
What Is Data Masking And Tokenization
Data masking and tokenization are essential security practices for safeguarding sensitive data while maintaining its usability. This article delves in...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

Data masking and tokenization are essential security practices for safeguarding sensitive data while maintaining its usability. This article delves in...
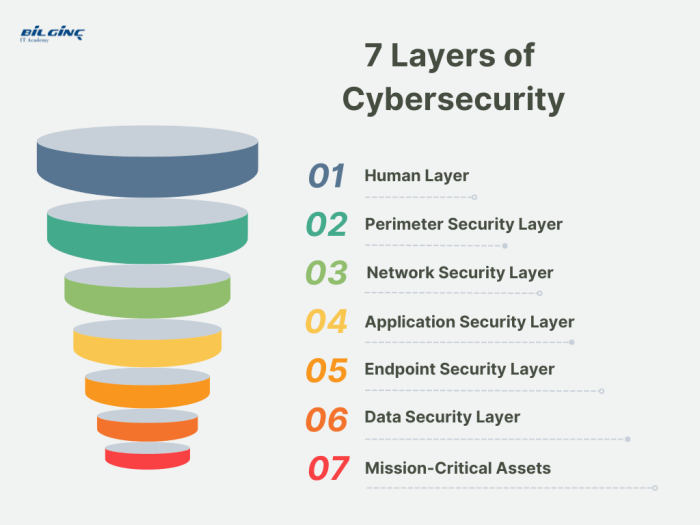
Defense in depth is a critical cybersecurity principle that emphasizes a layered approach to security, acknowledging that no single measure is impenet...
This article provides a comprehensive overview of serverless Step Functions, detailing their core components, benefits, and practical applications in...
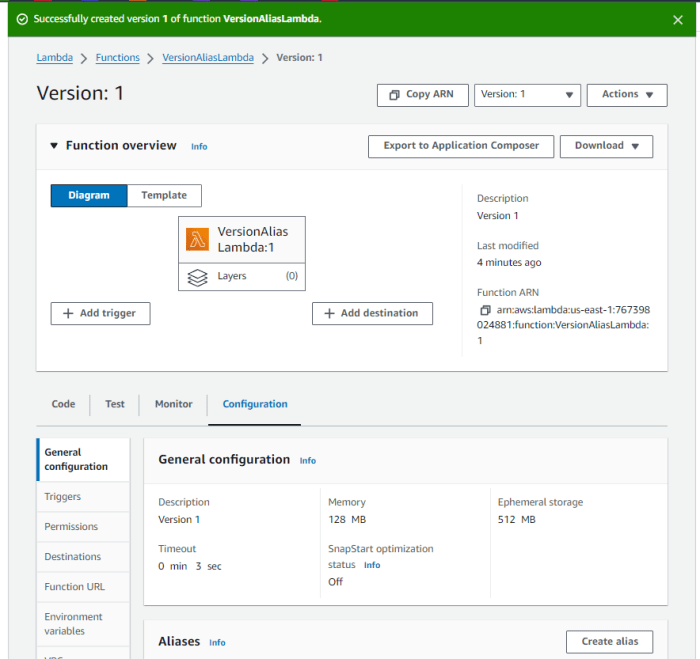
This comprehensive guide delves into the critical concepts of Lambda function versions and aliases, explaining their distinct roles in managing and de...
This comprehensive guide provides a detailed exploration of techniques to significantly reduce Docker image sizes, covering strategies from image buil...

Cloud commitment-based discounts provide substantial cost savings on cloud services, offering a significant advantage over on-demand pricing. This art...
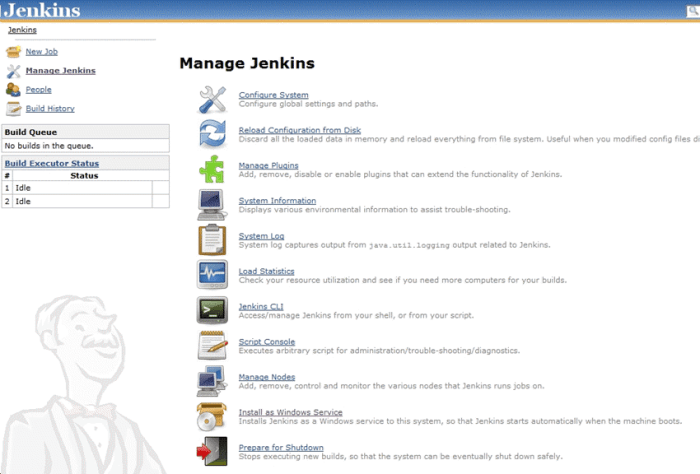
This article provides a comprehensive introduction to Jenkins and its critical role in Continuous Integration (CI) for software development. Learn how...

This article provides a comprehensive overview of the roles and responsibilities within a Security Operations Center (SOC), crucial for modern cyberse...
This comprehensive guide delves into the critical aspects of secure logging and monitoring within cloud environments, exploring its fundamental concep...

To thrive in a competitive environment, engineering teams must prioritize cost-aware decision-making. This guide provides a comprehensive overview of...
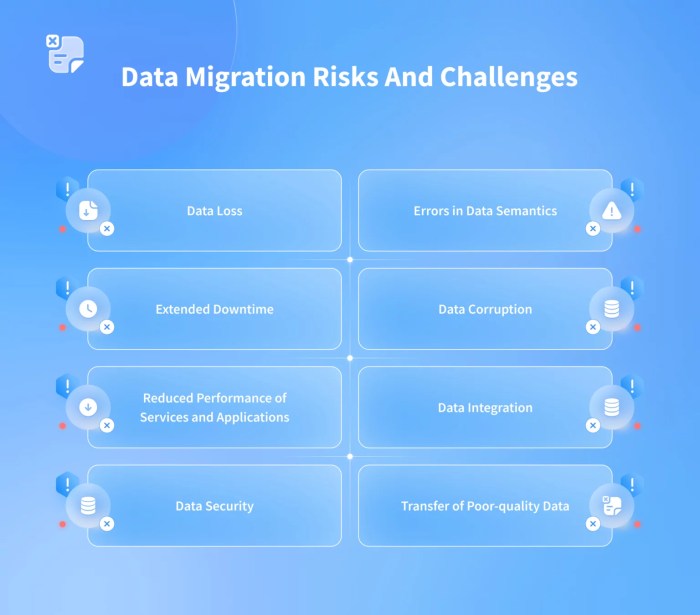
Data migration, the process of moving data across different systems, introduces significant security challenges that must be addressed. This article e...
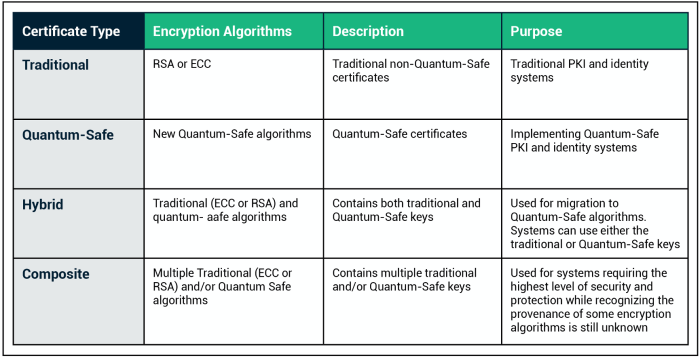
Explore the groundbreaking field of quantum cryptography and its revolutionary impact on cybersecurity in this comprehensive article. From fundamental...