Data Tokenization: A Comprehensive Guide to Enhanced Security
This comprehensive article delves into the critical role of tokenization in modern data security, exploring its core concepts, operational mechanisms,...
152 posts in this category

This comprehensive article delves into the critical role of tokenization in modern data security, exploring its core concepts, operational mechanisms,...
This comprehensive article delves into the transformative technology of homomorphic encryption, exploring its core functionality, diverse types, and u...

This comprehensive guide provides a roadmap for building a robust Security Operations Center (SOC) specifically designed for the cloud environment. Fr...

This article provides a comprehensive overview of cloud-native security services, exploring their core concepts, key components, and numerous benefits...

This article delves into the intricacies of legal hold and eDiscovery, focusing on the significant advantages of leveraging cloud technology for these...
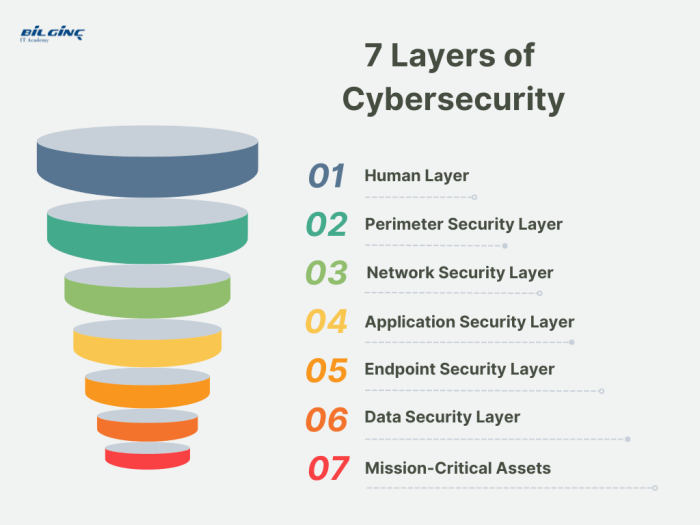
Defense in depth is a critical cybersecurity principle that emphasizes a layered approach to security, acknowledging that no single measure is impenet...
Artificial intelligence is rapidly transforming the cybersecurity landscape, offering powerful new tools for threat detection, incident response, and...

In today's evolving digital landscape, cloud security certifications are crucial for professionals seeking to validate their expertise and advance the...

This article delves into the critical practice of Continuous Compliance Monitoring (CCM) in cloud environments, explaining its core concepts and showc...

Navigating the complexities of cloud security requires a proactive approach, beginning with a comprehensive incident response plan. This guide highlig...

This article provides a comprehensive overview of runtime security for containers, emphasizing its critical role in protecting containerized applicati...
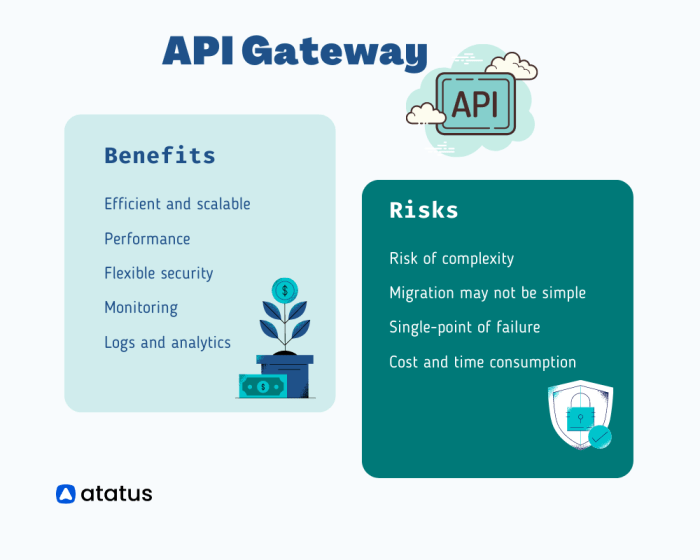
API gateways are vital components of modern application architectures, acting as the primary point of entry and security for all API traffic. Understa...