
Serverless Vendor Lock-In: Challenges and Mitigation Strategies
Serverless computing offers significant benefits, but it also introduces the critical challenge of vendor lock-in, which can severely impact portabili...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

Serverless computing offers significant benefits, but it also introduces the critical challenge of vendor lock-in, which can severely impact portabili...
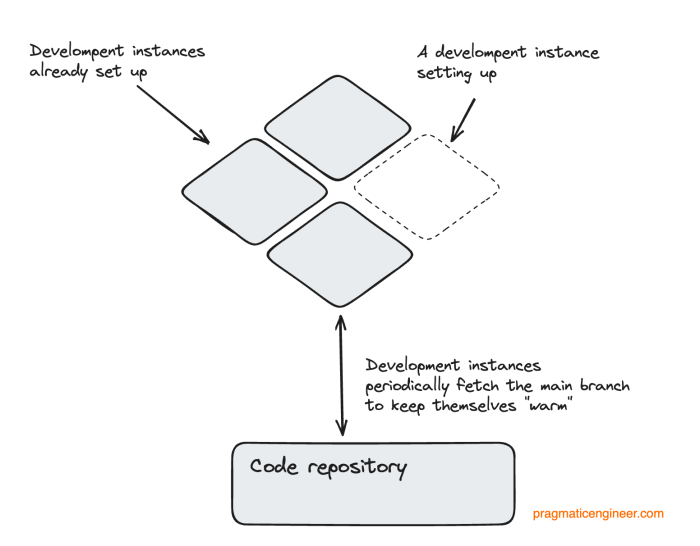
This guide offers a comprehensive overview of achieving crucial dev/prod parity in cloud environments, a critical practice for modern cloud operations...
Software supply chain security is crucial in today's digital world, safeguarding every phase of software development from planning to deployment. This...
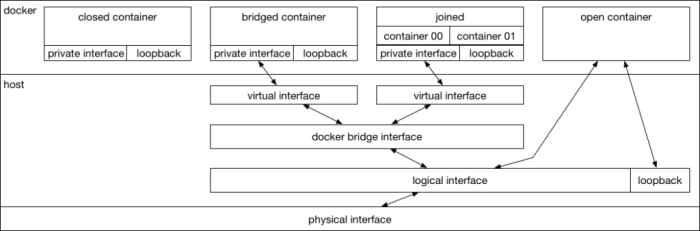
This comprehensive guide demystifies Docker networking, providing a deep dive into its fundamental concepts, network drivers, and advanced configurati...

This article provides a comprehensive guide to Tactics, Techniques, and Procedures (TTPs), crucial elements for understanding and combating cyber thre...
This article dissects the "Boiling the Ocean" anti-pattern, a common pitfall in project management where overly ambitious scopes lead to project failu...
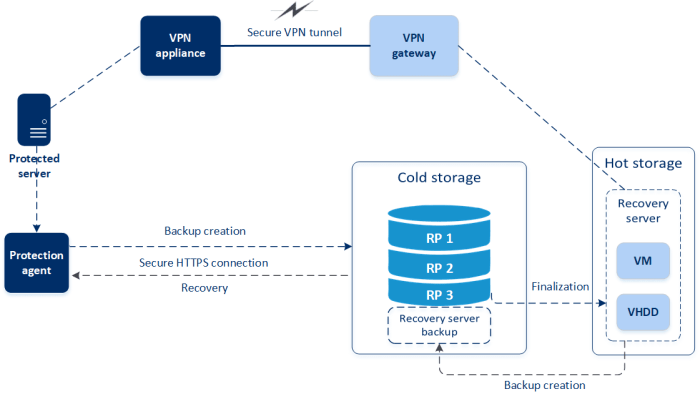
Ensuring the reliability of your systems post-migration necessitates rigorous testing of failover and redundancy mechanisms. This article provides a c...

Unused cloud resources silently drain budgets and can create security vulnerabilities, making their identification and termination crucial for optimal...

Application portfolio analysis is a vital, yet often overlooked, step in digital transformation, providing a data-driven understanding of an organizat...

This comprehensive article explores the critical practice of cloud cost anomaly detection, providing a detailed overview of its definition, benefits,...

This comprehensive guide delves into the Observer Pattern, a crucial design pattern for building flexible and maintainable systems. The article provid...

Organizations leveraging multi-cloud environments face a complex landscape of security risks, including data breaches, identity and access management...