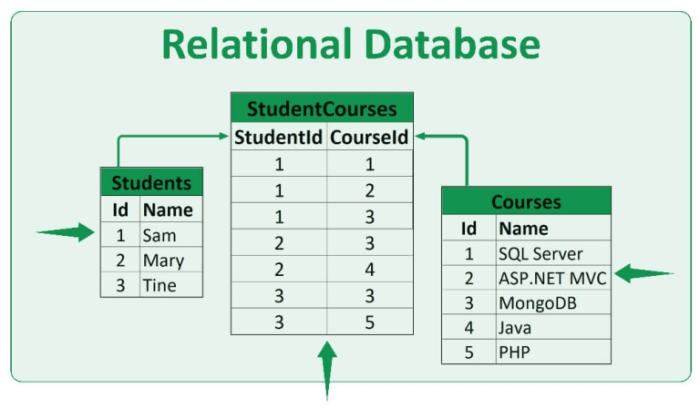
Database Sharding: A Comprehensive Guide to Scalability and Performance
This comprehensive article delves into the critical database architecture technique of sharding, exploring its benefits, challenges, and various imple...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

This comprehensive article delves into the critical database architecture technique of sharding, exploring its benefits, challenges, and various imple...
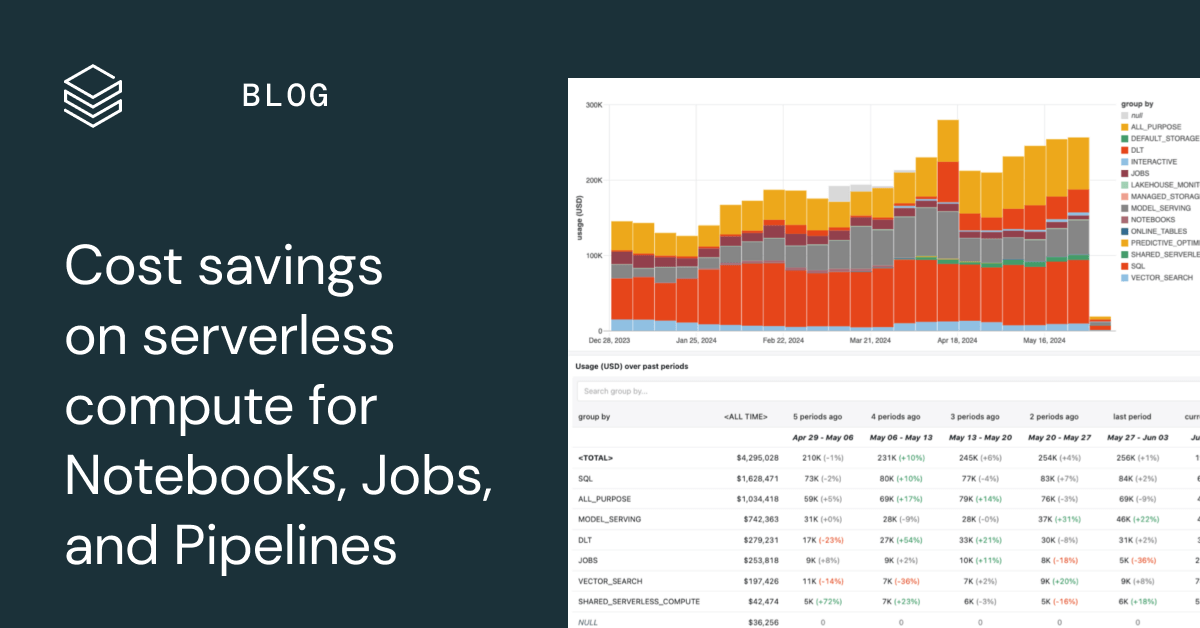
This comprehensive guide delves into the critical aspects of forecasting and managing serverless costs, providing actionable strategies for optimizing...
This article provides a comprehensive guide to implementing CIS Benchmarks for cloud hardening, covering crucial aspects from understanding the benchm...
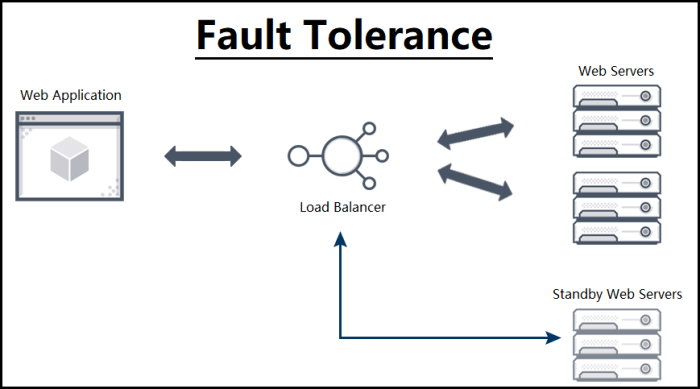
This guide provides a comprehensive overview of designing for fault tolerance in cloud environments, a critical aspect often overlooked in modern appl...

This article provides a comprehensive analysis of proactive versus reactive security strategies, detailing their core principles, advantages, and limi...

This article provides a comprehensive guide to developing and implementing a successful cloud adoption strategy, outlining its core components, benefi...

Discover insights and practical tips in this comprehensive guide about What Are The Compliance Requirements For Data Breach Notifications.
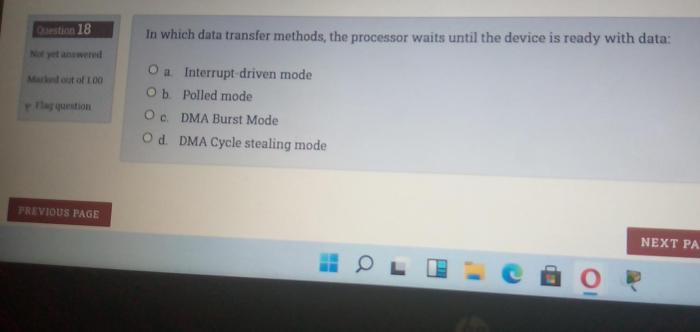
Migrating stateful applications requires careful consideration due to their persistent data and session information, which differentiates them from st...
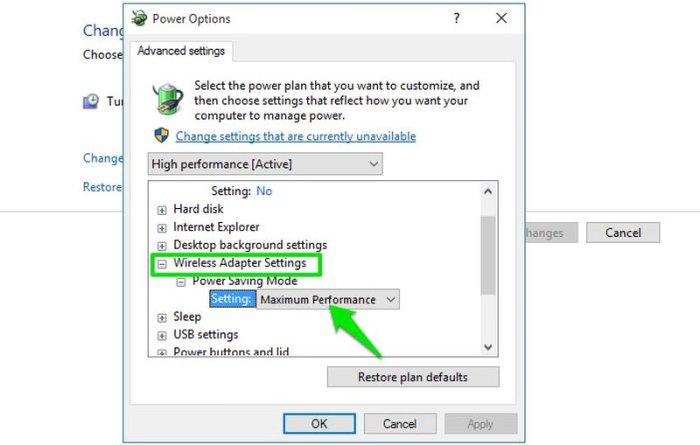
Migrating your application can introduce performance challenges. This comprehensive guide provides a strategic approach to proactively address and res...
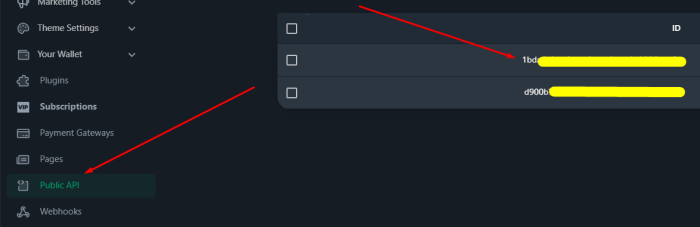
Protecting sensitive API keys and tokens is crucial for maintaining application security and preventing costly data breaches. This article provides a...

This article provides a comprehensive overview of security maturity models, essential frameworks for enhancing an organization's cybersecurity posture...
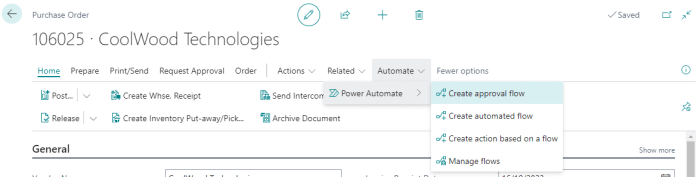
This article delves into the critical process of automating database schema migrations, exploring the benefits of automation and the challenges of man...