
Kubernetes Pod Security Policies: Understanding and Implementing Best Practices
Kubernetes Pod Security Policies (PSPs) are crucial for bolstering the security of your containerized applications within a Kubernetes cluster. These...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

Kubernetes Pod Security Policies (PSPs) are crucial for bolstering the security of your containerized applications within a Kubernetes cluster. These...

This article provides a comprehensive overview of Content Delivery Networks (CDNs), explaining their architecture, functionality, and crucial role in...

Effectively communicating a migration plan to stakeholders is crucial for its success. This article provides a comprehensive guide to crafting a robus...

This article delves into the transformative impact of Artificial Intelligence (AI) and Machine Learning (ML) on cloud architecture, exploring their in...
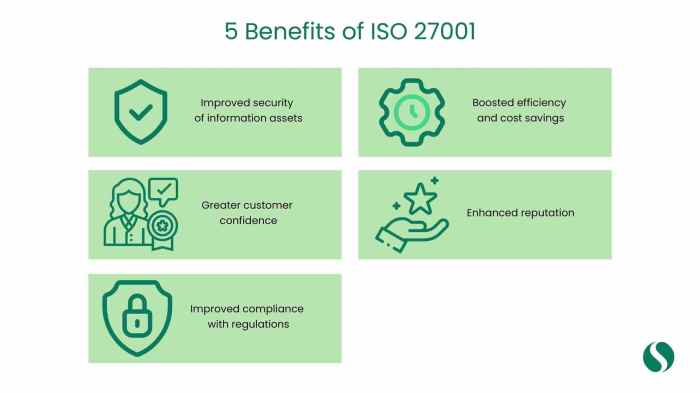
This comprehensive guide provides a detailed roadmap for achieving ISO 27001 certification, covering everything from understanding the core principles...
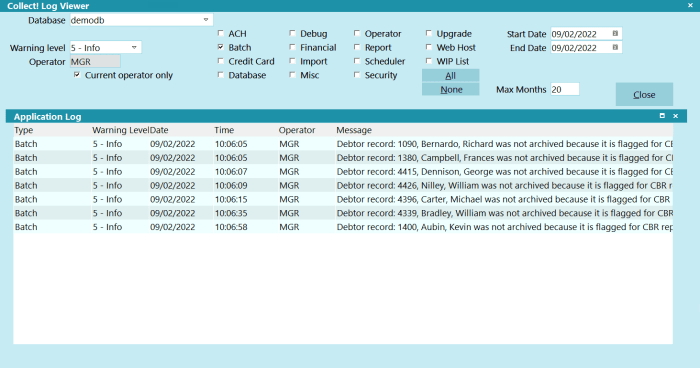
Retiring applications doesn't mean losing valuable data. This article outlines a systematic approach to data archival for retired applications, focusi...
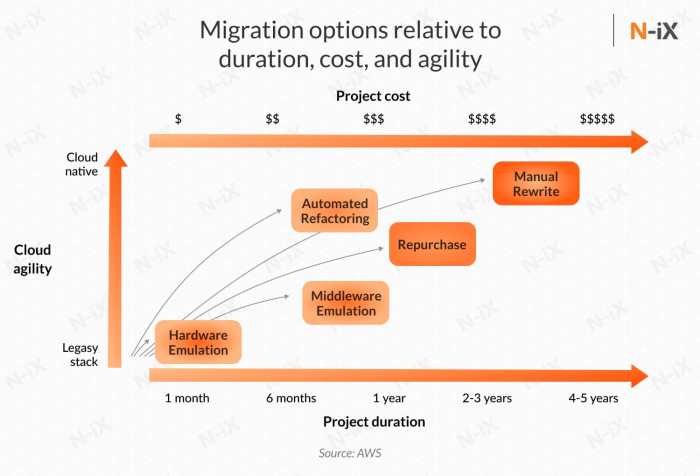
Cloud migration offers substantial benefits, but migrating all applications at once is rarely feasible. This necessitates a strategic approach to prio...

Moving to cloud computing requires a significant investment in employee training to bridge the skills gap created by this evolving technology landscap...

This comprehensive guide provides a roadmap for building a robust Security Operations Center (SOC) specifically designed for the cloud environment. Fr...
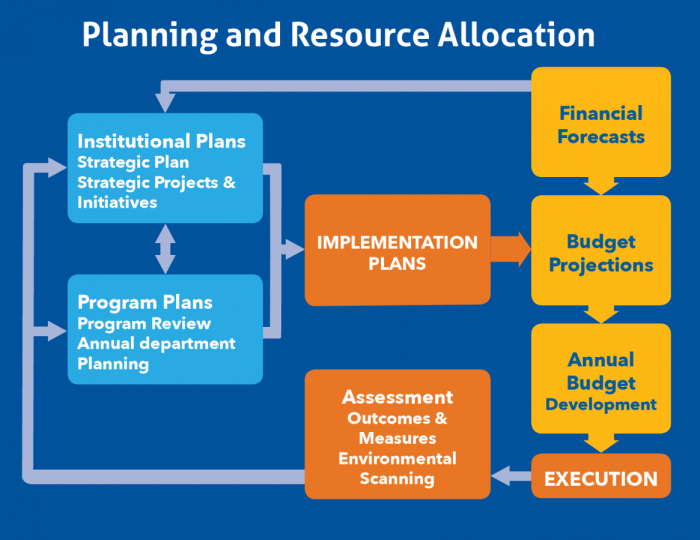
Serverless data analytics is revolutionizing data processing through scalable, cost-effective, and agile solutions. This paradigm shift requires strat...
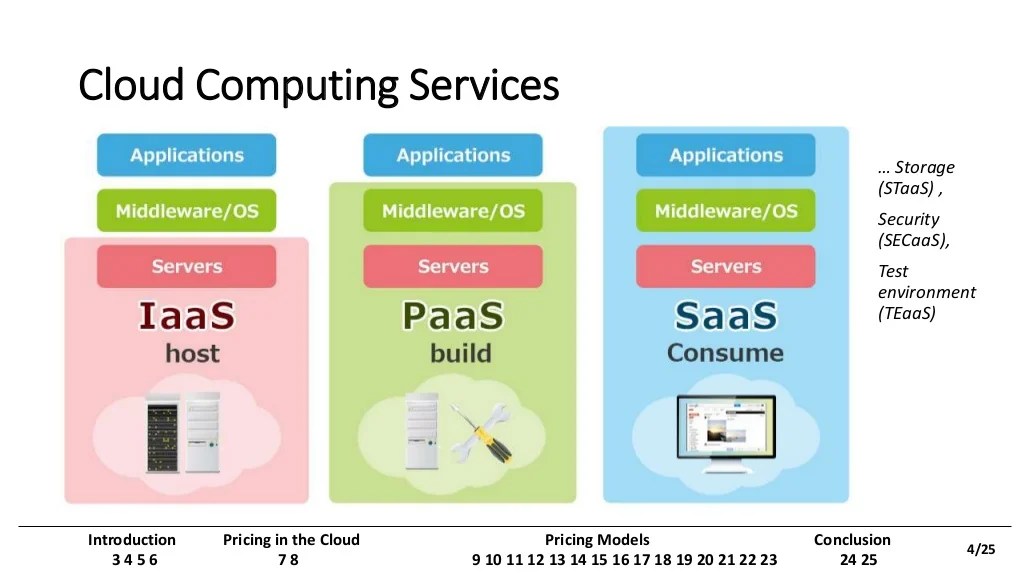
Understanding internal cloud service costs is crucial for efficient resource management. A rate card functions as a price list for your internal cloud...
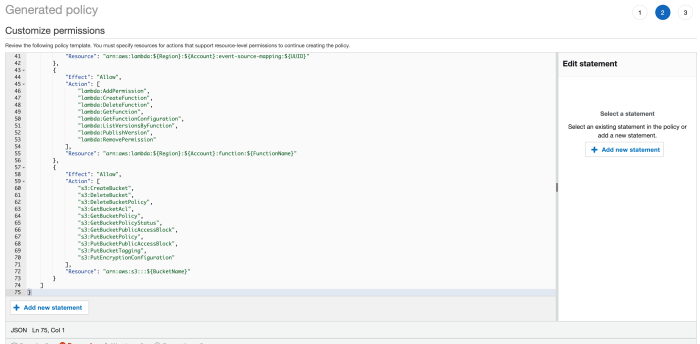
This comprehensive guide provides a deep dive into serverless security, covering critical aspects from authentication and authorization to incident re...