
Using the MITRE ATT&CK Framework: A Practical Guide
This comprehensive guide delves into the MITRE ATT&CK framework, providing a roadmap for understanding its structure and leveraging its capabilities t...
152 posts in this category

This comprehensive guide delves into the MITRE ATT&CK framework, providing a roadmap for understanding its structure and leveraging its capabilities t...

The NIST Cybersecurity Framework is a widely adopted, voluntary standard designed to help organizations proactively manage and reduce cybersecurity ri...
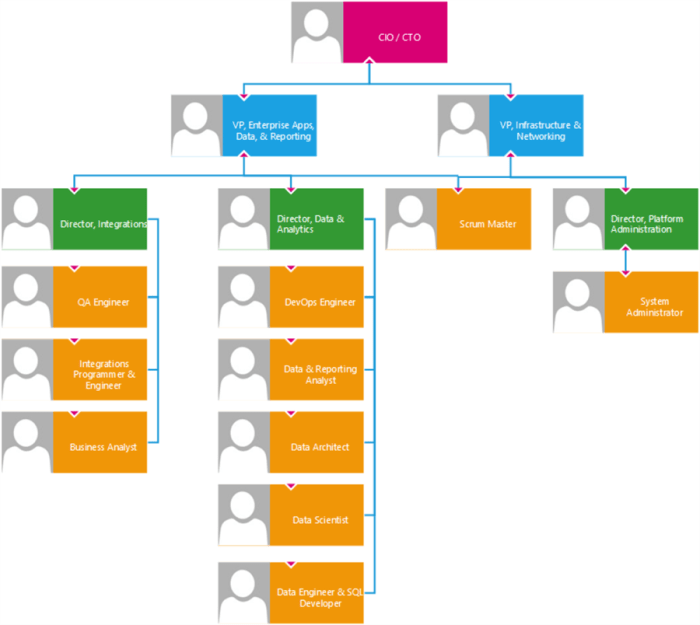
Cloud computing's scalability demands stringent security measures, making clear role and responsibility definitions for cloud access paramount. This a...

Protecting sensitive data within big data platforms demands a comprehensive approach encompassing encryption, access control, data governance, and rob...

Cloud systems demand constant vigilance to ensure both security and optimal performance. This guide outlines essential strategies and best practices f...
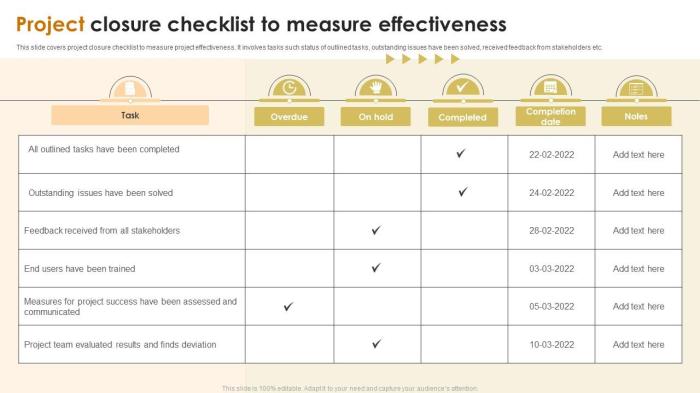
In today's evolving threat landscape, measuring the effectiveness of your security program is paramount. This guide provides a structured approach to...
Protecting your organization from internal cybersecurity risks is paramount. This guide, "How to Detect and Respond to Insider Threats," offers a comp...

Prepare for the future of cybersecurity with a comprehensive guide to Post-Quantum Cryptography (PQC). This article delves into the fundamental concep...
User Lifecycle Management (ULM) and provisioning are crucial for security, operational efficiency, and compliance within any organization. This guide...

In the ever-evolving cloud environment, safeguarding your digital assets is critical, and Cloud Infrastructure Entitlement Management (CIEM) tools off...
This comprehensive article explores the concept of honeypots in cybersecurity, detailing their purpose, diverse types (low, medium, and high-interacti...
The increasing convergence of Internet of Things (IoT) devices and cloud services necessitates a thorough examination of the associated security risks...