
The Chief Information Security Officer (CISO): Roles, Responsibilities, and Impact
In today's digital world, the Chief Information Security Officer (CISO) is a vital strategic leader, tasked with protecting an organization's data and...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

In today's digital world, the Chief Information Security Officer (CISO) is a vital strategic leader, tasked with protecting an organization's data and...

Migrating from a monolithic architecture to microservices offers significant advantages in scalability and agility. This guide provides a structured f...
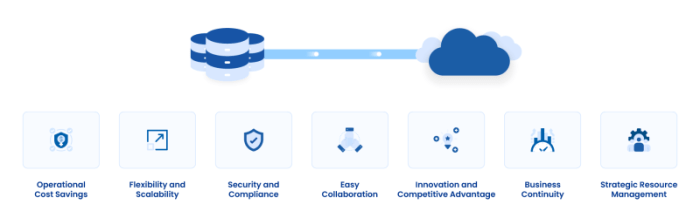
Moving from on-premise infrastructure to the cloud requires a strategic and well-planned approach to ensure a smooth transition. This article provides...

This article provides a comprehensive guide to reviewing and refining your FinOps practices to maximize cloud spending efficiency. It emphasizes the i...
This article provides a comprehensive overview of endpoint security specifically tailored for cloud workloads, outlining its core concepts, essential...
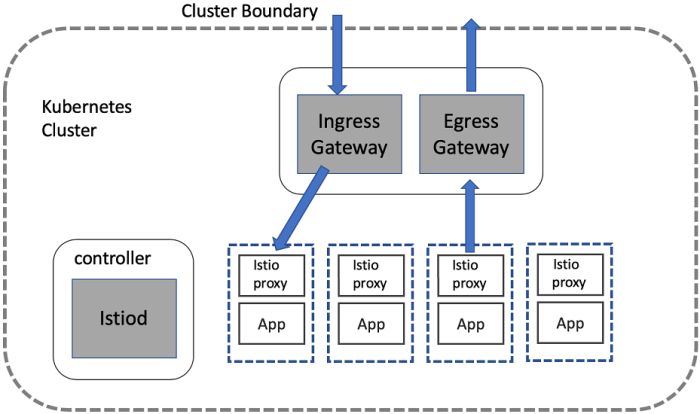
Gated egress and ingress security patterns are fundamental to robust network security. These patterns govern the flow of traffic entering and leaving...

This article provides a comprehensive overview of User and Entity Behavior Analytics (UEBA), exploring its core concepts, components, and practical ap...
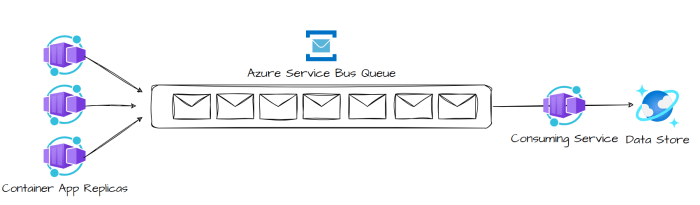
The queue-based load leveling pattern offers a robust solution for handling variable workloads, promoting consistent performance, and maximizing resou...

Creating a compelling business case is essential for successful cloud migration projects. This strategic shift requires articulating the value proposi...
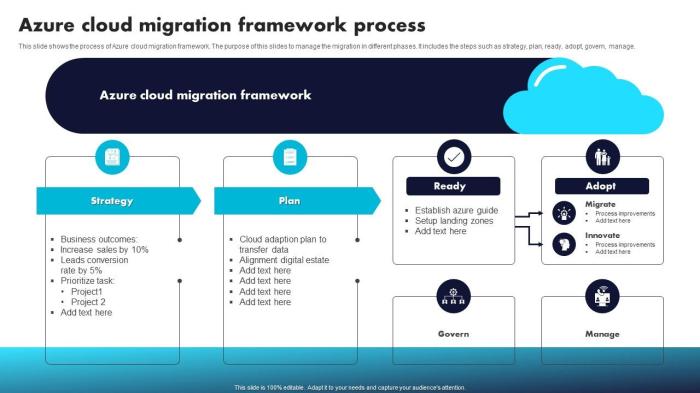
Successfully navigating a cloud migration requires a robust cloud governance framework to mitigate risks and ensure compliance. This comprehensive gui...
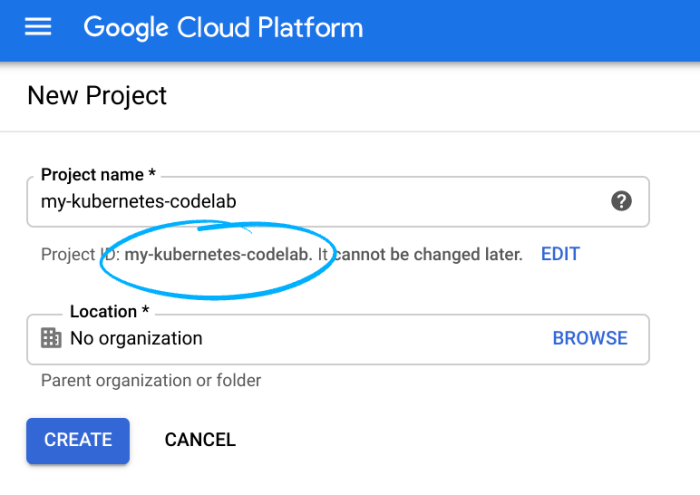
A multi-region failover strategy is a vital architectural approach for maintaining uninterrupted operation and data availability, especially during re...
This article offers a comprehensive guide to negotiating robust security provisions within your cloud service level agreement (SLA). It covers critica...