Unit Testing vs. Integration Testing: Key Differences and Best Practices
This comprehensive article meticulously examines the crucial differences between unit testing and integration testing, offering a clear understanding...
167 posts in this category

This comprehensive article meticulously examines the crucial differences between unit testing and integration testing, offering a clear understanding...
Discover insights and practical tips in this comprehensive guide about How To Treat Backing Services As Attached Resources (Factor Iv).
This comprehensive guide provides a practical introduction to using Markdown for creating clear and maintainable technical documentation. From setting...

Feature flags are a powerful technique for modern software development, offering a way to control the release, testing, and deployment of features. Th...

Protecting sensitive data within Kubernetes is crucial for the security of your deployments. This article provides a comprehensive guide to managing s...

This article delves into the critical world of database version control, exploring its core concepts, benefits, and the common challenges encountered....
Navigating the complexities of microservices architecture demands a robust data management strategy. This article delves into crucial approaches for m...

This comprehensive guide delves into the essential practices of effective code reviews, highlighting their crucial role in enhancing software quality...
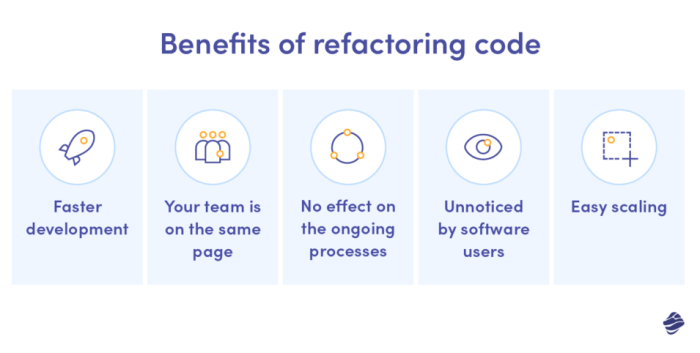
Refactoring code is crucial for long-term software health, allowing developers to improve code structure and maintainability without changing its core...
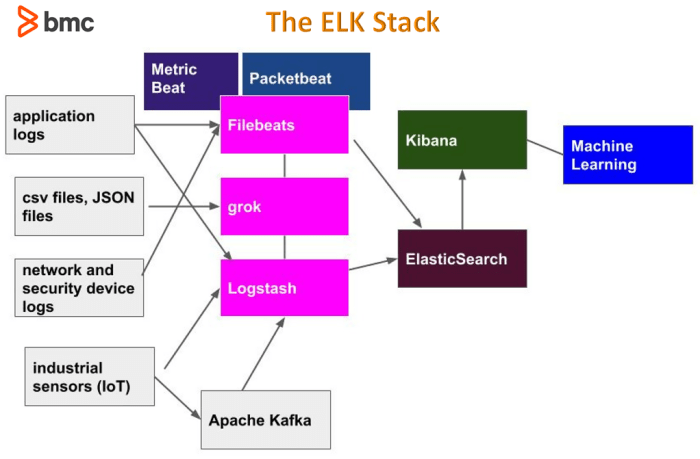
This comprehensive guide explores the ELK Stack (Elasticsearch, Logstash, and Kibana) as a powerful log management solution, covering its core compone...

This article delves into the concept of "code smells," which are subtle indicators of underlying problems within your codebase. Understanding and iden...

This comprehensive guide provides a deep dive into securing container images and registries, covering essential topics from image scanning and vulnera...