
SOC 2 Compliance in the Cloud: A Comprehensive Guide
Navigating SOC 2 compliance in a cloud environment requires a strategic approach, and this article provides a comprehensive guide. It covers essential...
152 posts in this category

Navigating SOC 2 compliance in a cloud environment requires a strategic approach, and this article provides a comprehensive guide. It covers essential...

This article provides a comprehensive analysis of proactive versus reactive security strategies, detailing their core principles, advantages, and limi...

In today's digital world, the Chief Information Security Officer (CISO) is a vital strategic leader, tasked with protecting an organization's data and...

Securing your critical digital assets starts with effective Privileged Access Management (PAM). This article provides a comprehensive, practical guide...

This article provides a comprehensive overview of security maturity models, essential frameworks for enhancing an organization's cybersecurity posture...
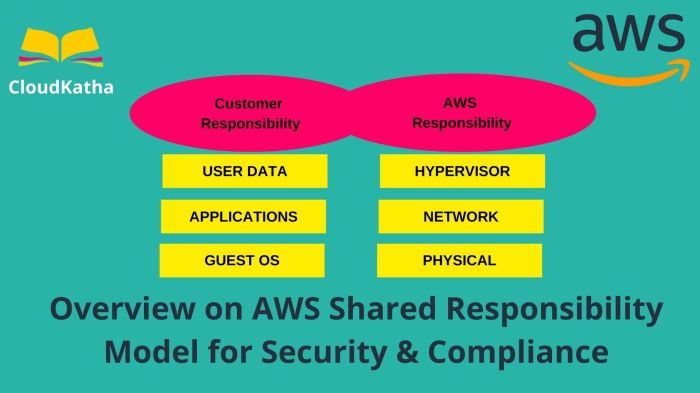
The shared responsibility model is a critical framework in cloud security, outlining the security obligations of both the cloud provider and the custo...

In today's dynamic digital landscape, Cloud Security Posture Management (CSPM) is essential for securing your cloud environments. CSPM offers a compre...

This comprehensive article delves into the emerging field of Confidential Computing, defining its core concepts, key technologies, and significant ben...
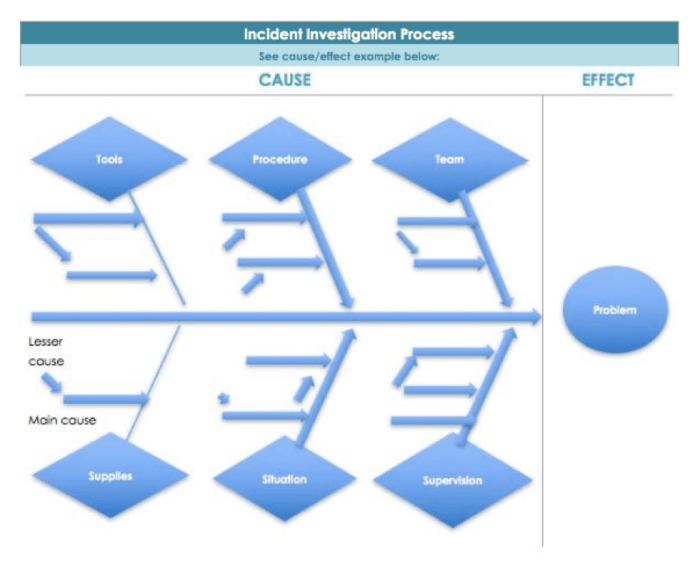
This article provides a comprehensive guide to performing a Root Cause Analysis (RCA) following a security incident, a crucial skill in today's digita...
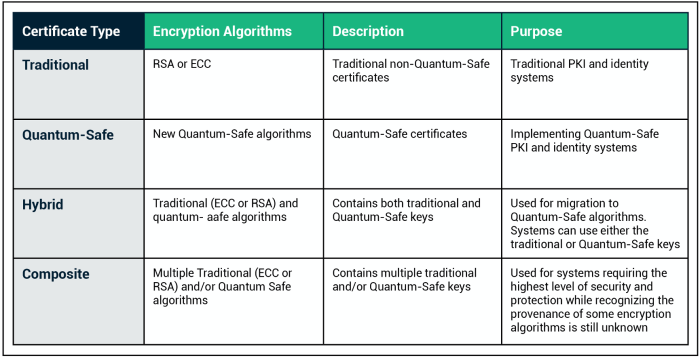
Explore the groundbreaking field of quantum cryptography and its revolutionary impact on cybersecurity in this comprehensive article. From fundamental...
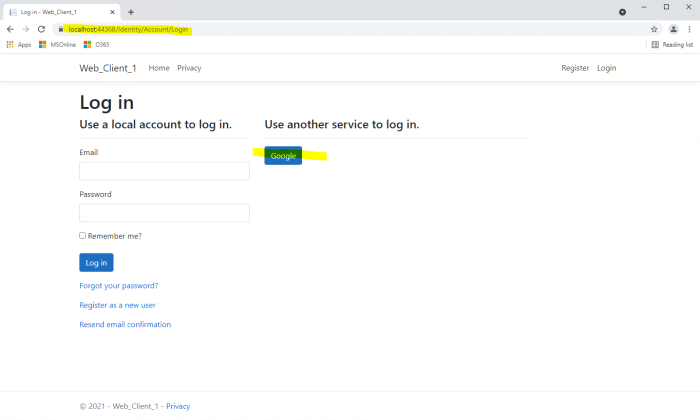
This comprehensive guide delves into the intricacies of OAuth 2.0 and OpenID Connect, explaining their roles in modern authentication and authorizatio...

Navigating HIPAA compliance in the cloud requires a strategic approach that addresses data security, access controls, and disaster recovery. This comp...