
Securely Managing Access for Third-Party Contractors: A Comprehensive Guide
Managing third-party contractor access is a crucial element of robust cybersecurity. This guide outlines essential strategies for securely granting ac...
152 posts in this category

Managing third-party contractor access is a crucial element of robust cybersecurity. This guide outlines essential strategies for securely granting ac...
Protecting sensitive data in the cloud requires robust security measures, and this guide provides a comprehensive overview of data encryption. It delv...

Discover how Open Policy Agent (OPA) is transforming policy enforcement in modern software development. This guide explores OPA's capabilities in mana...

This article delves into the critical security challenges inherent in serverless computing, covering everything from authentication and authorization...

This article delves into the critical process of de-provisioning user accounts, explaining its definition, triggers, and the vital role it plays in bo...
Managing security across a multi-cloud environment requires a strategic approach to avoid fragmentation and ensure consistent protection. This guide o...
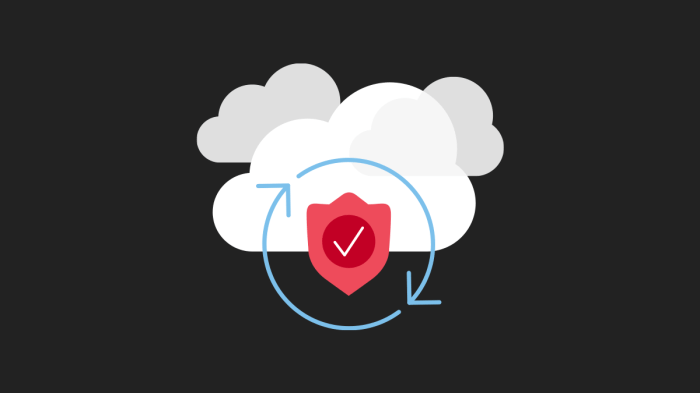
This article delves into the critical concept of Just-in-Time (JIT) access for cloud resources, exploring its core principles and the significant secu...

This comprehensive guide to Cloud Identity and Access Management (IAM) explores core concepts, best practices, and emerging trends to secure your clou...

This article provides an introduction to threat modeling using the STRIDE methodology, a critical practice for enhancing software security. Learn how...
Want to strengthen your organization's digital defenses? This guide offers a comprehensive approach to conducting a security architecture review, prov...

This comprehensive guide explores the critical concepts of data anonymization and pseudonymization, essential practices for protecting sensitive infor...

This article provides a comprehensive overview of Data Privacy Impact Assessments (DPIAs), essential tools for protecting personal information in the...