Web Application Firewall (WAF): Protecting Your Apps from Cyber Threats
In the face of escalating cyber threats, protecting web applications is more critical than ever. This article delves into the essential function of We...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology
In the face of escalating cyber threats, protecting web applications is more critical than ever. This article delves into the essential function of We...

Navigating the complexities of cloud compliance is critical for modern businesses. This guide provides a comprehensive overview of designing a robust...
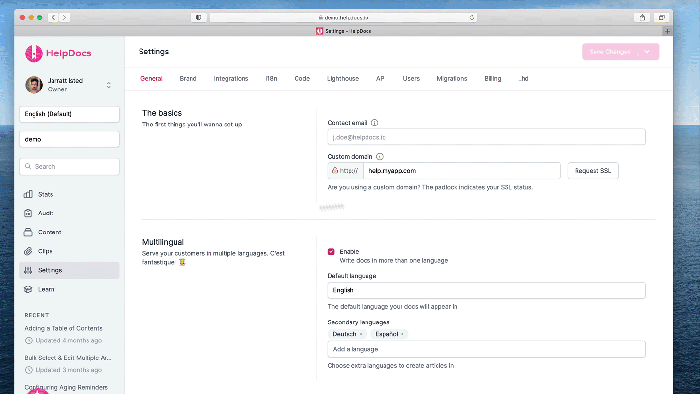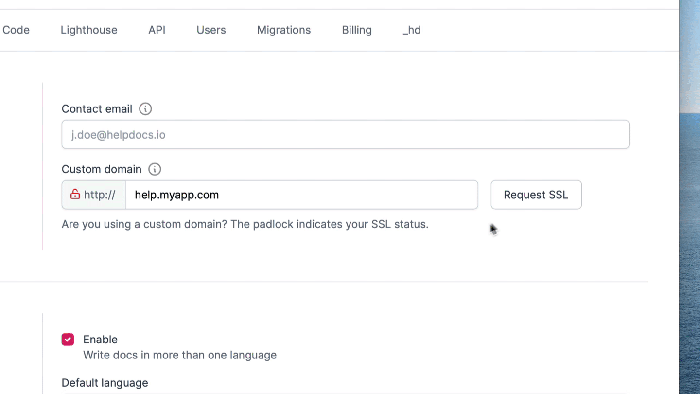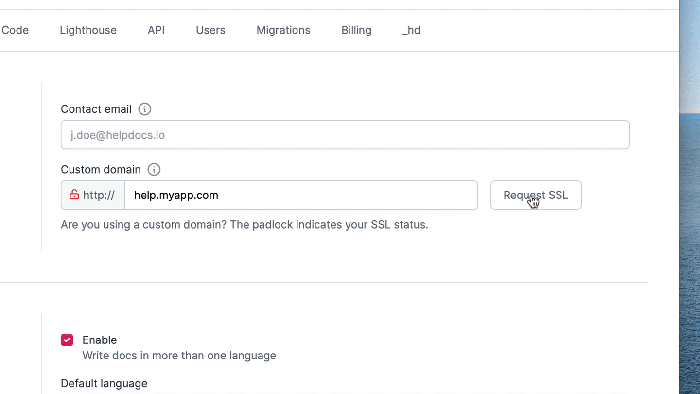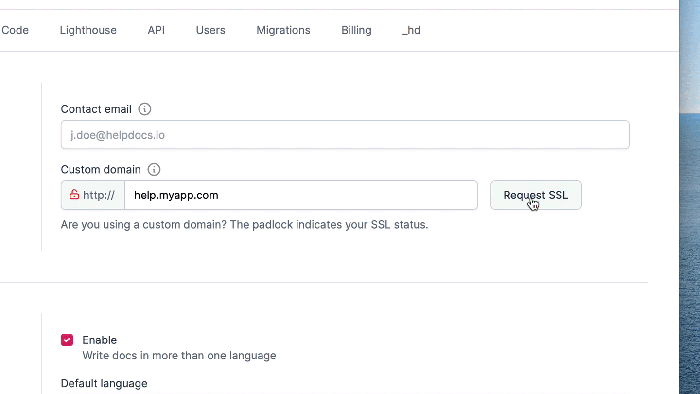
Custom domains are essential for professionalizing your serverless APIs, offering branding, a better user experience, and improved security compared t...
Choosing between SQL and NoSQL databases is a critical decision for any application. This comprehensive guide provides a thorough comparison, analyzin...
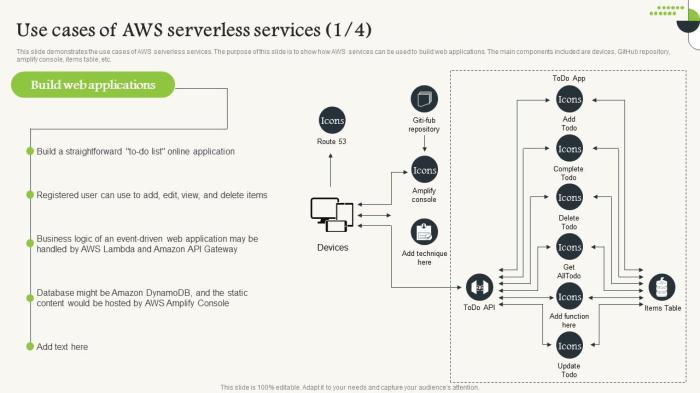
The serverless-first development approach is revolutionizing software architecture by making serverless computing the cornerstone of application desig...
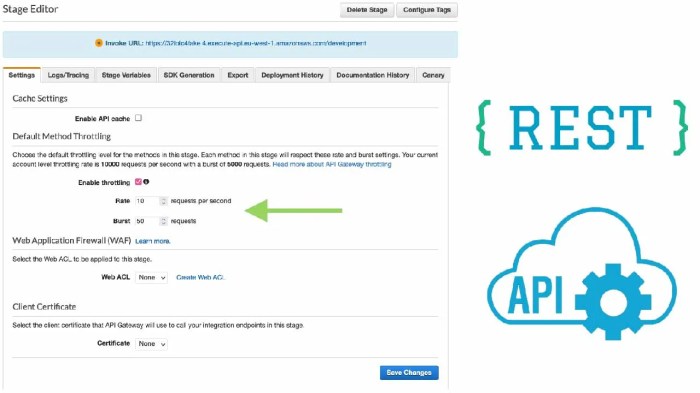
This article provides a comprehensive overview of throttling in serverless APIs, exploring its fundamental concepts, various implementation mechanisms...
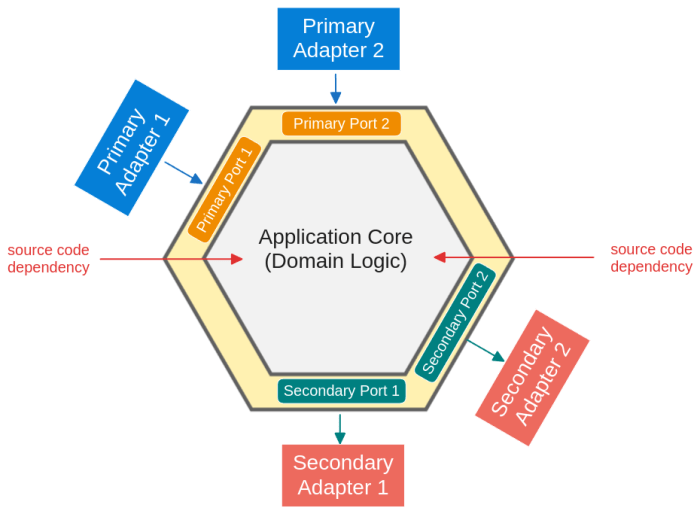
This article explores the significant benefits of testability within the Hexagonal Architecture, demonstrating how it reduces development time and cos...
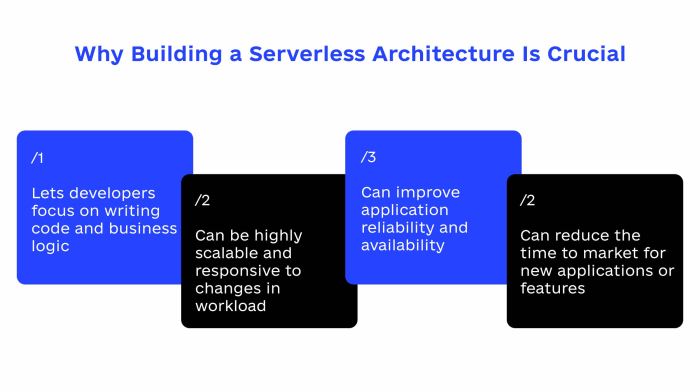
This article explores the critical role of Infrastructure as Code (IaC) in effectively managing serverless environments. It provides a comprehensive g...
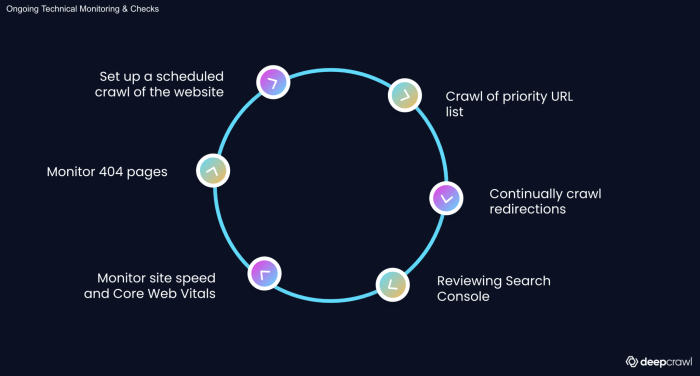
Ensuring a smooth transition after a migration requires robust post-migration monitoring to identify and address potential issues. This article delves...
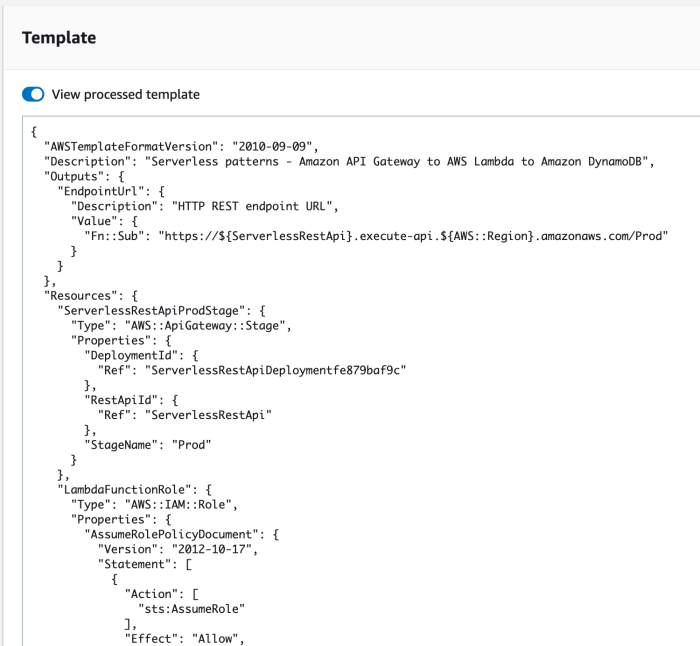
This comprehensive guide provides a deep dive into defining various serverless resources within AWS SAM templates, a crucial skill for modern serverle...
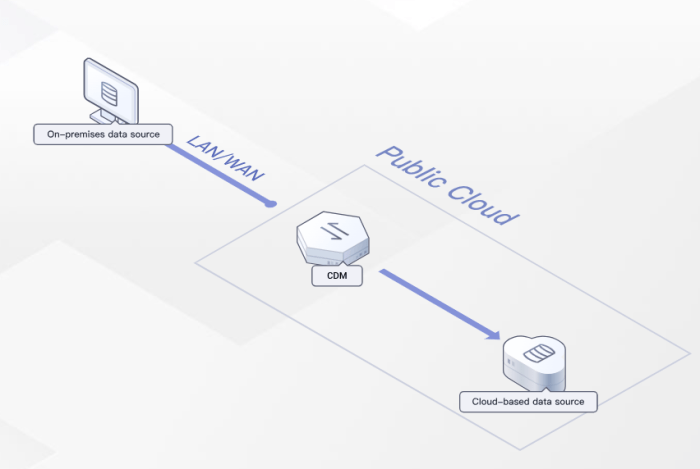
Navigating the complexities of cloud data migration requires a strategic approach, and this article provides a comprehensive guide to help you make in...
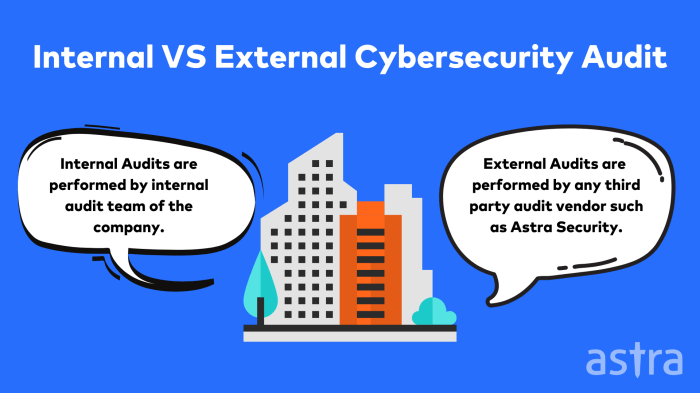
Navigating a cloud security audit can seem daunting, but this comprehensive guide provides a clear roadmap for preparation and success. The article me...