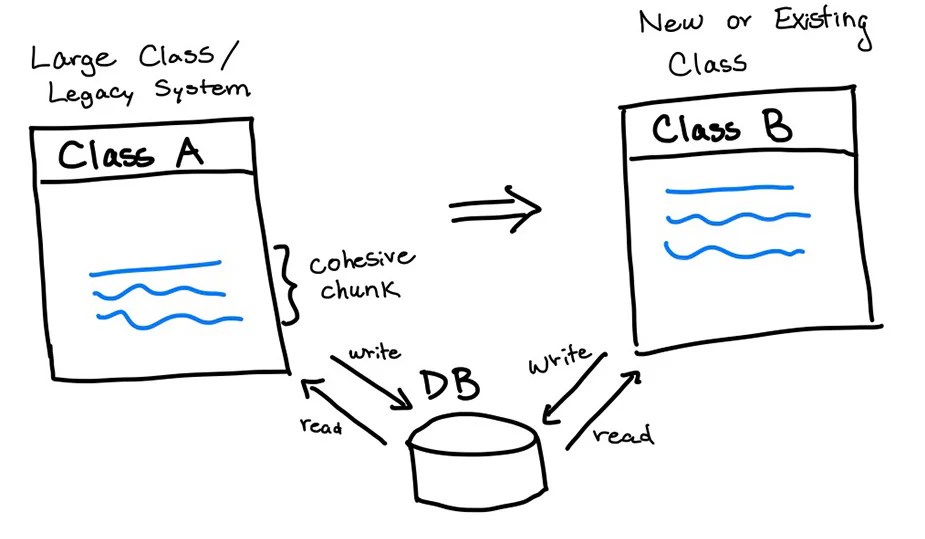
Understanding the Strangler Fig Pattern for Modern Application Modernization
Facing the complexities of application modernization? The Strangler Fig pattern provides a strategic and controlled approach to incrementally update l...
175 posts in this category

Facing the complexities of application modernization? The Strangler Fig pattern provides a strategic and controlled approach to incrementally update l...

Cloud computing's transformative impact necessitates a proactive approach to security. This article outlines the core principles of "secure by design"...

Navigating the benefits of a multi-cloud architecture requires careful consideration of significant challenges, including complexities in management,...
This comprehensive guide explores the Retry Pattern with Exponential Backoff, a crucial strategy for building resilient and fault-tolerant systems. Fr...
Infrastructure as Code (IaC) transforms infrastructure management by enabling automated provisioning and configuration. This approach replaces manual...
This article delves into the 'analysis paralysis' anti-pattern, a common pitfall in project planning that can severely impact timelines, budgets, and...

This article offers a practical roadmap for seamlessly integrating Artificial Intelligence (AI) services into your existing applications, unlocking en...
Cloud architecture demands a strategic approach to ensure optimal performance and efficiency. This guide outlines key principles for designing, optimi...
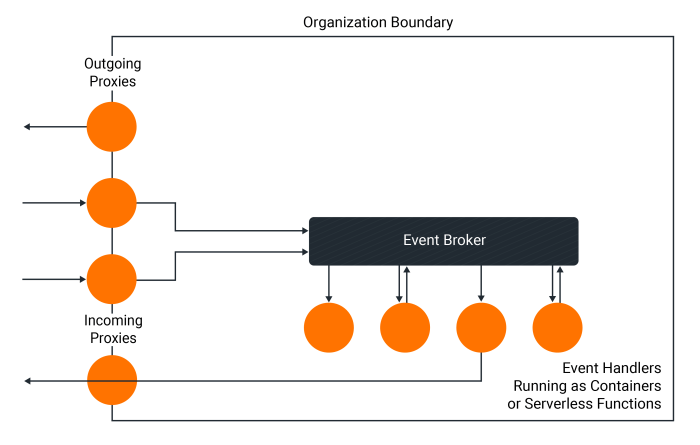
This article provides a comprehensive guide to designing event-driven architectures (EDAs) in the cloud, a paradigm shift for building dynamic and res...

Automation plays a critical role in modern cloud architecture, significantly streamlining tasks and orchestrating complex workflows. This article expl...
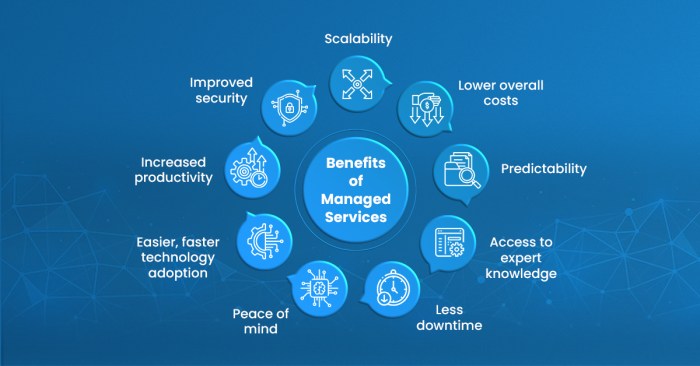
Discover how managed database services are transforming data management for businesses. This approach offers significant advantages over self-managed...

Hexagonal architecture leverages ports and adapters to isolate the core application logic from external concerns. This design pattern enhances softwar...