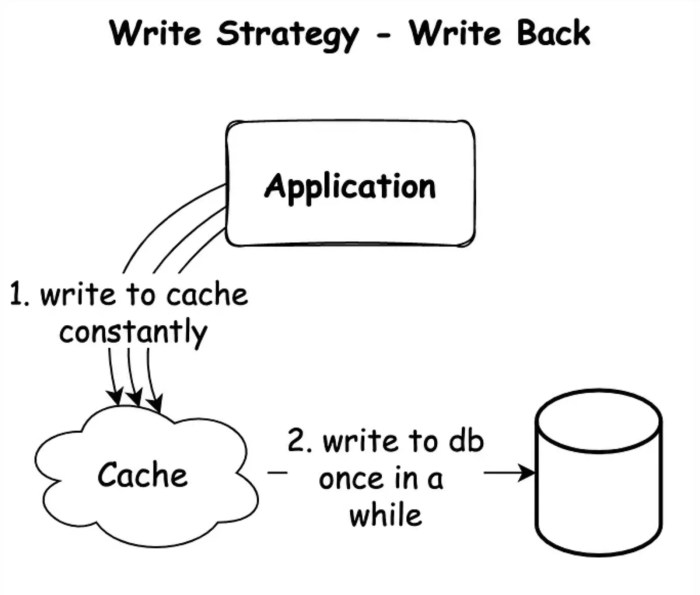
This article delves into the critical distinctions between write-through and write-back caching, two fundamental strategies for optimizing data access...
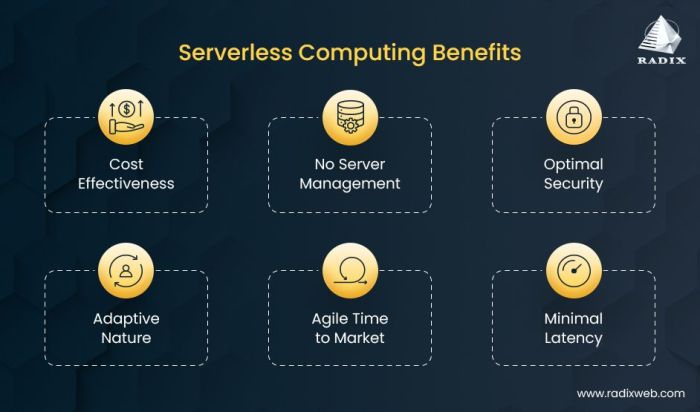
This comprehensive guide explores the significant advantages of migrating to a serverless architecture, detailing how it can revolutionize your infras...

This article provides a comprehensive guide to serverless cron jobs, exploring their core concepts, architectural components, and triggering mechanism...

This comprehensive guide delves into the critical practice of container vulnerability scanning, explaining its core concepts and importance in securin...