SOAR Automation: Streamlining Security Operations for Enhanced Threat Response
Facing an increasingly complex cyber threat landscape, security operations teams need efficient solutions. This article explores how Security Orchestr...
152 posts in this category

Facing an increasingly complex cyber threat landscape, security operations teams need efficient solutions. This article explores how Security Orchestr...
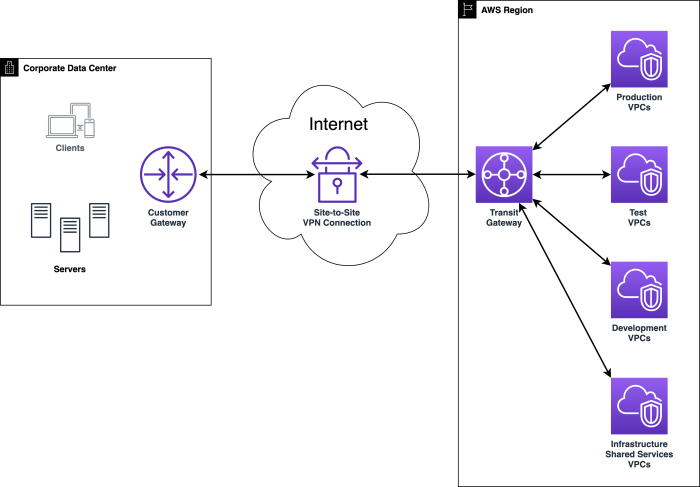
Understand the critical role of Virtual Private Networks (VPNs) in securing modern corporate communications. This article explores the core functional...

Navigate the complex legal landscape of cloud computing with this comprehensive guide. This article delves into critical areas like data privacy regul...
Securing remote access to cloud environments is paramount in today's interconnected landscape, yet presents significant security challenges. This guid...

This guide provides a comprehensive roadmap for establishing robust threat hunting capabilities, essential for proactively identifying and mitigating...
This article explores the vital integration of threat intelligence into cloud security operations, a crucial step in defending against modern cyber th...

In today's digital environment, understanding the financial ramifications of a data breach is essential for any organization. This comprehensive guide...
This article provides a comprehensive overview of Secure Boot processes within virtual machines, detailing its critical role in securing a VM's boot p...

Organizations face increasing cyber threats, making robust security awareness training for employees crucial. This comprehensive guide provides a step...
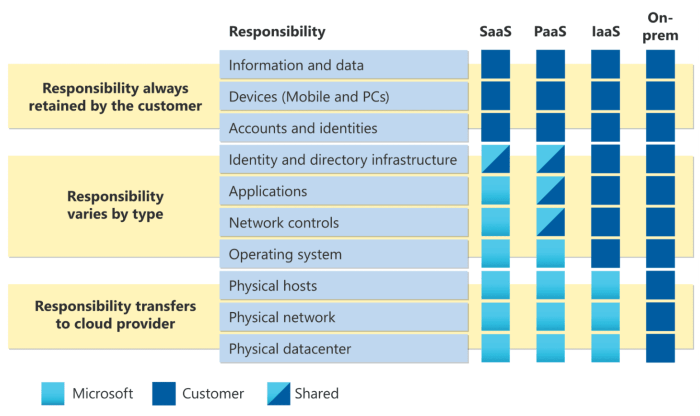
This article explores the critical need to protect "data in use," delving into the inherent security risks and challenges associated with active compu...
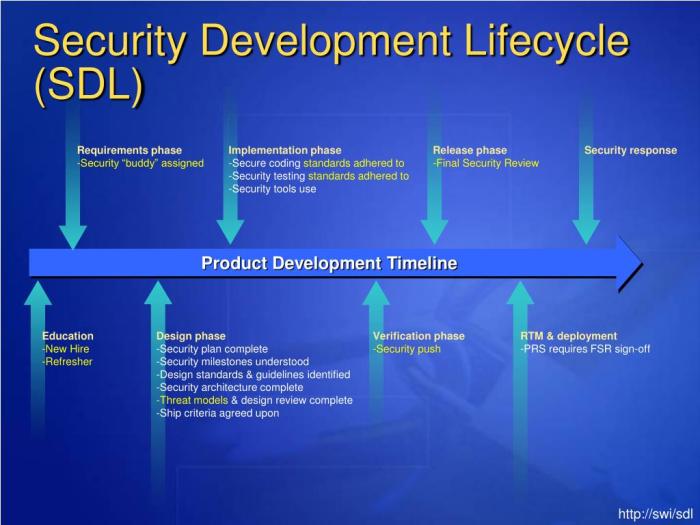
"Shifting security left" is a critical strategy for modern software development, emphasizing the integration of security practices early in the develo...
This comprehensive guide provides a detailed roadmap for implementing Single Sign-On (SSO) across your enterprise applications. From understanding the...